Why is Threat Detection Hard?
Anton on Security
OCTOBER 7, 2020
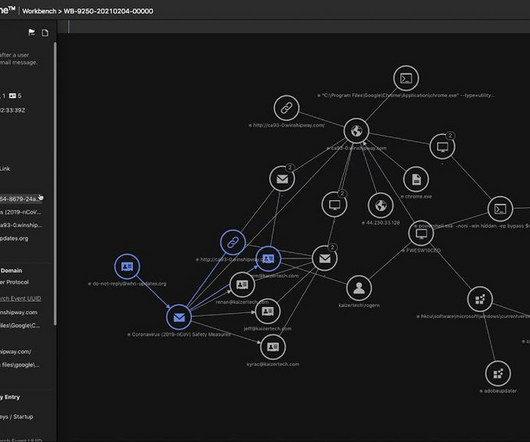
While creating a recent presentation, I needed a slide on “threat detection is hard.” And it got me thinking, why is threat detection so hard for so many organizations today? This means we are “celebrating” ~35 years of cyber threat detection. This does make detection even harder. Action items?









































Let's personalize your content