Infoblox Exposes $5.7B Investment Scam Surge Fueled by RDGAs and DNS Abuse
Penetration Testing
APRIL 29, 2025
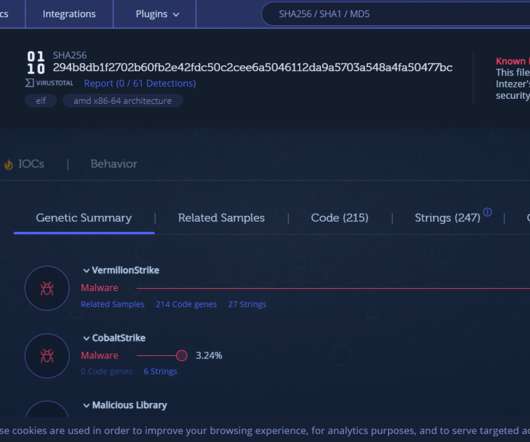
Investment Scam Surge Fueled by RDGAs and DNS Abuse appeared first on Daily CyberSecurity. In a revealing new report, Infoblox Threat Intelligence warns that investment scams are evolving rapidlycontributing to record-breaking consumer The post Infoblox Exposes $5.7B



















Let's personalize your content