Introducing continuous remote worker visibility and expanded data collection with Secure Network Analytics Release 7.3.2
Cisco Security
JUNE 1, 2021
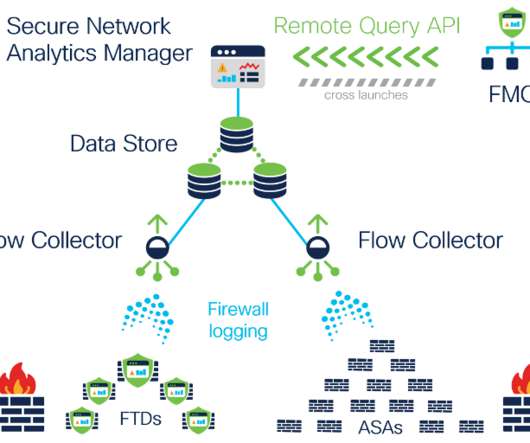
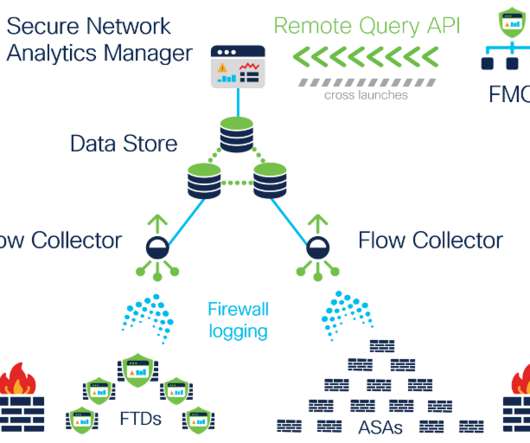
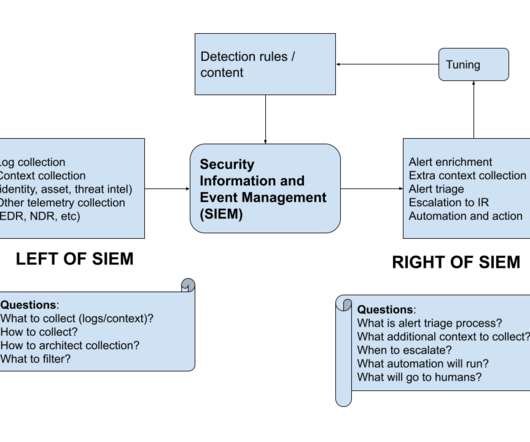
Preamble: The great network visibility blackout of 2020. Expanded data collection to provide further extended visibility and enhanced context . A graphical depiction of the Security Logging and Analytics On-premises Architecture. With release 7.3.2, The Cisco Telemetry Broker .





















Let's personalize your content