U.S. Confirms Chinese Hackers Compromised Telecommunications Networks
SecureWorld News
NOVEMBER 15, 2024
telecommunications infrastructure. We have identified that PRC-affiliated actors have compromised networks at multiple telecommunications companies to enable the theft of customer call records data," CISA and the FBI explained in the joint release. The compromised data also included information acquired by U.S.



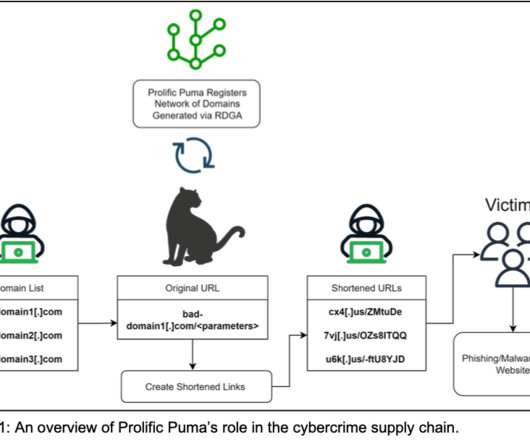
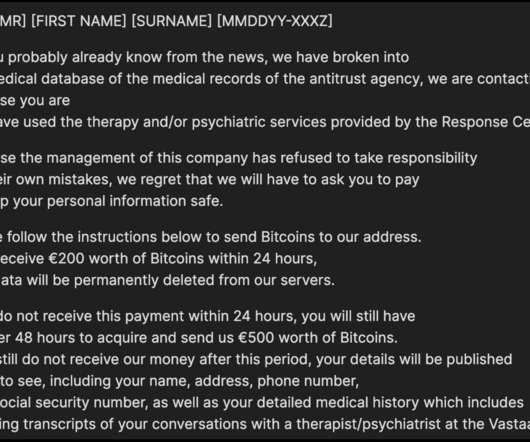
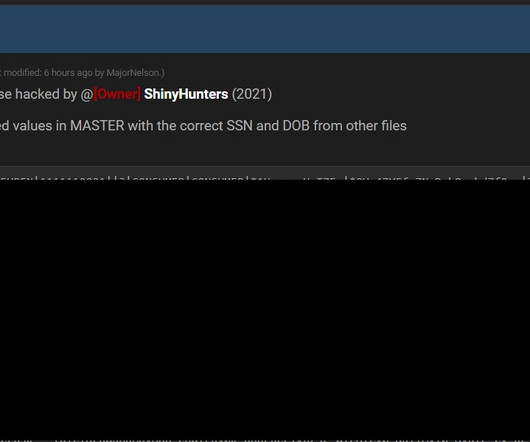








Let's personalize your content