Risks in Telecommunications IT
Trend Micro
JULY 29, 2021
We summarize the characteristics, threats, and recommendations to improve the security posture of enterprises' and telecommunications companies' IT infrastructure.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Trend Micro
JULY 29, 2021
We summarize the characteristics, threats, and recommendations to improve the security posture of enterprises' and telecommunications companies' IT infrastructure.

Tech Republic Security
JANUARY 2, 2025
Threat actors entered Treasury Department systems through BeyondTrust. The breach may be related to the Salt Typhoon attacks reported throughout the year.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Approachable Cyber Threats
MARCH 9, 2023
Category Awareness, News, Case Study As one of the world’s fastest-growing industries, telecommunication has become a highly vulnerable target for cybersecurity threats. In short, telecommunications (telecom) is a fundamental and critical component of our global infrastructure. Why are Telecom Sectors Targeted?

The Last Watchdog
JANUARY 7, 2025
By leveraging advanced behavioral analysis, CyTwist Profiler identifies new and emerging threats in real time, stopping attackers before they can cause harm. Advanced detection CyTwist recently demonstrated its advanced detection capabilities during a red team simulation with a major telecommunications provider.

IT Security Guru
DECEMBER 1, 2022
Furthermore, the Armed Forces run awareness campaigns to instruct their personnel about cyber threats and what measures authorized users may take to mitigate threats to military information systems and their vulnerabilities. The importance of cybersecurity awareness training. He is also a writer for Bora.

Schneier on Security
JULY 24, 2019
If the choice is between a world where we can achieve a 99 percent assurance against cyber threats to consumers, while still providing law enforcement 80 percent of the access it might seek; or a world, on the other hand, where we have boosted our cybersecurity to 99.5 That telecommunications company was GTEwhich became Verizon.

Schneier on Security
AUGUST 14, 2019
If the choice is between a world where we can achieve a 99 percent assurance against cyber threats to consumers, while still providing law enforcement 80 percent of the access it might seek; or a world, on the other hand, where we have boosted our cybersecurity to 99.5 That telecommunications company was GTE -- which became Verizon.

CyberSecurity Insiders
JUNE 8, 2022
United States Cybersecurity and Infrastructure Security Agency (CISA) have issued an advisory to all telecom and network operators in the United States asking them to be vigilant against state sponsored cyber attacks from China.

Approachable Cyber Threats
MARCH 9, 2023
Category Awareness, News, Case Study As one of the world’s fastest-growing industries, telecommunication has become a highly vulnerable target for cybersecurity threats. In short, telecommunications (telecom) is a fundamental and critical component of our global infrastructure. Why are Telecom Sectors Targeted?

SecureWorld News
FEBRUARY 12, 2025
The Honourable David McGuinty, Minister of Public Safety, on February 6th unveiled Canada's National Cyber Security Strategy (NCSS), a long-term plan to protect Canadians, businesses, and critical infrastructure from an increasingly complex cyber threat landscape.

Thales Cloud Protection & Licensing
JULY 21, 2022
The Ongoing Cyber Threat to Critical Infrastructure. With that in mind, Thales has launched the 2022 Thales Data Threat Report Critical Infrastructure Edition, which includes responses from 300 security leaders and practitioners within critical infrastructure organizations. Thu, 07/21/2022 - 12:28.

Security Boulevard
JUNE 21, 2021
RedFoxtrot cyber threat group, which is believed to have links with the Chinese military, has been targeting Indian organizations since becoming active in 2014. This hacker group has particularly focussed on targeting Indian institutions ranging from defense, telecommunications, mining, and research.

Digital Shadows
NOVEMBER 1, 2022
As we move towards the end of 2022, now is the time to take a look back at the major trends from the last eleven months and identify what might happen from a cyber threat perspective in 2023. A key for analysts is to remain flexible and not compartmentalize cyber threats.

CyberSecurity Insiders
MARCH 4, 2021
At 11:11 am NSE announced that it was closing the financial system for the day because of the slow network that could have been because of a telecommunication glitch out of which MTNL is a backbone for conducting most of the network operations and communications.

CyberSecurity Insiders
JUNE 28, 2022
Kaspersky, the Russian originated Cybersecurity firm has discovered in its latest studies that cyber crooks are targeting Industrial Control Systems (ICS) operating in Asia and targeting companies operating in logistics, transportation, telecom and airlines sectors operating in Afghanistan, India, Pakistan and Malaysian regions.

eSecurity Planet
SEPTEMBER 21, 2024
Understanding and adhering to cybersecurity regulations is crucial for any organization as cyber threats evolve and become more sophisticated. Cybersecurity laws and regulations encompass a range of legal requirements designed to protect information systems and data from cyber threats.
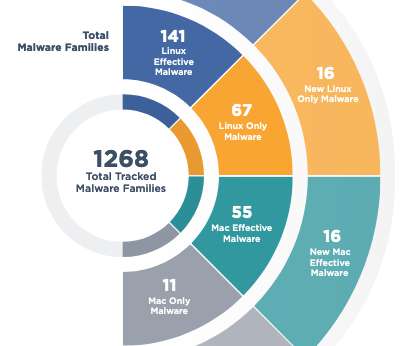
Security Affairs
FEBRUARY 24, 2020
.” Mandiant experts named the China-linked APT41 threat actor as one of the most prolific cyber threat group. The group hit entities in several industries, including the gaming, healthcare, high-tech, higher education, telecommunications, and travel services industries.

Thales Cloud Protection & Licensing
APRIL 24, 2024
They will also have the opportunity to enjoy one-on-one conversations with both Thales and Imperva experts to help them remain ahead of today's cyber threats. Quantum Computing for Telecommunications Also, on May 8, a panel will be on “ Quantum Computing for Telecommunications.”

Cisco Security
NOVEMBER 18, 2022
The telecommunications infrastructure that carries internet traffic between countries and continents is often provided by submarine cables. The British Chief of Defense Staff has warned how seriously intentional damage to telecommunications cables would be taken [2]. . Physical infrastructure can not be taken for granted.

Security Affairs
OCTOBER 29, 2021
“To counter this threat, it is imperative that 5G cloud infrastructures be built and configured securely, with capabilities in place to detect and respond to threats, providing a hardened environment for deploying secure network functions.

Security Boulevard
DECEMBER 9, 2024
This massive DDoS attack targeted a telecommunications service provider, one of NSFOCUSs global clients. The telecommunications industry frequently faces such cyber threats. a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.

CyberSecurity Insiders
APRIL 12, 2023
The report stems from a detailed analysis of attacks targeting StormWall’s clientele, which spans various sectors such as finance, e-commerce, telecommunications, entertainment, transportation, education, and logistics. Telecommunications continued to be a popular target, enduring 16% of attacks and a 47% YoY increase.

SecureWorld News
OCTOBER 30, 2024
Cybersecurity and Infrastructure Security Agency (CISA) has taken a significant step forward by introducing its first international strategic plan in an effort to help contain cyber threats that continue to transcend national borders. Depends Recognizing that much of U.S.

Heimadal Security
APRIL 6, 2021
According to a Cyber Threat Report released by the Bangladesh Government’s e-Government Computer Incident Response Team (BGD e-GOV CIRT) on April 1st, hacker group Hafnium has launched attacks on more than 200 organizations in Bangladesh.

Security Boulevard
FEBRUARY 27, 2025
As the CTO of a telecommunications company said to me, HYAS doesnt just find the needle in the haystack, you find the needle in the stack of needles. The Challenge: An Avalanche of Threats Imagine having to defend against 56 billion unique attacks every three months.
Security Affairs
DECEMBER 11, 2020
This means that in addition to the traditional telecommunications business, the company is increasingly attentive to sectors like the cloud, the Internet of Things and cybersecurity. Redazione SA: What do you think has led to what is today an impressive increase in cyber threats?

SecureWorld News
AUGUST 28, 2023
Of particular note is their willingness to pay exorbitant fees for access to telecommunications providers' platforms, enabling them to hijack phone numbers and gain access to accounts via SMS one-time passcodes. The group's activities extended from 2021 to 2022 and involved individuals from both the U.K. and Brazil.

Security Affairs
DECEMBER 24, 2019
“The purpose of the task is to ensure the reliable operation of the Internet in Russia in any conditions and under any circumstances,” said Aleksei Sokolov, deputy communications minister, in televised remarks on December 23 from the Monitoring and Cyber Threat Response Center.”

Malwarebytes
OCTOBER 13, 2022
The US and other allied nations consider China a cyber threat as it continues to target and attack companies in the US and elsewhere, with the primary aim of stealing intellectual property or gaining access to sensitive networks.

Security Affairs
MARCH 26, 2023
NCA infiltrates the cybercriminal underground with fake DDoS-for-hire sites Pwn2Own Vancouver 2023 awarded $1,035,000 and a Tesla for 27 0-days CISA announced the Pre-Ransomware Notifications initiative China-linked hackers target telecommunication providers in the Middle East City of Toronto is one of the victims hacked by Clop gang using GoAnywhere (..)

SecureWorld News
MAY 25, 2023
Since the targets span several industries and sectors, among them telecommunications, transportation, the military, and emergency response, this could be part of a Chinese operation to map out the paths a potential American response to an invasion of Taiwan would take. China's cyber threat landscape presents a distinct challenge.

CyberSecurity Insiders
JANUARY 19, 2022
NetAbstraction will host an industry event on March 2nd at the Georgia Cyber Center to discuss the cyber threats facing both the government and private sector. It was founded by a team that built clandestine telecommunication networks for the NSA and CIA.

Security Boulevard
DECEMBER 20, 2023
In the field of cybersecurity, a potent and covert threat called Krasue has surfaced. This remote access trojan has been silently infiltrating Linux systems, primarily targeting telecommunications companies since 2021.

Centraleyes
DECEMBER 5, 2024
This incident serves as a stark reminder of the vulnerabilities in our telecommunications networks, which are fundamental to everything from personal communication to national security. As cyber threats from nation-state actors become more complex, the need for stronger, more proactive cybersecurity measures has never been clearer.

SecureWorld News
JUNE 18, 2023
Gaming (58.7%) and telecommunications (47.7%) had the highest bad bot traffic on their websites and applications. Bad bots at work One cyber threat that targets user accounts on digital platforms is a credential stuffing attack. Taking the lead were Germany with 68.6%, Ireland with 45.1%, and Singapore with 43.1%.

IT Security Guru
JULY 28, 2023
Not only large enterprises but small and medium-sized businesses (SMBs) should realise the threat size, its origin, exogenous or from their inner circle , and the potential impact on their assets. Implementing an effective data loss prevention (DLP) strategy to mitigate these cyber threats and safeguard critical data is imperative.

Pen Test Partners
FEBRUARY 22, 2024
This is a pivotal moment for manufacturers, importers, and distributors, imposing new compliance measures to safeguard against cyber threats. Its detailed regulations were established in September 2023 and aim to improve the security standards of smart products. What does non-compliance look like? You can read the Act here.

SC Magazine
JUNE 16, 2021
Major health care groups telecommunications companies and law enforcement organizations have also anonymously reviewed the framework, Grace-McMinn noted. Michael Daniel, CEO of the Cyber Threat Alliance, said that the formation of new threat frameworks comes with pros and cons. “As

Security Boulevard
JUNE 26, 2023
Different states have their own laws and statutes regulating the definition and disclosure of data breaches, so it is important for organizations to be aware of these standards in the event they are party to any type of cyber security incident. Every organization is, to varying degrees, potentially at risk of experiencing a data breach.

CyberSecurity Insiders
NOVEMBER 26, 2021
SolarWinds is one example of a threat actor finding a way to compromise one company and leveraging that attack to allow them to compromise the customers of the initial target. Threat actors gained access to telecommunications providers, which then enabled them to access and monitor communications for customers of those providers.

Jane Frankland
JUNE 25, 2024
According to Intel, the Intel® Xeon® 6 processors have enabled telecommunication companies to manage increasing data traffic seamlessly while maintaining low latency and high reliability. As cyber threats become increasingly destructive and sophisticated, the role of AI in cybersecurity becomes even more critical.

CyberSecurity Insiders
JUNE 15, 2023
The NFV architecture, standardized by the European Telecommunications Standards Institute (ETSI), provides a blueprint for implementing and deploying NFV solutions. By consolidating multiple network functions onto shared infrastructure, NFV lowers energy usage and cooling requirements.
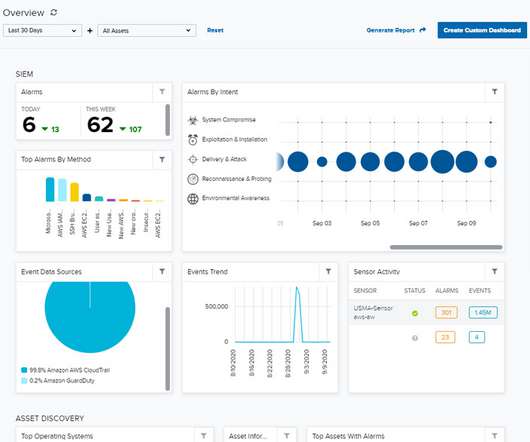
eSecurity Planet
FEBRUARY 9, 2022
According to Jay McBain, an analyst at Forrester Research, spending on IT and telecommunications will be worth about $7 trillion by 2030. The research shows that cyber threats like ransomware have become a top priority for business executives and boards of directors,” said Jon Oltsik, an analyst with ESG. Competition is fierce.

Spinone
DECEMBER 26, 2018
VoIP phishing and impersonation also victimized millions of corporate employees across the world , contributing to an even greater cyber threat. Cloud security success and choosing the right investments is all about having a clear understanding of threat types and their resulting damages.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content