Cybersecurity Snapshot: Critical Infrastructure Orgs Found Vulnerable to Basic Hacks, While New MITRE Tool Uses ML to Predict Attack Chains
Security Boulevard
SEPTEMBER 20, 2024
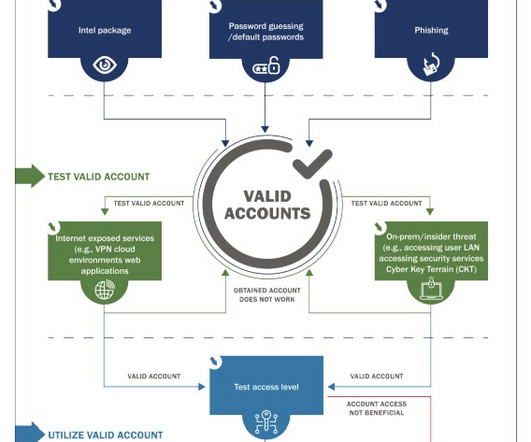
Specifically, CISA and USCG assessors had the most success gaining initial access, attaining network permanence, evading defenses and moving laterally by using valid accounts, phishing schemes and default credentials – all simple attack methods. Maintain a comprehensive asset inventory, and keep software updated and patched.
















Let's personalize your content