New LightSpy spyware variant comes with enhanced data collection features targeting social media platforms
Security Affairs
FEBRUARY 26, 2025
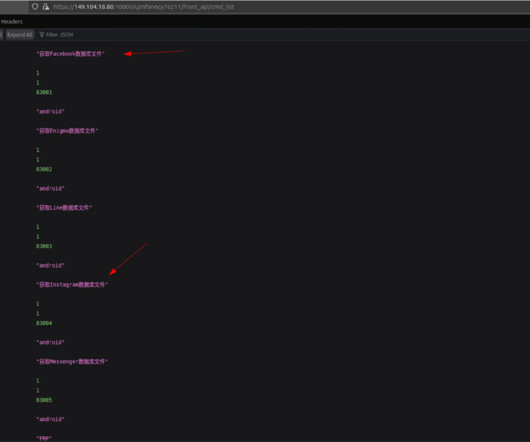
Researchers found an updated LightSpy spyware with enhanced data collection features targeting social media platforms like Facebook and Instagram. have found an updated version of the LightSpy spyware that supports an expanded set of data collection features to target social media platforms like Facebook and Instagram.























Let's personalize your content