A week in security (June 28 – June 4)
Malwarebytes
JULY 5, 2021
Lil’ skimmer, the Magecart impersonator What is the WireGuard VPN protocol ? Last week on Malwarebytes Labs: Is it Game Over for VR Advergaming ? Other cybersecurity news.

Malwarebytes
JULY 5, 2021
Lil’ skimmer, the Magecart impersonator What is the WireGuard VPN protocol ? Last week on Malwarebytes Labs: Is it Game Over for VR Advergaming ? Other cybersecurity news.

Security Affairs
FEBRUARY 8, 2024
Cyber Insurance: US cyber insurance premiums soared by 50% in 2022, reaching $7.2 Cyber Skills Gap: By 2025, there could be 3.5 million unfilled cyber security jobs, showing a big need for skilled professionals. Market Size: The AI cyber security market was worth around $17.4 million per breach.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Boulevard
MAY 12, 2022
What Is Not Covered Under Cyber Insurance? Cyber insurance will not cover the cost for security remediation, the purchase of new security technology, or any 3rd pen testing, auditing, or installation of any security products. For organizations seeking cyber insurance, the road for predictable security runs in parallel.
Digital Shadows
JANUARY 14, 2025
To gain access to internal networks, Akira targeted local accounts with disabled multifactor authentication (MFA) and SonicOS firmware versions vulnerable to exploitation, often exposed to the internet for virtual private network (VPN) access.
Digital Shadows
NOVEMBER 26, 2024
Initial Access Broker (IAB) activity increased by 16% during the reporting period, heavily targeting US-based organizations due to perceived financial capability from cyber insurance. This incident shows that while security tools are essential, phishing emails can still slip through.

eSecurity Planet
MARCH 17, 2023
Examples of threatening traffic that IDPS solutions can combat include network intrusions, DDoS attacks, malware, and socially engineered attacks.
NetSpi Executives
APRIL 27, 2024
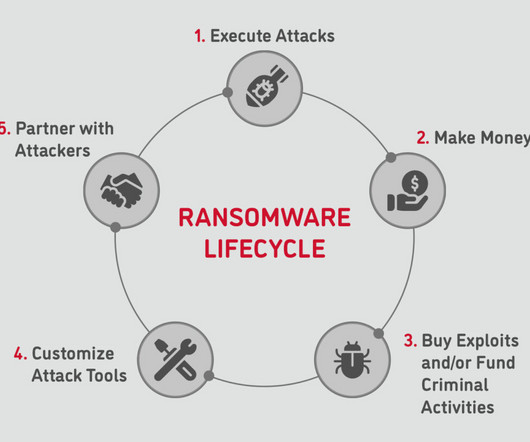
Ransomware, a definition Ransomware is a set of malware technologies, hacking techniques, and social engineering tactics that cybercriminals use to cause harm, breach data, and render data unusable. Ransomware attackers get into a network in many ways: Social engineering. Should I get a ransomware cyber insurance policy?
Let's personalize your content