GUEST ESSAY: Privacy risks introduced by the ‘metaverse’ — and how to combat them
The Last Watchdog
OCTOBER 10, 2022
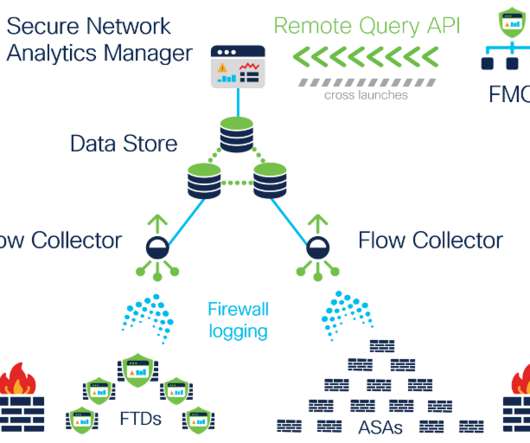
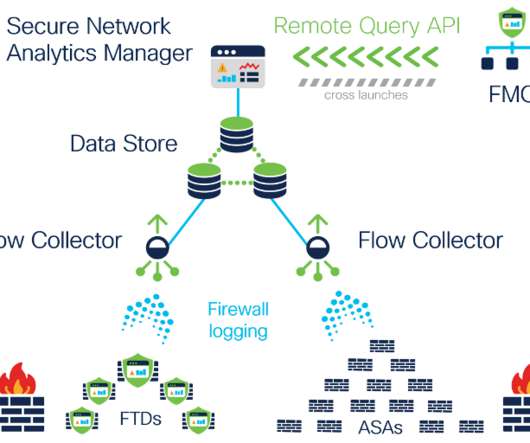
To test the true extent of data collection in VR, we designed a simple 30-person user study called MetaData. In a follow-up work, called “ MetaGuard ,” we present a promising solution to our VR data privacy woes. But until recently, the VR privacy threat has remained entirely theoretical.
















































Let's personalize your content