Breaking a Password Manager
Schneier on Security
JUNE 4, 2024
Interesting story of breaking the security of the RoboForm password manager in order to recover a cryptocurrency wallet password.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Schneier on Security
JUNE 4, 2024
Interesting story of breaking the security of the RoboForm password manager in order to recover a cryptocurrency wallet password.

Tech Republic Security
JULY 6, 2023
The post New Malware Targets 97 Browser Variants, 76 Crypto Wallets & 19 Password Managers appeared first on TechRepublic. Learn how the Meduza Stealer malware works, what it targets and how to protect your company from this cybersecurity threat.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Affairs
MARCH 10, 2025
DoJ, threat actors may have used private keys extracted by cracking the victim’s password vault stolen from the 2022 security breach suffered by an online password manager. The scale and speed of the theft indicate a coordinated effort, consistent with previous breaches of online password managers and crypto thefts.

Security Affairs
NOVEMBER 15, 2024
The malware could harvest a huge trove of data from infected systems, including cookies, autofill, cryptocurrency wallets, 2FA authenticators, password managers, and email client information. Glove Stealer is a.NET-based information stealer that targets browser extensions and locally installed software to steal sensitive data.
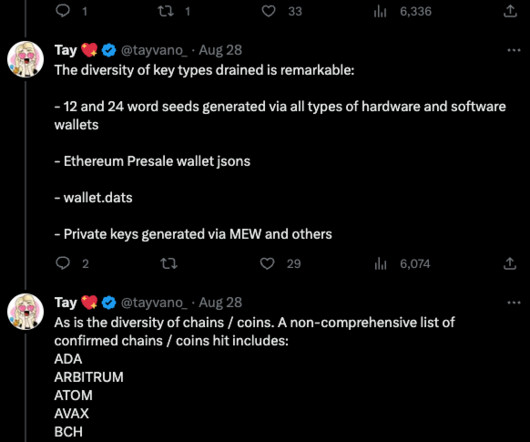
Krebs on Security
SEPTEMBER 5, 2023
In November 2022, the password manager service LastPass disclosed a breach in which hackers stole password vaults containing both encrypted and plaintext data for more than 25 million users. Taylor Monahan is founder and CEO of MetaMask , a popular software cryptocurrency wallet used to interact with the Ethereum blockchain.
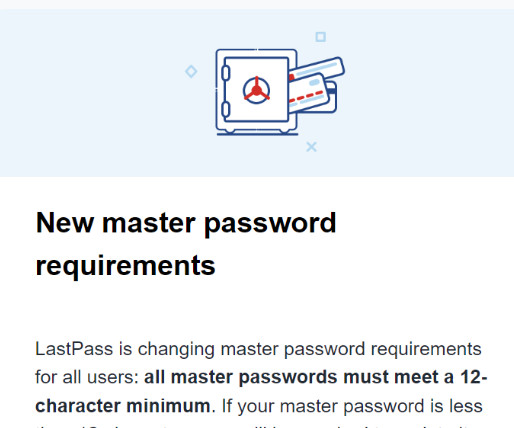
Krebs on Security
SEPTEMBER 22, 2023
The password manager service LastPass is now forcing some of its users to pick longer master passwords. But critics say the move is little more than a public relations stunt that will do nothing to help countless early adopters whose password vaults were exposed in a 2022 breach at LastPass. ”
Security Affairs
JULY 3, 2023
The malware also targets crypto wallet extensions, password managers, and 2FA extensions. The malware also collects a variety of data, including system info, browser info, password manager info, miner related registry info, and installed games info. ” continues the analysis.
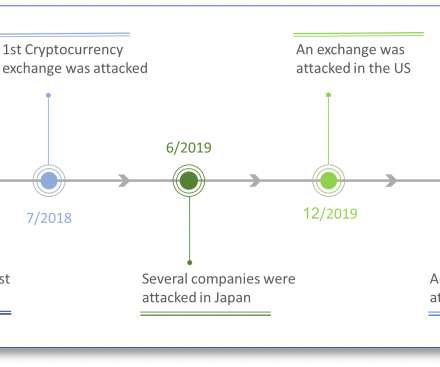
Security Affairs
JUNE 24, 2020
The CryptoCore hacker group that is believed to be operating out of Eastern Europe has stolen around $200 million from online cryptocurrency exchanges. Experts from ClearSky states that a hacker group tracked as CryptoCore, which is believed to be operating out of Eastern Europe, has stolen around $200 million from cryptocurrency exchanges.


Krebs on Security
JULY 29, 2021
22, 2020, when cryptocurrency wallet company Ledger acknowledged that someone had released the names, mailing addresses and phone numbers for 272,000 customers. Don’t re-use passwords. If you’re the kind of person who likes to use the same password across multiple sites, then you definitely need to be using a password manager.
SecureList
OCTOBER 29, 2024
Armed with BitLocker To Go, the attackers manipulate the registry, primarily to create the branches and keys that the Trojan needs to operate: That done, Lumma, again using the utility, searches the victim’s device for files associated with various cryptocurrency wallets and steals them: Then, the attackers view browser extensions related to (..)

Krebs on Security
JUNE 15, 2024
One of the more popular SIM-swapping channels on Telegram maintains a frequently updated leaderboard of the most accomplished SIM-swappers, indexed by their supposed conquests in stealing cryptocurrency. That leaderboard currently lists Sosa as #24 (out of 100), and Tylerb at #65.
Krebs on Security
DECEMBER 29, 2022
You just knew 2022 was going to be The Year of Crypto Grift when two of the world’s most popular antivirus makers — Norton and Avira — kicked things off by installing cryptocurrency mining programs on customer computers. The now-defunct and always phony cryptocurrency trading platform xtb-market[.]com,

Security Affairs
DECEMBER 29, 2023
On Christmas Eve, Resecurity’s HUNTER unit spotted the author of perspective password stealer Meduza has released a new version (2.2). Altogether, Meduza makes a great competitor to Azorult , Redline , Racoon , and Vidar Stealer used by cybercriminals for account takeover (ATO), online-banking theft, and financial fraud.

Krebs on Security
MAY 19, 2020
The SBU said they found on Sanix’s computer records showing he sold databases with “logins and passwords to e-mail boxes, PIN codes for bank cards, e-wallets of cryptocurrencies, PayPal accounts, and information about computers hacked for further use in botnets and for organizing distributed denial-of-service (DDoS) attacks.”

Malwarebytes
FEBRUARY 19, 2025
With stolen passwords, the impact is even broader; hackers could wire funds from a breached online banking account into their own, or masquerade as someone on social media to ask friends and family for money. Some info stealers dont even require an additional stepthey can take cryptocurrency directly from a victims online accounts.

Troy Hunt
JUNE 11, 2018
They suspected that a significant volume of the credentials obtained in these incidents have been used to access mailboxes, cryptocurrency exchanges, cloud service accounts and other similar online assets. In total, there were 655k records affected that are now searchable.

Krebs on Security
JANUARY 30, 2024
authorities arrested a 19-year-old Florida man charged with wire fraud, aggravated identity theft, and conspiring with others to use SIM-swapping to steal cryptocurrency. 12 blog post , the attackers used their access to Mailchimp employee accounts to steal data from 214 customers involved in cryptocurrency and finance. 9, 2024, U.S.
WIRED Threat Level
MAY 28, 2024
Thanks to a flaw in a decade-old version of the RoboForm password manager and a bit of luck, researchers were able to unearth the password to a crypto wallet containing a fortune.
Malwarebytes
NOVEMBER 19, 2024
Lumma steals information from cryptocurrency wallets and browser extensions, as well as two-factor authentication details. AMOS makes money for its operators by finding and stealing valuable information on the computers it infects, such as credit card details, authentication cookies, passwords and cryptocurrency.

Malwarebytes
MARCH 17, 2022
Cryptocurrency wallet attacks. People new to cryptocurrency often gravitate to services which take the hassle out of setting everything up. Some folks may feel the above process isn’t as secure as storing their cryptocurrency on standalone devices. Below, we dig into a few of those. Ransomware supply chain triple-threat.

Malwarebytes
DECEMBER 4, 2024
With the value of cryptocurrencies going to the roof, you can expect several attempts to get defrauded if you even show the slightest interest in the topic or not. And avoiding them is in everyone’s best interest—the Federal Bureau of Investigation (FBI) reported estimated losses to cryptocurrency related fraud exceeding $5.6

Responsible Cyber
JULY 13, 2024
Introduction Cryptocurrency represents a groundbreaking innovation in the financial sector, offering decentralized, peer-to-peer digital transactions through blockchain technology. However, the allure of these digital assets also attracts malicious actors, making cryptocurrency security paramount.

Malwarebytes
MAY 6, 2022
Use 2FA and a password manager. We don’t know what the phishing page was trying to obtain, but it will be something valuable, which probably means cryptocurrency or Discord logins. You can make it harder to steal your Discord login by using a password manager and two-factor authentication (2FA).

Malwarebytes
JUNE 3, 2022
By focusing on this context, we hope that you’ll come away with a stronger understanding about, for instance, why you should use a password manager rather than that you should use a password manager. By selling fake raffle tickets for the promotion, the scammers raked in $438,000 worth of cryptocurrency.

Security Affairs
MAY 21, 2021
CyberNews researchers found that crooks could abuse cryptocurrency exchange API keys and steal cryptocurrencies. CyberNews researchers found that cybercriminals are able to abuse cryptocurrency exchange API keys and steal cryptocurrencies from their victims’ accounts without being granted withdrawal rights.

Security Affairs
MAY 13, 2024
Password Management : Use strong, unique passwords and implement multi-factor authentication (MFA) whenever possible, prioritizing authentication apps or hardware tokens over SMS text-based codes.

Malwarebytes
MARCH 3, 2022
Nvidia LHR graphics cards detect when they’re being used for Ethereum (ETH) cryptocurrency mining and automatically halve the hash rate. If you recognize one or more of them we would encourage you to not only change them, but also to start using a password manager. They can auto-generate highly secure passwords for you.
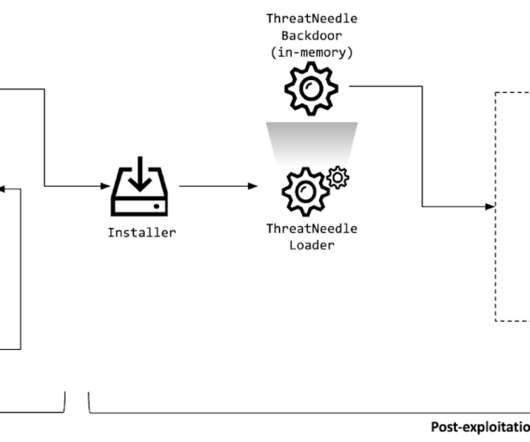
Security Affairs
FEBRUARY 25, 2021
The ThreatNeedle malware used in this campaign belongs to a malware family known as Manuscrypt, which belongs to the Lazarus group and has previously been seen attacking cryptocurrency businesses.” ” reads the press release published by Kaspersky. ” reads the report published by the experts.
Security Affairs
SEPTEMBER 27, 2022
Threat actors behind the new ‘Erbium’ information-stealing malware are distributing it as fake cracks and cheats for popular video games to steal victims’ credentials and cryptocurrency wallets. Collecting user credentials, such as passwords, from a range of popular chat and email programs, as well as web browsers.

eSecurity Planet
APRIL 21, 2021
From news of a collage selling for almost $70 million at Christie’s auction house to a portrayal of Janet Yellen and Morpheus rapping about cryptocurrency on SNL , the current craze is all about non-fungible tokens (NFTs). Also Read: Best Password Management Software & Tools for 2021. How do NFTs work?

Malwarebytes
APRIL 3, 2023
A new macOS malware—called MacStealer—that is capable of stealing various files, cryptocurrency wallets, and details stored in specific browsers like Firefox, Chrome, and Brave, was discovered by security researchers from Uptycs, a cybersecurity company specializing in cloud security. Users of macOS Catalina (10.5)
Security Affairs
MAY 9, 2022
The Jester stealer is able to steal credentials and authentication tokens from Internet browsers, MAIL/FTP / VPN clients, cryptocurrency wallets, password managers, messengers, game programs, and more.

Malwarebytes
SEPTEMBER 29, 2022
Erbium targets multiple forms of cryptocurrency wallet, along with password managing software and two-factor authentication (2FA) data. According to the latest research available , it leans into that well worn tactic of plundering several forms of web browser for passwords, autofill data, and also cookies.
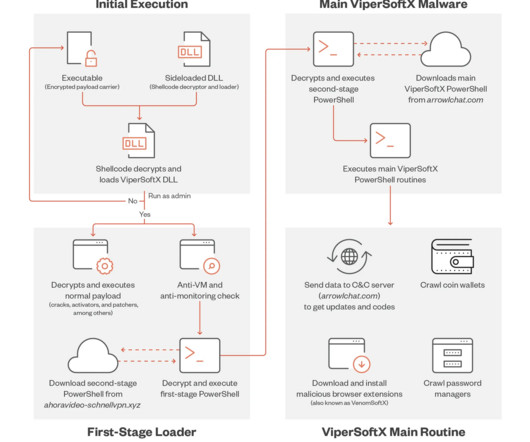
Security Affairs
APRIL 29, 2023
ViperSoftX is a JavaScript-based Remote Access Trojan (RAT) and cryptocurrency stealer that was first analyzed by Fortinet in February 2020. ” reads the analysis published by Trend Micro. In November 2022, Avast researchers discovered a malicious extension for Chromium-based web browsers that was spreading via ViperSoftX. .

CyberSecurity Insiders
AUGUST 24, 2022
And studies have revealed that the newly developed file-encrypting malware is using an Open-source password management library for encryption and is having capabilities of remaining anonymous, ex-filtrate data, and having abilities to give control to remote servers. The third is something astonishing to read!

eSecurity Planet
FEBRUARY 17, 2025
Users looking for extra tight security: It was reported that Microsoft Defender missed a type of malware that hijacked a victim’s Google account in the Chrome browser and stole over $24,000 in cryptocurrency. Like Norton and McAfee, Bitdefender offers a VPN and a password manager through Total Security.

SC Magazine
MAY 12, 2021
Researchers found 167 counterfeit Android and iOS apps that attackers used to steal money from victims who believed they installed a financial trading, banking or cryptocurrency app. Use strong access controls to protect the most important accounts using a password manager and multifactor authentication.

Security Affairs
SEPTEMBER 22, 2019
A flaw in LastPass password manager leaks credentials from previous site. France and Germany will block Facebooks Libra cryptocurrency. Drone attacks hit two Saudi Arabia Aramco oil plants. Astaroth Trojan leverages Facebook and YouTube to avoid detection. Data leak exposes sensitive data of all Ecuador ‘citizens.

SecureList
FEBRUARY 21, 2025
It also steals data from 11 browsers, including Chrome, Chromium, Edge, Kometa, Vivaldi, Brave, Opera Stable, Opera GX Stable, Opera Neon, Mozilla Firefox and Waterfox, as well as cryptocurrency wallets such as Binance and Ethereum. Command servers This sample contains encoded and encrypted addresses of command servers.

Malwarebytes
JUNE 17, 2021
Malwarebytes Browser Guard not only blocks some advertisements and trackers, it also stops in-browser cryptojackers (unwanted cryptocurrency miners), and it also uses an extended version of the Malwarebytes Premium blocklist that will stop malicious sites from loading—including sites that are involved in tech support scams.

Malwarebytes
MAY 10, 2022
The list of potential target areas includes: Internet browsers MAIL/FTP/VPN clients Cryptocurrency wallets Password managers Messengers Game programs. Jester Stealer is also capable of swiping screenshots a nd stealing network passwords. Impact on affected systems.

Security Boulevard
JUNE 15, 2023
Oftentimes this is credential data, but it can be any data that may have financial value to an adversary; this includes paid online service accounts, cryptocurrency wallets, instant messenger, or email contacts lists, etc. Key Mystic Stealer functions include its ability to extract data from web browsers and cryptocurrency wallets.

Security Affairs
JANUARY 27, 2022
Other affected businesses include Chip, a UK-based savings app boasting 400,000 users; Hoolah, a shopping app with over 100,000 installs ; Mode, a cryptocurrency app with over 50,000 installs ; and Greenwheels, a car-sharing service with over 50,000 installs. Note that iOS users are affected as much as Android users.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content