Protect Your Business With This Seamless Firewall — Now $150 Off
Tech Republic Security
MARCH 27, 2024
DNS FireWall is an intuitive security app built to protect you and your business from malware, phishing, botnets and more security threats.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Security Affairs
JANUARY 28, 2020
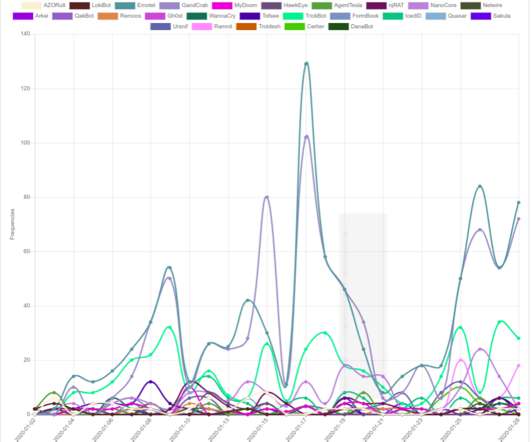
Marco Ramilli published the Cyber Threat Trends Dashbo a rd , a useful tool that will allow us to better understand most active threats in real time. Thanks to “infosharing” activities it is possible to block or, in specific cases, to prevent cyber attacks. Malware Families Trends. Malware Families.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

CyberSecurity Insiders
MARCH 25, 2021
Cyber Threats have increased on enterprise networks and all thanks to the latest trend of work from home that is being practiced by most of the firms operating across the globe to prevent the spread of Corona Virus. The post Work from home increases Cyber Threats on Enterprises appeared first on Cybersecurity Insiders.

IT Security Guru
MARCH 14, 2025
We speak with Sierra Six, a leading SEO agency in Essex to get their recommendations on the best plugins for security and to reduce cyber attacks. It provides a firewall that blocks malicious traffic before it reaches your website. It also has a malware scanner that checks your site for viruses and suspicious code.

Digital Shadows
MARCH 12, 2025
Lets dive into the key findings from this period and explore how organizations in this sector can strengthen their defenses against rising cyber threats. Proactively patching vulnerabilities and securing web applications with firewalls and secure coding practices are also crucial steps.

CyberSecurity Insiders
JUNE 2, 2023
In practice, however, air-gapping an OT system or firewalling its protected network is only the beginning of hardening its overall security. OT Attacks Are on the Rise Whether for geopolitical purposes or to collect a ransom, disrupting or threatening the performance of OT systems can be a huge win for threat actors. Great in theory.

CyberSecurity Insiders
DECEMBER 27, 2021
If you are in thinking that your PC or computing device is secure enough as it is loaded with an anti-malware solution, you better change your viewpoint. As some hackers have developed a malware that uses code signing certificates to avoid detection by security defenses and has the tendency to download payloads onto a compromised system.

Security Affairs
NOVEMBER 17, 2024
CISA adds Palo Alto Networks Expedition bugs to its Known Exploited Vulnerabilities catalog Hackers target critical flaw CVE-2024-10914 in EOL D-Link NAS Devices China-linked threat actors compromised multiple telecos and spied on a limited number of U.S.

IT Security Guru
DECEMBER 1, 2022
Furthermore, the Armed Forces run awareness campaigns to instruct their personnel about cyber threats and what measures authorized users may take to mitigate threats to military information systems and their vulnerabilities. These training programs imitate cyberattacks and educate people about existing malware.

SecureWorld News
JANUARY 21, 2025
Keeping pests out of your home and keeping cyber threats out of your organization might seem worlds apart, but there are surprising parallels between the two. This consistent, proactive approach keeps threats at bay before they become a costly problem. About Pestie: I swear by it and am nearing the end of year two as a customer.

Krebs on Security
APRIL 13, 2022
Nine of the updates pushed this week address problems Microsoft considers “critical,” meaning the flaws they fix could be abused by malware or malcontents to seize total, remote access to a Windows system without any help from the user. . “Go patch your systems before that situation changes.”. 10 being the worst). .”

eSecurity Planet
FEBRUARY 6, 2024
A host-based firewall is installed directly on individual networked devices to filter network traffic on a single device by inspecting both incoming and outgoing data. Larger enterprises use this to manage the spread of malware throughout a network in the event that one device is infected.

The Last Watchdog
DECEMBER 13, 2020
Gartner refers to this as the Secure Access Service Edge (SASE), which is a framework combining the functionality of Wide Area Network (WAN) with network security services to shield against any cyber threats or cloud-enabled SaaS. The cyber threats landscape. SASE is a sophisticated response to a complex, dynamic threat.

eSecurity Planet
AUGUST 29, 2023
Firewall-as-a-Service (FWaaS) offers firewall capabilities as a cloud-based service. Traditional firewalls protect the network perimeter, enforcing security standards by regulating incoming and outgoing traffic according to rules and traffic analysis.

eSecurity Planet
OCTOBER 24, 2023
Malware attacks pose a significant risk to both individuals and businesses, infiltrating computer systems, compromising sensitive data and disrupting operations, leading to financial and data loss — and even extortion. Here are 15 important controls and best practices for preventing malware.

Security Boulevard
MAY 6, 2021
The most important and integral part of any data security begins with having firewalls installed in the environment. Not just that, installing firewalls is an essential requirement of the Payment Card Industry Data Security Standard (PCI DSS ). What is a PCI DSS Compliant Firewall? Protect cardholder data with a firewall.

SecureBlitz
MAY 20, 2021
Want to secure your computer against cyber threats? The post How To Secure Your Computer Against Cyber Threats Like 007 appeared first on SecureBlitz Cybersecurity. I will show you how to do just that in this post. Then, I had to format my PC and lost some important files and.

eSecurity Planet
FEBRUARY 17, 2023
Threat hunting starts with a pretty paranoid premise: That your network may have already been breached and threat actors may be inside waiting for an opportunity to strike. This data is based on common attributes where cyber threat hunters can efficiently identify suspicious activity, making the threat hunting process more manageable.

SC Magazine
JUNE 10, 2021
a so-called “nameless” undetected malware stole a database in the cloud that contained some 1.2 Researchers on Wednesday said a so-called “nameless” undetected malware stole a database in the cloud that contained some 1.2 The malware also photographed the user if the device had a webcam. million Windows-based computers.

Hacker's King
OCTOBER 20, 2024
While cybersecurity primarily aims to protect users from threats like malware, hacking, and data breaches, some tools can monitor or track user activities in certain situations. Tools like firewalls, antivirus software, and encryption help safeguard information.

SecureWorld News
SEPTEMBER 27, 2023
To protect against them, you need to know the methods of hackers and the principles of malware operation. Tactical — Here, you will find reports or messages in formats like STIX-MISP that detail the tactics, techniques, and procedures (TTPs) deployed by hacker groups and specific malware.
Security Affairs
DECEMBER 11, 2024
” The group behind “Operation Digital Eye” remains unidentified due to the shared nature of malware, tools, and techniques, tactics and procedures (TTPs) within the Chinese cyber threat ecosystem. This tactic also allowed them to bypass firewall restrictions and evade closer scrutiny.

CyberSecurity Insiders
JUNE 20, 2023
The terms computer security, information security and cybersecurity were practically non-existent in the 1980s, but believe it or not, firewalls have existed in some form since that time. Over the years, the traditional firewall has transformed to meet the demands of the modern workplace and adapt to an evolving threat landscape.

eSecurity Planet
OCTOBER 26, 2023
Antivirus programs and firewalls are pretty good at catching malware before it can infect devices, but occasionally malware can slip through defenses, endangering personal and financial information. We’ll go over malware removal tools and steps, and offer some tips to keep your devices from getting reinfected.

CyberSecurity Insiders
JANUARY 11, 2022
Next-generation firewalls from Palo Alto Networks with AT&T Multi-Access Edge Computing (MEC) solutions are designed to help protect enterprises while optimizing security performance for these new use cases. They also help reduce complexity by assisting the customer with ongoing configuration changes to their firewall policies.

Hacker's King
DECEMBER 17, 2024
The cybersecurity world has been abuzz with news of a new Linux variant of FASTCash, a sophisticated malware targeting the banking sector. This new variant, designed to exploit Linux systems, signals a significant evolution in malware capabilities, highlighting the urgent need for robust defenses.

CyberSecurity Insiders
JANUARY 31, 2022
Stories from the SOC is a blog series that describes recent real-world security incident investigations conducted and reported by the AT&T SOC analyst team for AT&T Managed Threat Detection and Response customers. WannaCry malware was first discovered in May 2017 and a patch was released roughly two months prior to its public release.

SiteLock
AUGUST 27, 2021
As a website owner, chances are you’ve heard a great deal about malware. But you may wonder what exactly malware is, and why it’s such a serious threat to your website and your site’s visitors. What is Malware? And if you own a business website, a malware attack can cost you revenue and customers. Fileless Malware.

eSecurity Planet
JUNE 16, 2022
The 2022 SonicWall Cyber Threat Report found that all types of cyberattacks increased in 2021. Encrypted threats spiked 167%, ransomware increased 105%, and 5.4 billion malware attacks were identified by the report. In 2015, global cyber crime had a cost of about $3 trillion, and the cost is expected to rise to $10.5

Malwarebytes
JUNE 24, 2022
Threat actors are equally fond of it because it allows them to “live off the land”, and for the options it provides to create fileless malware or to gain persistence on a compromised system. The CIS discusses some security features available in PowerShell which can reduce abuse by threat actors. Reduce abuse.

IT Security Guru
MAY 20, 2024
This number highlights the widespread nature of digital threats. Today, common cyber threats include phishing, ransomware, and malware attacks, each capable of significantly disrupting operations and compromising sensitive data. It ensures your data remains secure against a wide array of cyber threats.

CyberSecurity Insiders
NOVEMBER 1, 2021
Since phishing attempts infect an individual’s system with malware, spyware, or viruses, it’s critical to use dedicated programs installed on all gadgets and throughout your system. Enact robust data security processes and firewalls. Implementing local firewalls is another good way to give that extra layer of security.

Hacker's King
DECEMBER 21, 2024
The proliferation of cyber threats demands innovative solutions, and generative AI is emerging as a transformative force in this arena. Far beyond its applications in content creation or virtual assistants, generative AI is revolutionizing cybersecurity by enhancing threat detection, automating responses, and fortifying defenses.

Responsible Cyber
JULY 14, 2024
Protecting sensitive information and maintaining seamless connectivity across distributed environments necessitates robust cybersecurity measures, with firewalls playing a crucial role. Malware Attacks : Remote devices are vulnerable to malicious software. As a result, the need for robust solutions like firewalls has become critical.

Security Boulevard
FEBRUARY 10, 2022
Malware, or code written for malicious purposes, is evolving. Software developers face new threats from malicious code as their tools and processes have proven to be an effective and lucrative threat vector. The first known instance of malware was the relatively benign Creeper Worm created by Robert H. Thomas in 1971.

Security Affairs
SEPTEMBER 25, 2020
Cybersecurity and Infrastructure Security Agency (CISA) revealed that a hacker breached a US federal agency and threat actors exfiltrated data. Threat actors implanted a malware in the network of an unnamed federal agency that was able to avoid detection. ” reads the analysis report published by CISA.

SecureWorld News
OCTOBER 10, 2024
In a world where cyber threats are becoming increasingly sophisticated, observability is essential for maintaining a robust security posture. An employee aware of cyber threats, protection measures, and the main tactics of malicious actors is less prone to social engineering attempts or phishing attacks.

The Last Watchdog
MARCH 1, 2019
Related: Why we’re in the Golden Age of cyber espionage. Enterprises have dumped small fortunes into stocking their SOCs (security operations centers) with the best firewalls, anti-malware suites, intrusion detection, data loss prevention and sandbox detonators money can buy. But this hasn’t done the trick.

eSecurity Planet
OCTOBER 10, 2024
Keeping your Mac safe from malicious threats is increasingly important as cyberattacks become more sophisticated and prevalent. With malware increasingly targeting macOS, many users wonder how to protect their devices best. This guide will explore the essential tools to help you secure your Mac against malware threats.
Security Boulevard
JANUARY 2, 2023
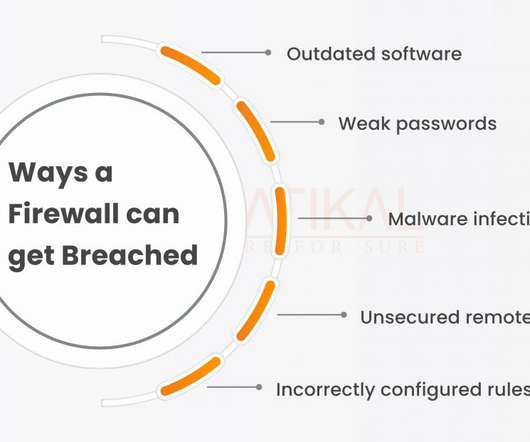
Introduction Every firewall in the market is vulnerable to hacking, despite what certain security providers may assert. Threat actors can still defeat a firewall’s security measures by employing a number of strategies.As Threat actors can still defeat a firewall’s security measures by employing a number of strategies.As

SiteLock
AUGUST 27, 2021
According to recent research, malware currently infects an estimated 12.8 Here are our top 4 cybersecurity tips your business can deploy now to get proactive on preventing data breaches , site defacement, DDoS attacks and other threats that put your sites at risk. Block cybercriminals and bad bots with a web application firewall.

Security Affairs
SEPTEMBER 20, 2020
We are absolutely committed to ensuring UK academia is as safe as possible from cyber threats, and will not hesitate to act when that threat evolves.”. This summer the NCSC investigated an increased number of cyber attacks on universities, schools, and colleges, most of them were hit with ransomware. .

Security Affairs
JULY 8, 2023
Ransomware Redefined: RedEnergy Stealer-as-a-Ransomware attacks MAR-10445155-1.v1 v1 Truebot Activity Infects U.S. Ransomware Redefined: RedEnergy Stealer-as-a-Ransomware attacks MAR-10445155-1.v1 v1 Truebot Activity Infects U.S.

SecureWorld News
JUNE 26, 2023
Even as your organization hires more security experts and invests in ever-better cybersecurity technology, malware, phishing, and other attacks remain a persistent threat to your organization and the data of your customers. Antivirus firewalls are the first line of defense against many malware and other intrusive attacks.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?



Let's personalize your content