Modern Strategies to Address Phishing Risks with Advanced Technology
SecureWorld News
AUGUST 9, 2024
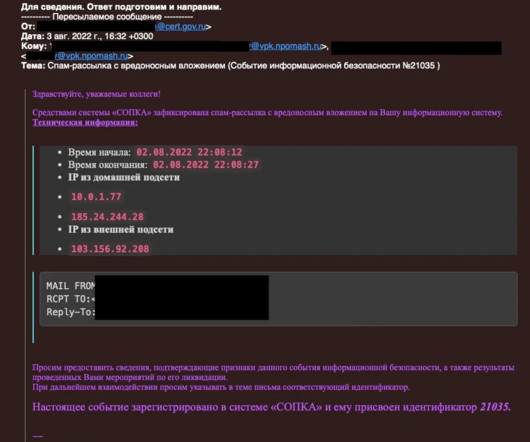
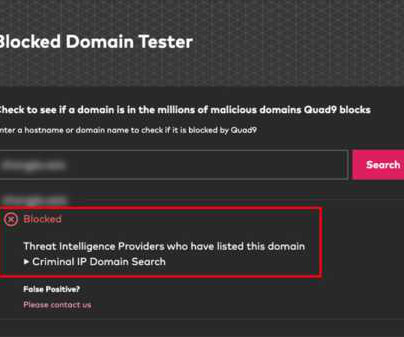
In today's digital age, phishing has evolved into a sophisticated threat capable of deceiving even the most technically savvy individuals. No longer confined to suspicious emails, phishing now encompasses voice-based attacks (vishing), text-based scams (smishing) automated with phishing kits, and deepfake technologies.

















































Let's personalize your content