Cryptocurrency Thefts Get Physical
Schneier on Security
APRIL 25, 2025
Long story of a $250 million cryptocurrency theft that, in a complicated chain events, resulted in a pretty brutal kidnapping.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Schneier on Security
APRIL 25, 2025
Long story of a $250 million cryptocurrency theft that, in a complicated chain events, resulted in a pretty brutal kidnapping.

SecureWorld News
APRIL 22, 2025
A sophisticated cybercrime campaign, dubbed Elusive Comet , has been uncovered, in which North Korean threat actors are exploiting Zoom's remote control feature to infiltrate the systems of cryptocurrency professionals. The research behind the discovery was released by Security Alliance , which tracked and analyzed the campaign.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
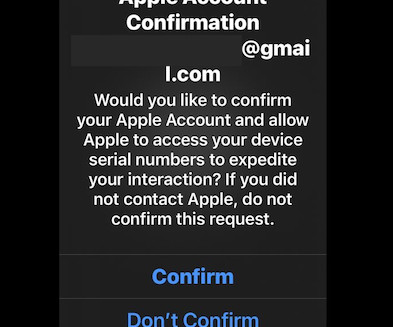
Krebs on Security
JANUARY 7, 2025
KrebsOnSecurity recently told the saga of a cryptocurrency investor named Tony who was robbed of more than $4.7 million in cryptocurrencies from Tony was verify-trezor[.]io. Federal Communications Commission (FCC), as well as those working at the cryptocurrency exchanges Coinbase and Binance. Image: Shutterstock, iHaMoo.

SecureList
OCTOBER 4, 2024
In a recent campaign starting in 2022, unknown malicious actors have been trying to mine cryptocurrency on victims’ devices without user consent; they’ve used large amounts of resources for distribution, but what’s more, used multiple unusual vectors for defense evasion and persistence.

Penetration Testing
AUGUST 22, 2024
In a surprising turn of events, McDonald’s, the global fast-food giant, fell victim to a cyberattack that leveraged the brand’s Instagram account to promote a meme coin called “Grimace.”

The Last Watchdog
JUNE 20, 2018
Cryptojacking, as defined by the Federal Trade Commission , is the use of JavaScript code to capture cryptocurrencies in users’ browsers without asking permission. LW: So cryptocurrency got discovered as the ideal payment vehicle for ransomware. In 2011, total cryptocurrency value was about $10 billion. It was insane.

Malwarebytes
JANUARY 3, 2025
It specializes in stealing credentials stored in most browsers, session cookie theft for platforms like Discord and Steam, and information theft related to cryptocurrency wallets. Part of the Nova Stealers infrastructure is a Discord webhook which allows the criminals to have the server send data to the client whenever a certain event occurs.

Security Affairs
NOVEMBER 6, 2021
Threat actors have stolen $55 million worth of cryptocurrency from the bZx decentralized finance (DeFi) platform. The decentralized finance (DeFi) platforms allow users to borrow/loan and speculate on cryptocurrency price variations. Contacted USDC and requested to freeze USDC in the hackers wallet. Pierluigi Paganini.

Malwarebytes
JUNE 23, 2022
NFT NYC describes itself as “the leading annual non-fungible token event” The 2022 meet-up is the fourth such event to take place. However, a “wallet drainer” is just another way of saying “phishing website” There are three ways the majority of cryptocurrency phishes take place: Airdrop phishing.
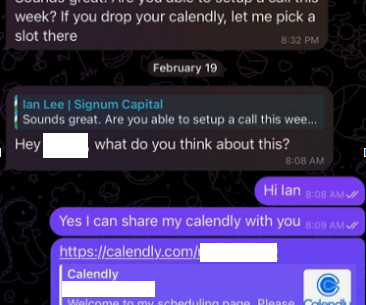
Krebs on Security
FEBRUARY 28, 2024
Malicious hackers are targeting people in the cryptocurrency space in attacks that start with a link added to the target’s calendar at Calendly , a popular application for scheduling appointments and meetings. The attackers impersonate established cryptocurrency investors and ask to schedule a video conference call. capital).

Malwarebytes
AUGUST 26, 2021
In August of 2021, a thief stole about $600 million in cryptocurrencies from The Poly Network. Slightly more than one week later, Japanese cryptocurrency exchange Liquid was hacked and lost $97 million worth of digital coins. They are not available for every cryptocurrency. We can’t answer the first question for you.
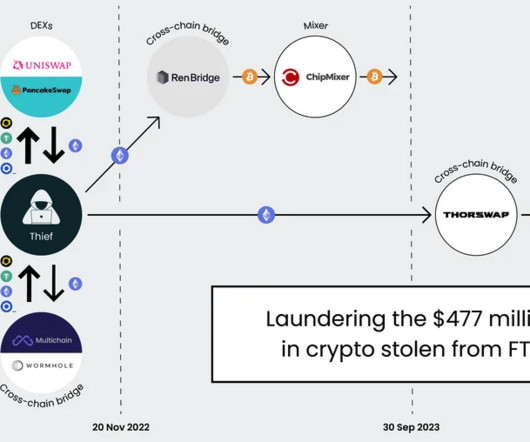
Krebs on Security
FEBRUARY 1, 2024
government did not name the victim organization, but there is every indication that the money was stolen from the now-defunct cryptocurrency exchange FTX , which had just filed for bankruptcy on that same day. A graphic illustrating the flow of more than $400 million in cryptocurrencies stolen from FTX on Nov. 11-12, 2022.
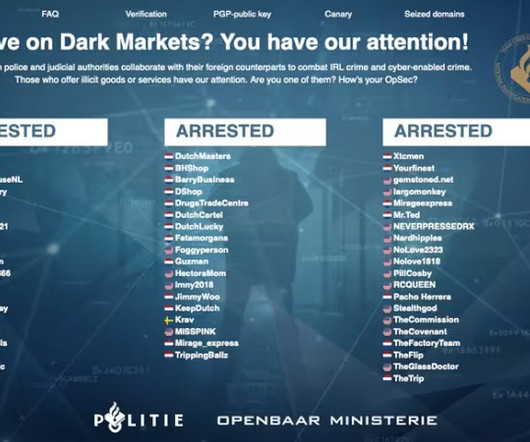
Security Affairs
OCTOBER 14, 2024
“The statement claims that in a “shameful and disgruntled set of events” a lead developer went “rogue”, withdrawing small amounts of Bitcoin (BTC) over a period of just over a month. The authorities also seized two vehicles and €8 million worth of cryptocurrency. ” reads the post published on the website Search Light Cyber.

Malwarebytes
JANUARY 5, 2022
There’s a lot of concern in the cryptocurrency realm at the moment. What is a rug pull in cryptocurrency? A rug pull (or “being rugged”, as they call it in cryptocurrency circles) is not a fun experience. Here’s an example press release in relation to certification of another cryptocurrency platform.

Krebs on Security
JUNE 15, 2024
One of the more popular SIM-swapping channels on Telegram maintains a frequently updated leaderboard of the most accomplished SIM-swappers, indexed by their supposed conquests in stealing cryptocurrency. KrebsOnSecurity sought comment from Mr. Buchanan, and will update this story in the event he responds.

The Last Watchdog
DECEMBER 18, 2024
Dooley Doug Dooley , COO, Data Theorem In 2025, cybersecurity threats will escalate across APIs, cloud setups, supply chains, and cryptocurrency. AI-powered cryptocurrency attacks will automate phishing and exploit vulnerabilities. Supply chain attacks will intensify through poisoned APIs and unchecked software dependencies.
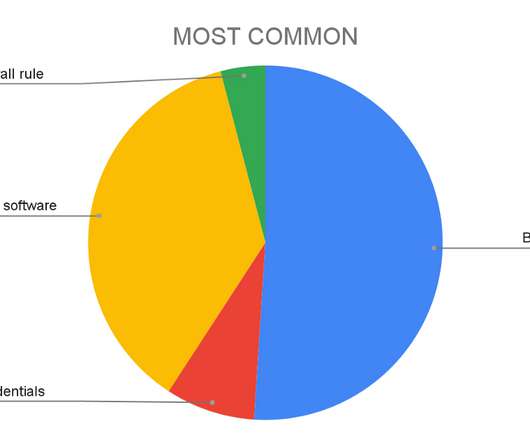
Anton on Security
JULY 7, 2022
this is another gem for me as your security posture may still be solely focused on “critical” assets and data loss, and hence miss the theft of cloud services that you pay for] “In 2022, actors have attempted to commit cloud network resources to mine cryptocurrencies that require network bandwidth. ” [A.C.?—?this

Penetration Testing
OCTOBER 4, 2024
Kaspersky Labs has uncovered a sophisticated cyberattack campaign that abuses an open-source Security Information and Event Management (SIEM) agent to deploy SilentCryptoMiner, a stealthy cryptocurrency mining malware.

Krebs on Security
NOVEMBER 6, 2018
that has been tracking down individuals engaged in unauthorized “SIM swaps” — a complex form of mobile phone fraud that is often used to steal large amounts of cryptocurrencies and other items of value from victims. SIM swapping attacks primarily target individuals who are visibly active in the cryptocurrency space.

SecureList
APRIL 8, 2025
Using the built-in WMIC utility, an event filter is created to trigger a handler every 80 seconds. They achieve this by again using the operating system’s built-in WMIC utility to establish an event filter that triggers the handler every 300 seconds. However, the attackers have found a way to exploit it for automatic startup.

The Last Watchdog
SEPTEMBER 6, 2023
Over time, Bitcoin has become the most widely used cryptocurrency in the world. Wallet backups provide a safety net in the event that your device breaks down, is misplaced, or is stolen. About the essayist: Ronin Ashford is a passionate tech enthusiast and a dedicated cryptocurrency investor. Backup, backup, backup.
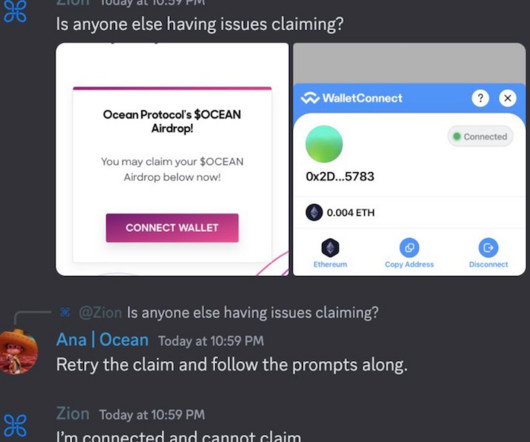
Krebs on Security
MAY 30, 2023
A number of Discord communities focused on cryptocurrency have been hacked this past month after their administrators were tricked into running malicious Javascript code disguised as a Web browser bookmark. On May 9, MetrixCoin reported that its Discord server was hacked, with fake airdrop details pushed to all users.

Heimadal Security
OCTOBER 18, 2021
Following the last week’s White House National Security Council’s virtual meetings on the Counter-Ransomware Initiative event, senior officials from the U.E. What Countries Are Involved […].

SecureList
AUGUST 10, 2022
VileRAT is a Python implant, part of an evasive and highly intricate attack campaign against foreign exchange and cryptocurrency trading companies. org”), and some denote a possible attempt to leverage events of worldwide interest to conduct attack campaigns (such as “weareukrainepeople[.]com”

SecureList
MARCH 5, 2025
Most active of all have been schemes for distributing popular stealers, remote access tools (RATs), Trojans that provide hidden remote access, and miners that harness computing power to mine cryptocurrency. This is a covert miner able to mine multiple cryptocurrencies (ETH, ETC, XMR, RTM and others) using various algorithms.

SecureList
APRIL 25, 2025
Specifically, they can modify cryptocurrency wallet addresses during transfer attempts, replace links in browsers, send arbitrary text messages and intercept replies, and steal login credentials for messaging and social media apps. The downloaded payload attempts to steal the victim’s cryptocurrency using various methods.

Security Affairs
NOVEMBER 4, 2020
Yesterday almost $1 billion worth of cryptocurrency contained in a password-protected BitCoin wallet was moved to another wallet. Someone has transferred almost $1 billion worth of cryptocurrency contained in a password-protected BitCoin wallet to another wallet.
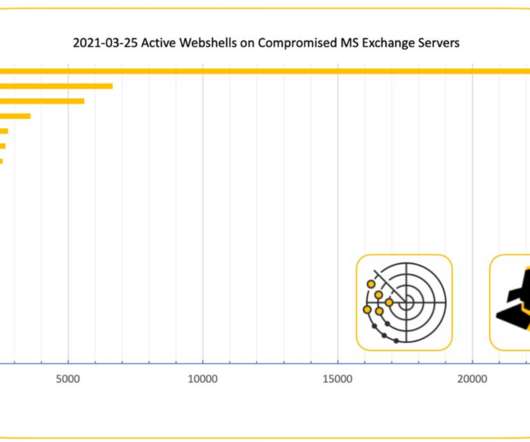
Krebs on Security
MARCH 28, 2021
I first heard about the domain in December 2020, when a reader told me how his entire network had been hijacked by a cryptocurrency mining botnet that called home to it. Here are a few of the more notable examples , although all of those events are almost a decade old. That same list today would be pages long. At Least 30,000 U.S.
Malwarebytes
SEPTEMBER 13, 2023
Yesterday, Apple launched its latest iPhone and Watch models at its massive Wonderlust event. One site uses the Apple brand to host a cryptocurrency scam. To speed up the process of cryptocurrency mass adoption, we decided to run a 5,000 BTC giveaway.
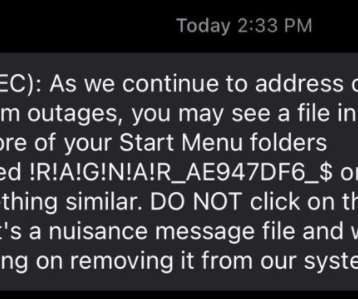
Krebs on Security
SEPTEMBER 15, 2021
” Ragnar Locker is an aggressive ransomware group that typically demands millions of dollars worth of cryptocurrency in ransom payments. It is common for companies to disconnect critical systems in the event of a network intrusion, as part of a larger effort to stop the badness from spreading elsewhere.

SecureList
APRIL 21, 2025
Fake Telegram channels for pirated content and cryptocurrencies. The attackers create Telegram channels with names containing keywords related to cryptocurrencies or pirated content, such as software, movies, etc. When a user searches for such content, the fraudulent channels appear at the top of the search.
Security Affairs
JUNE 18, 2022
Malibot is a new Android malware targeting online banking and cryptocurrency wallet customers in Spain and Italy. F5 Labs researchers spotted a new strain of Android malware, named Malibot, that is targeting online banking and cryptocurrency wallet customers in Spain and Italy. ” continues the report.

Security Affairs
MAY 17, 2021
The price of Bitcoin falls after Elon Musk declared that its company, Tesla, may have sold holdings of the cryptocurrency. We have a long-debated about the possibility that the Bitcoin price could be influenced by threat actors through 51% attacks , but recent events demonstrate that it could be easier to manipulate its value.

Digital Shadows
MARCH 12, 2025
These fake accounts promote fraudulent offers like free event tickets or gambling top-ups, exploiting user trust and luring victims into phishing scams. Cryptocurrencies are difficult to trace, making them a prime target for theft. For example, in February 2025, North Koreas Lazarus Group stole $1.46 billion from the Bybit exchange.

Malwarebytes
DECEMBER 13, 2023
While Zoom is used by millions of people around the world, these campaigns are likely targeting victims who are into cryptocurrencies as well as corporate users, in order to gain access to company networks.

Krebs on Security
OCTOBER 5, 2022
Since then, the response from LinkedIn users and readers has made clear that these phony profiles are showing up en masse for virtually all executive roles — but particularly for jobs and industries that are adjacent to recent global events and news trends. “It’s hit like hell since about January of this year.

Krebs on Security
JANUARY 18, 2021
Gemini said another event that may have contributed to this threat actor shutting down their marketplace is the recent spike in the value of Bitcoin. “JokerStash was an early advocate of Bitcoin and claims to keep all proceeds in this cryptocurrency,” Gemini observed in a blog post.

The Hacker News
JULY 19, 2023
The operation, dubbed "Operation Cookie Monster," resulted in the arrest of 119 people and the seizure of over $1M in cryptocurrency. In light of these events, I'd like to discuss how OSINT On April 5, 2023, the FBI and Dutch National Police announced the takedown of Genesis Market, one of the largest dark web marketplaces.

Security Affairs
OCTOBER 6, 2024
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape. Rhadamanthys Stealer Adds Innovative AI Feature in Version 0.7.0

Security Boulevard
DECEMBER 15, 2022
This paper also touches on the tumultuous year in decentralized finance (DeFi) and cyber angle of one of the year’s most shocking events: the Russian invasion of Ukraine. IV: Cryptocurrency: 2022 Juxtaposed Increasing Cyberattack Activity in Decentralized Finance with Decreasing Market Capitalization.

Security Affairs
JANUARY 8, 2019
The cryptocurrency exchange Coinbase suspended the trading of Ethereum Classic (ETC) after double-spend attacks worth $1.1 The cryptocurrency exchange Coinbase has suspended the trading of Ethereum Classic (ETC) after double-spend attacks that consist in spending digital coins twice. million worth of the digital currency.

SecureWorld News
AUGUST 13, 2021
After pulling off one of the largest cryptocurrency heists ever , the hacker (or hackers) decided to return $600 million worth of assets to the victim, Poly Network, claiming to have only done this "for fun" and that it was "always the plan" to return the crypto. Millions in cryptocurrency locked away.

Security Affairs
FEBRUARY 6, 2025
During the search, the agents seized cryptocurrencies and various computer equipment. “Following these events, and during 2024, various cyberattacks against other entities, public bodies and even Spanish universities took place.” The man was arrested in the town of Calpe (Alicante). ” continues the press release.
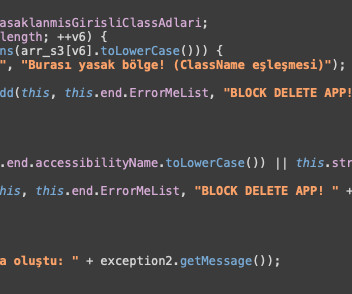
Security Affairs
MARCH 29, 2025
The malware also supports advanced keylogger capabilities by capturing all Accessibility events and screen elements. “Already observed targeting banks in Spain and Turkey and popular cryptocurrency wallets, Crocodilus is clearly engineered to go after high-value assets.” ” ThreatFabric concludes.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content