Feds Charge Five Men in ‘Scattered Spider’ Roundup
Krebs on Security
NOVEMBER 21, 2024
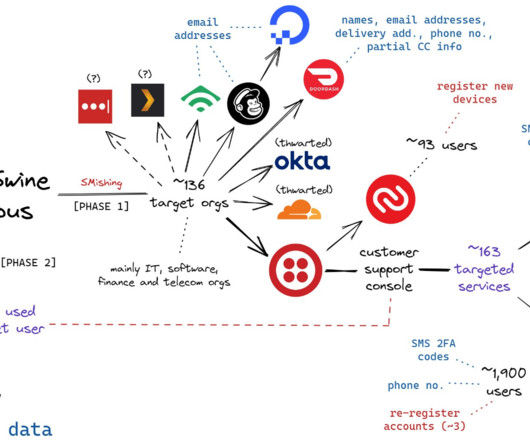
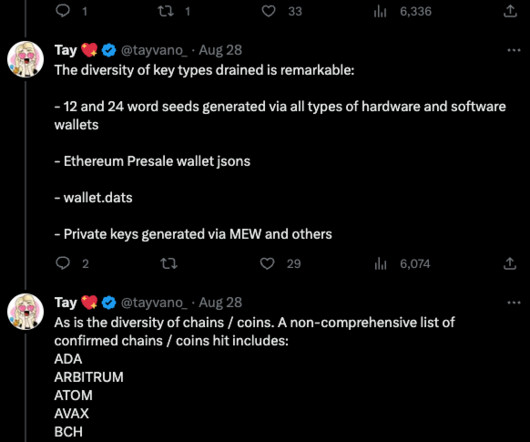
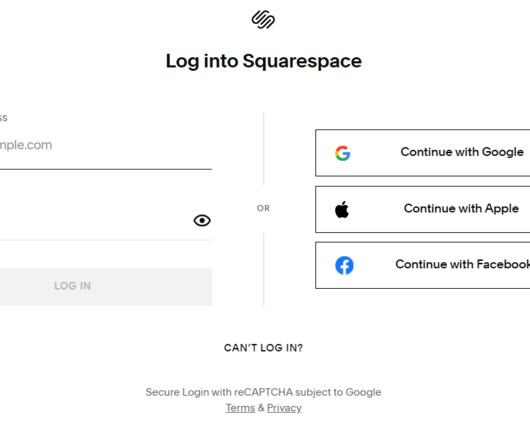
The bot allowed the attackers to use the phished username, password and one-time code to log in as that employee at the real employer website. According to prosecutors, the group mainly sought to steal cryptocurrency from victim companies and their employees. Tylerb was reputed to have fled the United Kingdom after that assault.




































Let's personalize your content