Many Cyber Attacks Begin by Breaking Human Trust
Lohrman on Security
OCTOBER 1, 2023
Sophisticated social engineering attacks have led to hundreds of data breaches this year. What can be done? And what new resources can help?
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Lohrman on Security
OCTOBER 1, 2023
Sophisticated social engineering attacks have led to hundreds of data breaches this year. What can be done? And what new resources can help?

Mitnick Security
APRIL 5, 2021
Social engineering attacks account for a massive portion of all cyber attacks, and studies show that these attacks are on the rise. According to KnowBe4 , more than 90% of successful hacks and data breaches start with a common type of social engineering attack called phishing.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

SecureWorld News
NOVEMBER 8, 2023
Social engineering attacks have long been a threat to businesses worldwide, statistically comprising roughly 98% of cyberattacks worldwide. The average business faces more than 700 of these types of attacks every single year.

The Hacker News
OCTOBER 11, 2021
Although organizations commonly go to great lengths to address security vulnerabilities that may exist within their IT infrastructure, an organization's helpdesk might pose a bigger threat due to social engineering attacks. There are many different types of social engineering

CyberSecurity Insiders
JUNE 17, 2022
In what appears as an operation first of its kind, Interpol has arrested over 2000 criminals who launched social engineering attacks worldwide. The operation to nab thousands of cyber criminals at a time was named ‘ First Light 2022’ and was performed with the coordination of police forces from about 76 countries.

Adam Levin
OCTOBER 8, 2019
In a Private Industry Notification (PIN), the FBI warned businesses that “cyber actors” had been observed, “circumventing multi-factor authentication through common social engineering and technical attacks.” The post FBI Warns of Cyber Attacks on Multi-Factor Authentication appeared first on Adam Levin.

Security Boulevard
NOVEMBER 14, 2022
A cybercriminal superstoreThe dark web, which can be accessed using special browsers like Tor, is a treasure trove of information, data, and software for carrying out cyber attacks.Reddit for CybercrimeThe Internet connects people. In the case of the dark web, this can be negative as cyber attackers find like-minded and motivated people.

The Hacker News
DECEMBER 11, 2023
In the ever-evolving cybersecurity landscape, one method stands out for its chilling effectiveness – social engineering. The answer lies in the intricate dance between the attacker's mind and human psychology. We delve deep into social engineering, exploring its But why does it work so well?

Jane Frankland
MAY 3, 2025
Allegedly orchestrated by the same group known as Scattered Spider, these attacks highlight the significant challenges even the most respected and established brands face in defending against modern cyber threats. Then, the focus of cyber attacks on retailers, and what lessons must be learned by business leaders and customers.

Security Affairs
FEBRUARY 20, 2023
Social engineering techniques are becoming increasingly sophisticated and are exploiting multiple emerging means, such as deep fakes. The human factor must always be considered as the first bastion of defense, even and especially against the most sophisticated cyber attacks. Deepfake technology, what’s it?

SecureWorld News
SEPTEMBER 17, 2022
Uber announced on Thursday evening that it was responding to a cybersecurity incident , which led to the ride-sharing giant taking internal communications and engineering systems offline. Sam Curry, a security engineer at Yuga Labs who corresponded with the individual, said "they pretty much have full access to Uber.

Hacker's King
DECEMBER 16, 2024
In the digital age, cyber-attacks are a growing concern for individuals, businesses, and governments worldwide. These attacks are becoming more sophisticated, targeted, and damaging, threatening data privacy, financial stability, and national security.

SecureWorld News
MARCH 17, 2025
You must equip your staff with the knowledge to recognize phishing attempts, social engineering ploys, and other common cyber threats through regular, targeted training sessions. You also need a clear and well-practiced incident response plan in place.

SecureWorld News
NOVEMBER 9, 2021
The company says an unauthorized third party socially engineered a customer support employee while talking on the phone, obtaining access to some customer support systems. The popular trading app Robinhood has just been hit with a major data breach affecting millions of its users.

Security Boulevard
JULY 10, 2024
Social engineering attacks are a cybersecurity threat. These attacks, which involve manipulating individuals into divulging confidential information, have been on the rise and pose a substantial risk to businesses, particularly for financial fraud.

CyberSecurity Insiders
MARCH 23, 2021
To all those who are concerned about the increase in cyber attacks on Maritime Industry, here’s an interesting finding to analyze. During a webinar conducted by Riviera, they revealed that the Human errors are causing an increase in cyber attacks on Maritime Industry.

Tech Republic Security
JUNE 4, 2024
Organisations providing services related to the Paris Olympics 2024 have an increased risk of cyber attack, a new study has found.

Javvad Malik
AUGUST 22, 2022
Lloyds of London has told its members to exclude nation state cyber attacks from insurance policies beginning in 2023, saying they pose unacceptable levels or risk. So who will decide whether an attack is a nation state or just little Timmy trying to impress his friends on the Discord channel?

The Hacker News
JULY 16, 2024
Scattered Spider is the designation given to a threat actor that's known for its sophisticated social engineering schemes to breach targets and establish persistence for follow-on exploitation and data theft. It also has a history of

CyberSecurity Insiders
JANUARY 17, 2022
North Korea, the nation that is being led by Kim Jong UN is back into news headlines for stealing cryptocurrency worth millions through cyber attacks. The post North Korea steals $400m cryptocurrency through Cyber Attacks appeared first on Cybersecurity Insiders.
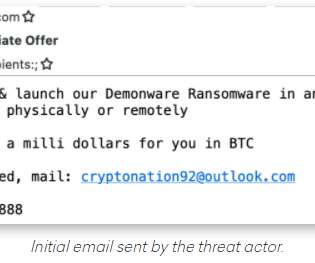
Krebs on Security
AUGUST 19, 2021
. “For decades, West African scammers, primarily located in Nigeria, have perfected the use of social engineering in cybercrime activity.”

CyberSecurity Insiders
AUGUST 18, 2021
Cybersecurity Researchers from Mandiant have disclosed that millions of IoT devices operating across the globe were vulnerable to cyber attacks because of a flaw in Kalay Cloud platform software supplied by ThroughTek. ThroughTek has issued a fix of 3.1.10

CyberSecurity Insiders
AUGUST 2, 2021
Florida Department of Economic Opportunity (DEO) has hit the news headlines for becoming a victim of a cyber attack that led to data breach of over 57,900 claimant accounts seeking unemployment benefits. The post Data breach news trending on Google Search Engine appeared first on Cybersecurity Insiders.

CyberSecurity Insiders
MAY 11, 2023
Tokyo MoU, the most active regional port control organization in the Asia Pacific, has revealed that its data was compromised for months and that hackers gained fraudulent access through a cyber attack. It is unclear how the attack has impacted the servers of the Port State Control (PSC) platform.

CyberSecurity Insiders
FEBRUARY 17, 2023
Succession Wealth, a financial wealth management service offering company, has released a press statement that a cyber attack targeted its servers and it can only reveal details after the investigation gets concluded. Prima Facie revealed that hackers accessed no client data in the attack.

Digital Shadows
JANUARY 22, 2025
In this blog, well preview the reports highlights and give insights into social engineering campaigns leveraging impersonating domains and our predictions for the threats shaping 2025. Organizations should implement domain monitoring, enforce DMARC policies, and train employees to recognize social engineering methods.

CyberSecurity Insiders
APRIL 4, 2023
Social engineering – specifically malicious cyber campaigns delivered via email – remain the primary source of an organization’s vulnerability to attack. Popularised in the 1990s, email security has challenged cyber defenders for almost three decades. billion phishing e-mails get delivered every day.

IT Security Guru
NOVEMBER 1, 2024
Cybersecurity Threats and Digital Warfare One of the most significant threats to national security in the modern era is cyber warfare. Cyber attacks can compromise critical infrastructure, financial systems, and sensitive government data.

Security Affairs
FEBRUARY 19, 2025
A cyber attack hit venture capital firm Insight Partners, threat actors gained unauthorized access to its information systems. According to the company, threat actors used a sophisticated social engineering technique to gain access to its infrastructure. ” reads a statement published by the company.
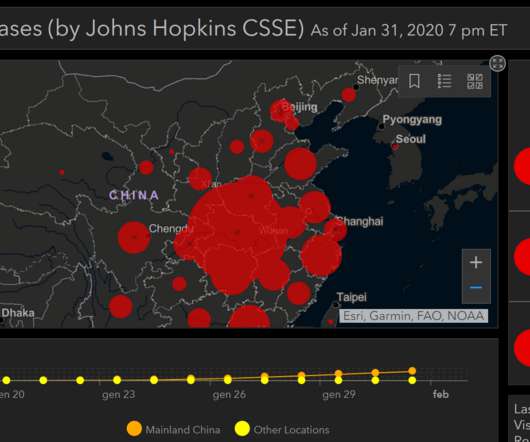
Security Affairs
FEBRUARY 26, 2020
Nowadays, it is common to say that the physical world and the cyber world are strictly connected. The proof is the leverage of the current physical threat, the CoronaVirus (COVID-19), as a social engineering trick to infect the cyber world. New Cyber Attack Campaign Leverages the COVID-19 Infodemic.

CyberSecurity Insiders
JANUARY 26, 2023
A cyber attack that appears to be a ransomware attack conducted through social engineering tactics has reportedly made hackers steal the source code of the game developer. The post Cyber Attack news headlines trending on Google appeared first on Cybersecurity Insiders.
Digital Shadows
NOVEMBER 26, 2024
Phishing often serves as the gateway to cyber attacks, opening the door to impactful follow-on activity like malware and ransomware deployment or access to internal networks, ultimately causing substantial financial losses. This incident shows that while security tools are essential, phishing emails can still slip through.

The Last Watchdog
APRIL 28, 2020
As coronavirus-themed cyber attacks ramp up, consumers and companies must practice digital distancing to keep themselves protected. That, of course, presents the perfect environment for cybercrime that pivots off social engineering. Sadly, coronavirus phishing and ransomware hacks already are in high gear.

CyberSecurity Insiders
JANUARY 19, 2023
News is out that social security numbers of nearly 35,000 users were leaked in a cyber attack that could have emerged from a credential stuffing campaign launched by a state funded actor. According to the update provided by a source from PayPal, the attack took place on December 6 and was identified at the end of last month.

CyberSecurity Insiders
JANUARY 7, 2022
user accounts related to 17 companies was reportedly compromised in a Credential Stuffing Cyber Attack. To those unaware of such attacks, here’s a gist. A credential stuffing is a kind of automated online process where hackers attempt to access online accounts by using usernames and passwords sourced from various cyber attacks.

Security Boulevard
MARCH 17, 2025
In reality, many of the most successful breaches stem from simple tactics like phishing emails, social engineering, and exploiting basic security misconfigurations. Attackers benefit when victims are overly trusting, untrained, or distractedthereby susceptible to simple manipulations that appear obviously suspicious in hindsight.

The Hacker News
JUNE 1, 2023
and South Korean intelligence agencies have issued a new alert warning of North Korean cyber actors' use of social engineering tactics to strike think tanks, academia, and news media sectors.

NetSpi Executives
OCTOBER 24, 2023
Don’t be afraid of social engineering attacks this Cybersecurity Awareness Month! In the spirit of this year’s theme, we created a parody of the Monster Mash to share social engineering prevention tips far and wide. In fact, 98 percent of cyber attacks involve some form of social engineering.

The Hacker News
OCTOBER 1, 2022
A "highly operational, destructive, and sophisticated nation-state activity group" with ties to North Korea has been weaponizing open source software in their social engineering campaigns aimed at companies around the world since June 2022.

Security Boulevard
JANUARY 13, 2025
Hackers are exploiting the digital breadcrumbs your personally identifiable information (PII) that you leave behind daily to launch their cyber attacks. The post How Your Digital Footprint Fuels Cyberattacks and What to Do About It appeared first on Security Boulevard.

SecureWorld News
JUNE 17, 2024
Ezra Graziano, Director of Federal Accounts at Zimperium, emphasized the urgency for defense against such evolving social engineering tactics. RELATED: The Impact of AI on Social Engineering Cyber Attacks ] Follow SecureWorld News for more stories related to cybersecurity.

Mitnick Security
FEBRUARY 22, 2023
There’s something both humbling and terrifying about watching industry giants like Twitter and Uber fall victim to cyber attacks.

Security Boulevard
JANUARY 23, 2022
What are DDOS attack tools? DDOS attacks are cyber- attacks targeted at rendering certain computers, network systems and servers non-functional. Attackers have to carry out a long series of actions that involve social engineering, data breaches and sometimes even system testing.

Security Boulevard
AUGUST 21, 2024
Attacks today can be executed through a myriad of communication channels, including emails, social media and mobile applications. The post The Golden Age of Impersonation: The Dual Role of AI in Cyber Attacks & Cyber Defense appeared first on Security Boulevard.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content