How 1-Time Passcodes Became a Corporate Liability
Krebs on Security
AUGUST 30, 2022
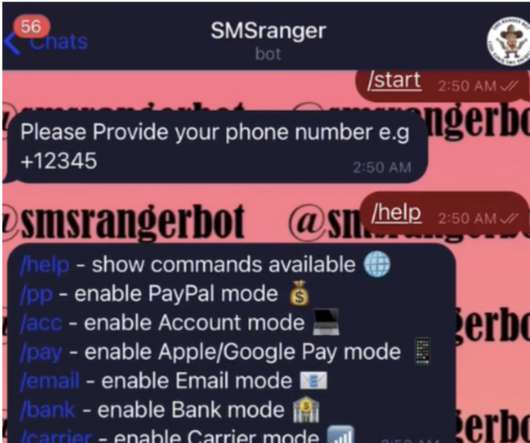
4 it became aware of unauthorized access to information related to a limited number of Twilio customer accounts through a sophisticated social engineering attack designed to steal employee credentials. On that last date, Twilio disclosed that on Aug. ” On July 28 and again on Aug. According to an Aug. In an Aug.














Let's personalize your content