China-linked APT Silk Typhoon targets IT Supply Chain
Security Affairs
MARCH 5, 2025
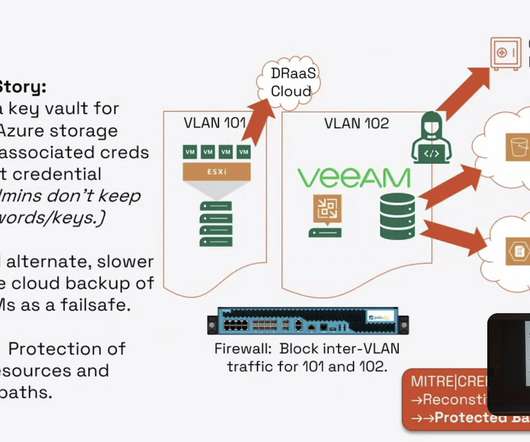
Silk Typhoon is a China-linked cyber espionage group involved in the cyber attack against the US Treasury. Though not directly attacking Microsoft cloud services, they exploit unpatched apps to escalate privileges and gain access to customer networks.



































Let's personalize your content