German Police Raid DDoS-Friendly Host ‘FlyHosting’
Krebs on Security
MARCH 31, 2023
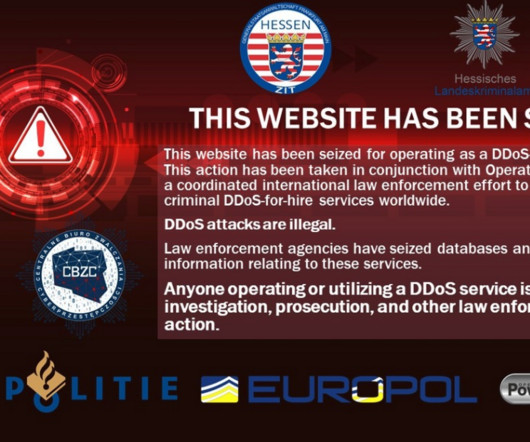
Authorities in Germany this week seized Internet servers that powered FlyHosting , a dark web offering that catered to cybercriminals operating DDoS-for-hire services, KrebsOnSecurity has learned. “Police says: They support ddos attacks, C&C/C2 and stresser a bit too much. A seizure notice left on the FlyHosting domains. .











Let's personalize your content