Google introduces Context-Aware Cyber Threat detection to Chronicle
CyberSecurity Insiders
MARCH 16, 2022
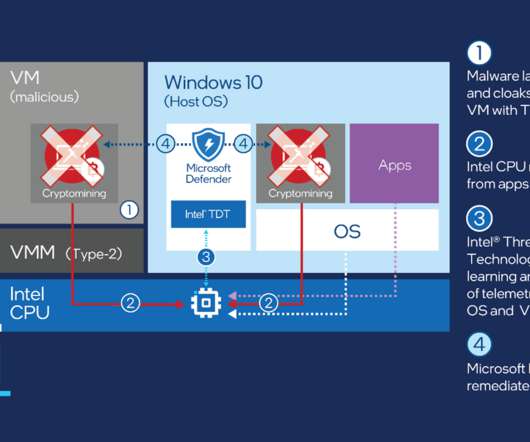
Google Cloud might think of delivering end-to-end security to its enterprise customers and so introduced Context-aware threat detection to its Chronicle platform. The availability of the context-aware threat detection on Chronicle is yet to be made official but is expected to be released by September this year.





















Let's personalize your content