Report: Recent 10x Increase in Cyberattacks on Ukraine
Krebs on Security
MARCH 11, 2022
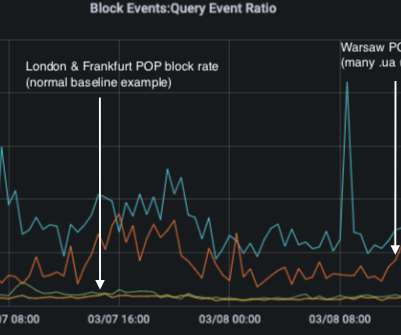
As their cities suffered more intense bombardment by Russian military forces this week, Ukrainian Internet users came under renewed cyberattacks, with one Internet company providing service there saying they blocked ten times the normal number of phishing and malware attacks targeting Ukrainians.













Let's personalize your content