How to Protect Operational Technology (OT) from Cyber Threats
CyberSecurity Insiders
JUNE 2, 2023
OT systems often come as closed systems with firmware and software installed by a supplier. In practice, however, air-gapping an OT system or firewalling its protected network is only the beginning of hardening its overall security. They are often unknown and dynamic, and, with OT systems firewalls dissolving, coming from more places.











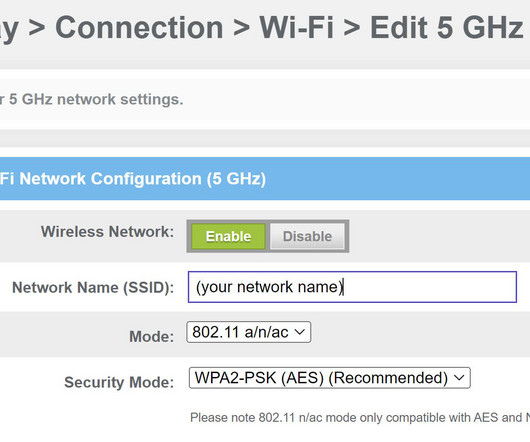











Let's personalize your content