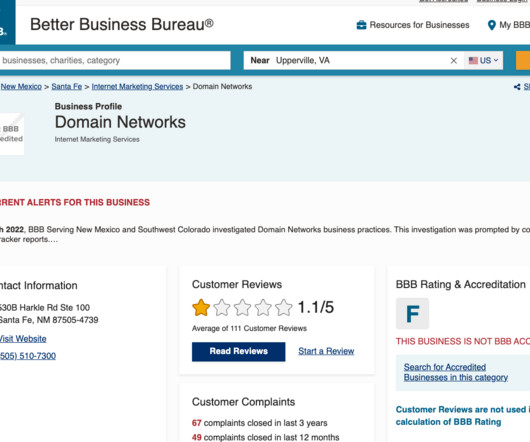
Who’s Behind the DomainNetworks Snail Mail Scam?
Krebs on Security
JULY 3, 2023
com , which says it belongs to a Las Vegas-based Search Engine Optimization (SEO) and digital marketing concern generically named both United Business Service and United Business Services. SammySam_Alon registered at Houzz using an Internet address in Huntsville, Ala. and Renton, Wash. 68.35.149.206).















Let's personalize your content