Many Cyber Attacks Begin by Breaking Human Trust
Lohrman on Security
OCTOBER 1, 2023
Sophisticated social engineering attacks have led to hundreds of data breaches this year. What can be done? And what new resources can help?
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Lohrman on Security
OCTOBER 1, 2023
Sophisticated social engineering attacks have led to hundreds of data breaches this year. What can be done? And what new resources can help?

SecureWorld News
DECEMBER 30, 2024
Recent cybersecurity statistics indicate that data breaches are escalating into a significant international concern. This underscores the need not only for strong preventive measures to protect critical information but also for a well-defined strategy to contain the damage if attackers successfully breach your defenses.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Mitnick Security
APRIL 5, 2021
Social engineering attacks account for a massive portion of all cyber attacks, and studies show that these attacks are on the rise. According to KnowBe4 , more than 90% of successful hacks and data breaches start with a common type of social engineering attack called phishing.

SecureWorld News
NOVEMBER 8, 2023
Social engineering attacks have long been a threat to businesses worldwide, statistically comprising roughly 98% of cyberattacks worldwide. The average business faces more than 700 of these types of attacks every single year.

CyberSecurity Insiders
AUGUST 2, 2021
Florida Department of Economic Opportunity (DEO) has hit the news headlines for becoming a victim of a cyber attack that led to data breach of over 57,900 claimant accounts seeking unemployment benefits. The post Data breach news trending on Google Search Engine appeared first on Cybersecurity Insiders.

CyberSecurity Insiders
AUGUST 12, 2021
The Korean based company that is into the business of perfume and clothes selling said that the data leak took place on August 8th, 2021 and was because of a cyber attack on a cloud based data storage firm. The post Data Breach on French Luxury brand Chanel appeared first on Cybersecurity Insiders.

Security Boulevard
NOVEMBER 14, 2022
A cybercriminal superstoreThe dark web, which can be accessed using special browsers like Tor, is a treasure trove of information, data, and software for carrying out cyber attacks.Reddit for CybercrimeThe Internet connects people. It really is a lot like Reddit or other social networks where you share information.

SecureWorld News
NOVEMBER 9, 2021
The popular trading app Robinhood has just been hit with a major data breach affecting millions of its users. The company says an unauthorized third party socially engineered a customer support employee while talking on the phone, obtaining access to some customer support systems.

SecureWorld News
SEPTEMBER 17, 2022
According to this cyber wonderkid, they used social engineering to pull off the hack. This incident is yet another example of how easy it is for malicious threat actors to use social engineering to gain access to an organization's internal systems. Uber's response to being breached. September 16, 2022.

CyberSecurity Insiders
FEBRUARY 17, 2023
Succession Wealth, a financial wealth management service offering company, has released a press statement that a cyber attack targeted its servers and it can only reveal details after the investigation gets concluded. Prima Facie revealed that hackers accessed no client data in the attack.

CyberSecurity Insiders
FEBRUARY 27, 2023
Stanford University, one of the top ranked Universities of the United States and world, has become a victim to a cyber attack leading to data leak or unauthorized access of sensitive information. Details are in that the data leak of students pursuing Economics PH.D

CyberSecurity Insiders
SEPTEMBER 7, 2021
A sophisticated cyber attack launched on the visa website of French government has led to a data breach where sensitive info related to applicants such as nationalities, birth dates and passport numbers were exposed to hackers. France-based media channels report that the incident could be a state funded attack.

Security Affairs
OCTOBER 30, 2018
In a letter sent to members, Christina Salcido, vice president of mission operations for GSOC, confirmed that attackers may have accessed to names, birth dates, home addresses, insurance policy numbers and health history for some members. Experts warn of possible social-engineering-based cyber attacks leveraging the exposed info.

CyberSecurity Insiders
JANUARY 30, 2023
JD Sports, Britain’s online retailer of branded sportswear, has reportedly become a victim of a cyber attack that leaked information of over 10 million customers. The post Data Breach at Britain JD Sports leaks 10 million customers appeared first on Cybersecurity Insiders.

Responsible Cyber
NOVEMBER 17, 2024
Image Source: AI Generated Recent data breaches have exposed sensitive information from millions of customers across healthcare, financial services, and technology sectors. These data breaches highlight significant vulnerabilities in vendor relationships and supply chain security. million per incident in 2023.
Digital Shadows
NOVEMBER 26, 2024
Phishing often serves as the gateway to cyber attacks, opening the door to impactful follow-on activity like malware and ransomware deployment or access to internal networks, ultimately causing substantial financial losses. For organizations, this can result in account compromise, data loss, data breaches, and operational disruption.

CyberSecurity Insiders
APRIL 13, 2023
As per the details available to our Cybersecurity Insiders in the Port of Halifax, located in Nova Scotia, the Ports at Montreal and Quebec, both based in province of Quebec, were digitally disrupted by a cyber-attack. Presently, preliminary analysis suggests that there is a data breach in their network.

Security Boulevard
JANUARY 23, 2022
What are DDOS attack tools? DDOS attacks are cyber- attacks targeted at rendering certain computers, network systems and servers non-functional. Attackers have to carry out a long series of actions that involve social engineering, data breaches and sometimes even system testing.

Security Affairs
FEBRUARY 8, 2024
Phishing Attacks: Phishing is the top cyber attack, causing 90% of data breaches. Shockingly, 96% of these attacks come through email. Ransomware Attacks: In 2023, a whopping 72.7% The cost of these attacks could hit $265 billion annually by 2031. of organizations faced ransomware.
Security Affairs
DECEMBER 17, 2023
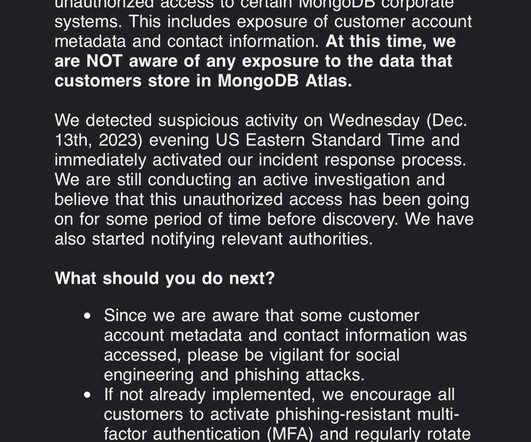
MongoDB on Saturday disclosed it is investigating a cyber attack against certain corporate systems. The cyber attack was discovered on December 13, 2023, and led to the exposure of customer account metadata and contact information. .” ” reads the alert published by the company.”

Jane Frankland
FEBRUARY 7, 2025
When data breaches escalate, cyber-attacks grow more sophisticated, nation states ramp up their digital warfare, and regulations tighten the noose, staying ahead isnt just an optionits your only line of defence. The AI Question AI is on everyones lips and theres no denying that its revolutionising the way we do business.

SecureWorld News
MAY 20, 2020
How do most data breaches occur? Who are the threat actors behind these cyber attacks? And what are key attacker motivations? The 2020 Verizon Data Breach Investigations Report (DBIR) has the answers. The things that follow are based on that data set. What are the top 5 causes of data breaches?

Security Affairs
FEBRUARY 27, 2021
The telecommunications giant T-Mobile disclosed a data breach after some of its customers were apparently affected by SIM swap attacks. The telecommunications provider T-Mobile has disclosed a data breach after it became aware that some of its customers were allegedly victims of SIM swap attacks.

CyberSecurity Insiders
FEBRUARY 22, 2021
A security expert monitoring the currency stealing campaigns digitally says that cyber crooks are stealing smaller amounts from victims, but targeting many of them to make their cash bells ringing. The post Cyber Attacks in UK leading to Silent Stealing appeared first on Cybersecurity Insiders.

The Last Watchdog
MARCH 4, 2024
Keeping these systems up to date and installing the latest security patches can help minimize the frequency and severity of data breaches among organizations. Ransomware: This attack involves criminals holding a network and its precious data hostage until the enterprise pays the demanded amount. Strengthen authentication.

CyberSecurity Insiders
APRIL 18, 2023
As data breaches and cyber attacks continue to rise, the traditional method of securing online accounts using passwords is becoming increasingly ineffective. Hackers can easily crack simple and commonly used passwords, or even use social engineering tactics to trick users into giving away their login credentials.

The Last Watchdog
JULY 24, 2023
Today, bad actors are ruthlessly skilled at cracking passwords – whether through phishing attacks, social engineering, brute force, or buying them on the dark web. In fact, according to Verizon’s most recent data breach report, approximately 80 percent of all breaches are caused by phishing and stolen credentials.

Identity IQ
JUNE 1, 2023
The Rise of AI Social Engineering Scams IdentityIQ In today’s digital age, social engineering scams have become an increasingly prevalent threat. Social engineering scams leverage psychological manipulation to deceive individuals and exploit the victims’ trust.

CyberSecurity Insiders
JANUARY 16, 2023
School districts are constantly being targeted by cyber attacks, leading to data breaches and information misuse. Following basic cybersecurity hygiene by students and staff while sharing the data is also important, as it avoids being targeted by phishing scams or other type of social engineering attacks.

CyberSecurity Insiders
MARCH 15, 2023
Australian firm Latitude Financial Services is hitting news headlines as a cyber attack on its servers has led to the data breach of 225,000 customers. Among the stolen data, a majority of the documents are related to driving licenses, employee login details, and such. The company which has over 2.8

The Last Watchdog
AUGUST 20, 2024
Impact of cyber attacks The financial toll of cyber incidents can be staggering. The average cost of a data breach ballooned to $4.88 “As cyber threats become more sophisticated, the cost of not investing in cybersecurity training escalates exponentially,” explains Dara Warn, CEO of INE Security.

Security Affairs
DECEMBER 17, 2023
CISA and ENISA enhance their Cooperation CISA adds Qlik bugs to exploited vulnerabilities catalog Report: 2.6 CISA and ENISA enhance their Cooperation CISA adds Qlik bugs to exploited vulnerabilities catalog Report: 2.6 CISA and ENISA enhance their Cooperation CISA adds Qlik bugs to exploited vulnerabilities catalog Report: 2.6

Security Affairs
NOVEMBER 29, 2020
A cyberattack crippled the IT infrastructure of the City of Saint John Hundreds of female sports stars and celebrities have their naked photos and videos leaked online Romanians arrested for running underground malware services Threat actor shared a list of 49,577 IPs vulnerable Fortinet VPNs Computer Security and Data Privacy, the perfect alliance (..)

SecureWorld News
SEPTEMBER 15, 2020
Now the Department of Veteran's Affairs (VA) is sending breach notification letters to tens of thousands of veterans impacted by a recent data breach. What do we know about the VA data breach against veterans? How large was the VA data breach? How do I know if I am part of the VA data breach?

Security Affairs
SEPTEMBER 3, 2023
Enjoy a new round of the weekly SecurityAffairs newsletter, including the international press.

Security Boulevard
DECEMBER 29, 2022
What are DDOS attack tools? DDOS attacks are cyber- attacks targeted at rendering certain computers, network systems and servers non-functional. Attackers have to carry out a long series of actions that involve social engineering, data breaches and sometimes even system testing.

Security Affairs
SEPTEMBER 8, 2024
Quishing, an insidious threat to electric car owners Google fixed actively exploited Android flaw CVE-2024-32896 Discontinued D-Link DIR-846 routers are affected by code execution flaws.

Thales Cloud Protection & Licensing
JANUARY 24, 2022
Cyber criminals are also evolving with technology to satisfy their nefarious goals. Attacks are increasing in volume and sophistication and are becoming costlier for all businesses. The IBM Cost of Data Breach 2021 report indicates that data breaches have become more expensive by 10% compared to 2020, amounting to $4.24

Security Boulevard
JUNE 26, 2023
Unfortunately, the increasing reliance on digital systems and capabilities has also attracted an ever-growing number of malicious actors seeking to defraud businesses through phishing , social engineering , or ransomware attacks. The end result of these types of cyber attacks are often highly public and damaging data breaches.

Security Affairs
JUNE 11, 2023
Experts found new MOVEit Transfer SQL Injection flaws The University of Manchester suffered a cyber attack and suspects a data breach Russians charged with hacking Mt. Enjoy a new round of the weekly SecurityAffairs newsletter, including the international press.

The Last Watchdog
OCTOBER 15, 2019
Compromised logins continue to facilitate cyber attacks at all levels, from phishing ruses to credential stuffing to enabling hackers to probe deep inside of a breached network. Verizon has been doing this very substantive report, in which it culls hard evidence collected in actual data breach investigations, for 12 years.

Appknox
JUNE 23, 2022
More threats were detected on iOS than Android devices; 68% of Australian CISOs expect their organization to suffer a material cyber-attack within the next year. Mobile devices pave the way to launch ransomware attacks on Australian businesses of every scale and domain. Common Trends Among the Australian Mobile Threats.

Digital Shadows
OCTOBER 23, 2024
The attacker gained initial access to two employee accounts by carrying out social engineering attacks on the organization’s help desk twice. Within six hours, the attacker began encrypting the organization’s systems. This concealed their attack until the environment was encrypted and backups were sabotaged.

Approachable Cyber Threats
SEPTEMBER 24, 2022
Category News, Social Engineering. All of the attacks were carried out with relatively simple phishing and social engineering techniques. So far in September, IHG , Uber , and Rockstar Games have all been victims of major independent cyber attacks. Risk Level. The common theme?
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content