Security Affairs newsletter Round 261
Security Affairs
APRIL 26, 2020
Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->. Copyright (C) 2014 Media.net Advertising FZ-LLC All Rights Reserved -->.

Security Affairs
APRIL 26, 2020
Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->. Copyright (C) 2014 Media.net Advertising FZ-LLC All Rights Reserved -->.

Security Affairs
OCTOBER 22, 2023
North Korea-linked APT groups actively exploit JetBrains TeamCity flaw Multiple APT groups exploited WinRAR flaw CVE-2023-38831 Californian IT company DNA Micro leaks private mobile phone data Threat actors have been exploiting CVE-2023-4966 in Citrix NetScaler ADC/Gateway devices since August A flaw in Synology DiskStation Manager allows admin account (..)
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Webroot
MAY 6, 2024
As we navigate through 2024, the cyber threat landscape continues to evolve, bringing new challenges for both businesses and individual consumers. The latest OpenText Threat Report provides insight into these changes, offering vital insights that help us prepare and protect ourselves against emerging threats.

Security Affairs
MARCH 17, 2023
According to statistics on insider threats, these threats may originate from employees, business contractors, or other reliable partners with simple access to your network. However, insider threat reports and recent developments have shown a sharp rise in the frequency of insider attacks.

Thales Cloud Protection & Licensing
APRIL 3, 2024
The 2023 Thales Data Threat Report – Financial Edition outlines some of the major threats faced today, from dealing with multi-cloud environments, to encryption management, ransomware and even good, old fashioned human error.
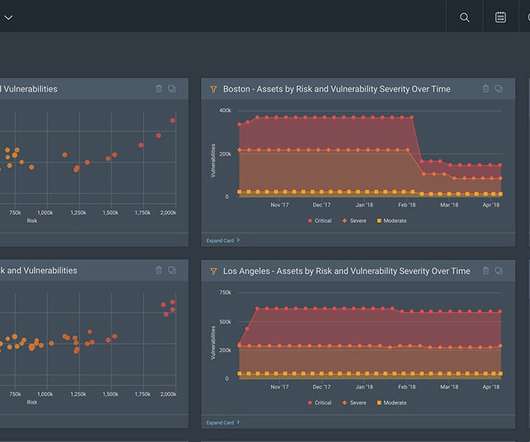
eSecurity Planet
JANUARY 9, 2023
With over 450 pre-configured templates, speedily understand where you have threats. Reporting and troubleshooting capabilities can be customized to meet particular needs and are exportable in multiple formats. Web crawling technology covers the entire attack surface, including the network, assets, and the deep web.

Security Affairs
OCTOBER 29, 2023
PII Belonging to Indian Citizens, Including their Aadhaar IDs, Offered for Sale on the Dark Web Spain police dismantled a cybercriminal group who stole the data of 4 million individuals CISA adds second Cisco IOS XE flaw to its Known Exploited Vulnerabilities catalog Cisco warns of a second IOS XE zero-day used to infect devices worldwide City of Philadelphia (..)
Let's personalize your content