How threat actors can use generative artificial intelligence?
Security Affairs
DECEMBER 1, 2024
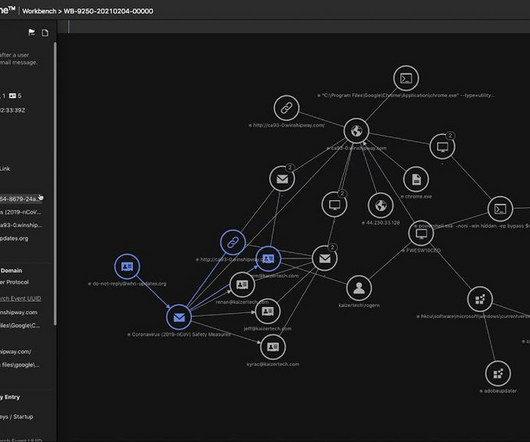
From generating deepfakes to enhancing phishing campaigns, GAI is evolving into a tool for large-scale cyber offenses GAI has captured the attention of researchers and investors for its transformative potential across industries. Unfortunately, its misuse by malicious actors is altering the cyber threat landscape.












Let's personalize your content