Risks in Telecommunications IT
Trend Micro
JULY 29, 2021
We summarize the characteristics, threats, and recommendations to improve the security posture of enterprises' and telecommunications companies' IT infrastructure.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Trend Micro
JULY 29, 2021
We summarize the characteristics, threats, and recommendations to improve the security posture of enterprises' and telecommunications companies' IT infrastructure.

Security Affairs
DECEMBER 4, 2024
The government agencies released a guide that advises telecom and critical infrastructure defenders on best practices to strengthen network security against PRC-linked and other cyber threats. The agencies recommend robust measures to protect enterprise networks against cyber threats. ” reads the joint advisory.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Approachable Cyber Threats
MARCH 9, 2023
Category Awareness, News, Case Study As one of the world’s fastest-growing industries, telecommunication has become a highly vulnerable target for cybersecurity threats. In short, telecommunications (telecom) is a fundamental and critical component of our global infrastructure. Why are Telecom Sectors Targeted?

The Last Watchdog
JANUARY 7, 2025
This incident highlights three key risks of AI-driven attacks: Sophistication: AI allows attacks to evolve in real-time, rendering static defenses obsolete. By leveraging advanced behavioral analysis, CyTwist Profiler identifies new and emerging threats in real time, stopping attackers before they can cause harm.

Schneier on Security
JULY 24, 2019
But, in the world of cybersecurity, we do not deal in absolute guarantees but in relative risks. All systems fall short of optimality and have some residual risk of vulnerability a point which the tech community acknowledges when they propose that law enforcement can satisfy its requirements by exploiting vulnerabilities in their products.

Schneier on Security
AUGUST 14, 2019
But, in the world of cybersecurity, we do not deal in absolute guarantees but in relative risks. All systems fall short of optimality and have some residual risk of vulnerability -- a point which the tech community acknowledges when they propose that law enforcement can satisfy its requirements by exploiting vulnerabilities in their products.

IT Security Guru
DECEMBER 1, 2022
After all, cybersecurity is a matter of proper human risk management. Several reports, such as the World Economic Forum Global Risk Report 2022 and Verizon’s 2022 Data Breach Investigations Report highlight that human error is by far the biggest and dominant cause of illicit actions and cybersecurity issues. Reduce human risk.

Cisco Security
NOVEMBER 18, 2022
Often security researchers and security teams focus on threats to software and the risks associated with authenticating and managing users. Each layer within the stack is exposed to specific threats which need to be considered as part of a cyber security strategy. Physical infrastructure can not be taken for granted.

SecureWorld News
FEBRUARY 12, 2025
The Honourable David McGuinty, Minister of Public Safety, on February 6th unveiled Canada's National Cyber Security Strategy (NCSS), a long-term plan to protect Canadians, businesses, and critical infrastructure from an increasingly complex cyber threat landscape.

Approachable Cyber Threats
MARCH 9, 2023
Category Awareness, News, Case Study As one of the world’s fastest-growing industries, telecommunication has become a highly vulnerable target for cybersecurity threats. In short, telecommunications (telecom) is a fundamental and critical component of our global infrastructure. Why are Telecom Sectors Targeted?
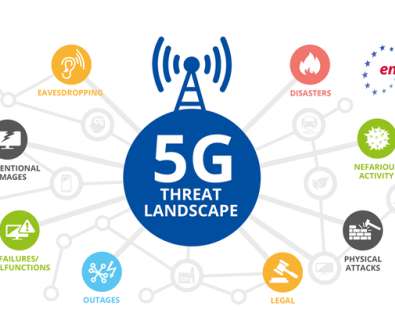
Security Affairs
NOVEMBER 21, 2019
ENISA, the European Union Agency for Cybersecurity publishes a Threat Landscape for 5G Networks, assessing the threats related to the fifth generation of mobile telecommunications networks (5G). An EU-wide Coordinated Risk Assessment of 5G networks has been published on the 9 th October 2019. Next Steps.

eSecurity Planet
SEPTEMBER 21, 2024
Understanding and adhering to cybersecurity regulations is crucial for any organization as cyber threats evolve and become more sophisticated. Let’s explore what to expect from the upcoming regulations, provide insights into critical federal and state laws, and offer practical compliance and risk management strategies.

Thales Cloud Protection & Licensing
JULY 21, 2022
The Ongoing Cyber Threat to Critical Infrastructure. With that in mind, Thales has launched the 2022 Thales Data Threat Report Critical Infrastructure Edition, which includes responses from 300 security leaders and practitioners within critical infrastructure organizations. Thu, 07/21/2022 - 12:28.

Digital Shadows
NOVEMBER 1, 2022
As we move towards the end of 2022, now is the time to take a look back at the major trends from the last eleven months and identify what might happen from a cyber threat perspective in 2023. A key for analysts is to remain flexible and not compartmentalize cyber threats.

SecureWorld News
OCTOBER 30, 2024
Cybersecurity and Infrastructure Security Agency (CISA) has taken a significant step forward by introducing its first international strategic plan in an effort to help contain cyber threats that continue to transcend national borders. Increase awareness to detect, deter, and disrupt emerging threats and hazards 4.

Security Affairs
OCTOBER 29, 2021
“To counter this threat, it is imperative that 5G cloud infrastructures be built and configured securely, with capabilities in place to detect and respond to threats, providing a hardened environment for deploying secure network functions.

Thales Cloud Protection & Licensing
APRIL 24, 2024
They will also have the opportunity to enjoy one-on-one conversations with both Thales and Imperva experts to help them remain ahead of today's cyber threats. They will also learn best practices for effective risk mitigation and explore the complex challenges posed by securing the modern, highly connected supply chain.
Security Affairs
DECEMBER 11, 2020
This means that in addition to the traditional telecommunications business, the company is increasingly attentive to sectors like the cloud, the Internet of Things and cybersecurity. Redazione SA: What do you think has led to what is today an impressive increase in cyber threats? Pierluigi Paganini.

CyberSecurity Insiders
APRIL 12, 2023
The report stems from a detailed analysis of attacks targeting StormWall’s clientele, which spans various sectors such as finance, e-commerce, telecommunications, entertainment, transportation, education, and logistics. Telecommunications continued to be a popular target, enduring 16% of attacks and a 47% YoY increase.

SecureWorld News
NOVEMBER 21, 2024
However, its rapid adoption introduces new risks, requiring businesses to balance opportunities with challenges. A 2024 study by Bell, Canada's largest telecommunications company, surveyed 600 Canadian business leaders and IT professionals to explore the evolving role of GenAI.

Security Boulevard
FEBRUARY 27, 2025
As the CTO of a telecommunications company said to me, HYAS doesnt just find the needle in the haystack, you find the needle in the stack of needles. The Challenge: An Avalanche of Threats Imagine having to defend against 56 billion unique attacks every three months.

CyberSecurity Insiders
OCTOBER 28, 2021
A recent study by telecommunications provider, TextAnywhere, looked into the screen habits of 1,000 employees in the UK and revealed that over two-thirds (67.4%) are using their mobiles for work, imposing a serious threat to business security. . For a full look at the research, see here.

Spinone
DECEMBER 26, 2018
In this article we will learn how to address and effectively respond to major enterprise cybersecurity threats and provide tips to mitigate IT security risk. VoIP phishing and impersonation also victimized millions of corporate employees across the world , contributing to an even greater cyber threat.

CyberSecurity Insiders
NOVEMBER 26, 2021
Looking ahead to what Cybereason and our customers need to be aware of for 2022, it’s important to keep those things in mind, but let us consider the broader threat landscape—and what we are seeing in terms of emerging attacks and current threat research—to identify key risks that defenders need to prepare for.

Security Affairs
DECEMBER 24, 2019
“The purpose of the task is to ensure the reliable operation of the Internet in Russia in any conditions and under any circumstances,” said Aleksei Sokolov, deputy communications minister, in televised remarks on December 23 from the Monitoring and Cyber Threat Response Center.”

IT Security Guru
JULY 28, 2023
In today’s digital age, every business, no matter its size, faces increasing cybersecurity threats, including the risk of data loss that can have severe consequences, ranging from financial losses – with annual costs of $10.5 trillion in 2025 – to disrupted operations and reputational damage.

SecureWorld News
MAY 25, 2023
Since the targets span several industries and sectors, among them telecommunications, transportation, the military, and emergency response, this could be part of a Chinese operation to map out the paths a potential American response to an invasion of Taiwan would take. China's cyber threat landscape presents a distinct challenge.

SecureWorld News
MARCH 10, 2022
Many threats that have until now been theoretical—like creation of a "Ru-net" as an alternative to the Internet—are becoming a reality. Is it better to cut off Russia or allow free communication, with all the risks and benefits it provides? Tech firms are making very hard decisions. It is not by any means exhaustive.

SecureWorld News
JUNE 18, 2023
Over the past few years, bots have emerged as a new cybersecurity threat, as they can be manipulated for malicious purposes. This article will explore the realm of malicious bots, uncover their cybersecurity risks, and provide valuable insights on safeguarding yourself from bot attacks. Stats on bots 1.

Centraleyes
DECEMBER 5, 2024
It is likely that new legislation will soon be on the table, focusing on stricter encryption requirements, third-party risk management, and tougher penalties for lapses in securing critical infrastructure.

Pen Test Partners
FEBRUARY 22, 2024
This is a pivotal moment for manufacturers, importers, and distributors, imposing new compliance measures to safeguard against cyber threats. Such policies are crucial for a collaborative security posture, encouraging responsible vulnerability disclosure and ensuring that manufacturers can promptly address and mitigate risks.

Security Boulevard
JUNE 26, 2023
In this article, we will dive deep into different types of data breaches , how organizations can mitigate their risk of falling victim to a breach, and what industries face the highest risk of falling victim to a cyber security attack. Every organization is, to varying degrees, potentially at risk of experiencing a data breach.

SC Magazine
JUNE 16, 2021
Major health care groups telecommunications companies and law enforcement organizations have also anonymously reviewed the framework, Grace-McMinn noted. Michael Daniel, CEO of the Cyber Threat Alliance, said that the formation of new threat frameworks comes with pros and cons. “As

Thales Cloud Protection & Licensing
NOVEMBER 28, 2022
The current geopolitical climate has heightened the risk of cyberattacks, particularly for operators of key services that could be targets of hybrid warfare. In 2020, the European Commission revised the Directive, to “further strengthen overall cybersecurity in the Union” to address emerging cyber threats. Supply chain security.

CyberSecurity Insiders
JUNE 15, 2023
This simplifies the deployment and management of network services, improves efficiency, and minimizes the risk of errors. The NFV architecture, standardized by the European Telecommunications Standards Institute (ETSI), provides a blueprint for implementing and deploying NFV solutions.

eSecurity Planet
JUNE 10, 2024
Last week’s vulnerability news revealed a significant increase in serious flaws targeted by cyber threat actors across multiple large platforms. The fix: To prevent the risk, federal agencies and companies that use Oracle WebLogic Server should apply the most recent fixes before June 24, 2024.

Centraleyes
OCTOBER 31, 2024
Its relevance extends to sectors including IT, security, telecommunications, and others handling confidential data that could impact national and public security. The policy framework has undergone numerous updates, with each version refining security measures to keep up with emerging threats. Version 5.9.5 Compliance with CJIS v5.9.5

Centraleyes
AUGUST 1, 2024
The goal is to transition from cumbersome manual methods to a more efficient, automated system that enhances your compliance efforts and boosts your cyber risk management. By adopting the right tools, you can ensure continuous compliance, proactive risk management, and a robust defense against cyber threats.
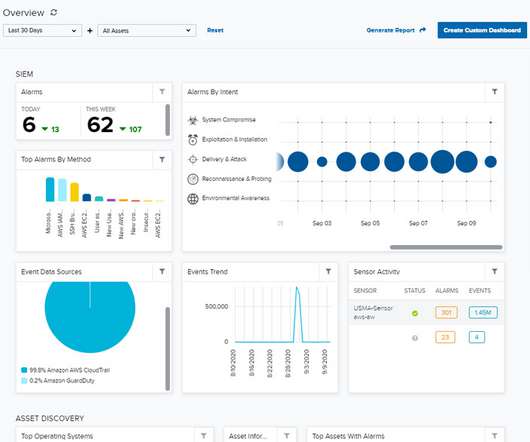
eSecurity Planet
FEBRUARY 9, 2022
According to Jay McBain, an analyst at Forrester Research, spending on IT and telecommunications will be worth about $7 trillion by 2030. The research shows that cyber threats like ransomware have become a top priority for business executives and boards of directors,” said Jon Oltsik, an analyst with ESG. Competition is fierce.

Thales Cloud Protection & Licensing
OCTOBER 10, 2022
Both the renewable energy business and the telecommunications industry are projected to expand significantly over the next decade, and the green energy movement is gaining traction. Protecting 5G from cyber threats. The benefits of 5G connectivity. Clean energy.

eSecurity Planet
JANUARY 28, 2021
Darktrace – Threat detection. Darktrace‘s Cyber artificial intelligence (AI) platform detects and fights cyber threats in real-time. The product increases automation security surrounding development to reduce risk. Cybereason also made eSecurity Planet ‘s list of top EDR solutions.
eSecurity Planet
MARCH 7, 2023
The downside of ISSAF is that it is no longer updated, and keeping up to date is critical in an ever-evolving cyber threat landscape. Pros and Cons of Penetration Testing Like all security solutions and approaches, penetration tests have benefits, risks, and challenges.

The Security Ledger
SEPTEMBER 18, 2019
We talk about the growing demand for security automation tools and how the chronic cyber security talent shortage in North America and. Advances in the use of polymers revolutionized everything from food packaging to electronics, telecommunication and medicine. Read the whole entry. »

CyberSecurity Insiders
SEPTEMBER 21, 2021
Establish a session inactivity timeout as short as possible, based on balancing risk and business functional requirements. Different cryptographic approaches, such as symmetric-key cryptography or public-key cryptography, can be deployed throughout the transfer of information and storage depending on the security demands and risks present.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content