On Chinese-Owned Technology Platforms
Schneier on Security
FEBRUARY 25, 2021
I am a co-author on a report published by the Hoover Institution: “ Chinese Technology Platforms Operating in the United States.”
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Schneier on Security
FEBRUARY 25, 2021
I am a co-author on a report published by the Hoover Institution: “ Chinese Technology Platforms Operating in the United States.”

Lohrman on Security
JANUARY 14, 2024
What were the top government technology and security blogs in 2023? The metrics tell us what cybersecurity and technology infrastructure topics were most popular.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Lohrman on Security
JANUARY 15, 2023
What were the top government technology and security blogs in 2022? The metrics don’t lie, and they tell us what cybersecurity and technology infrastructure topics were most popular.

Anton on Security
DECEMBER 20, 2021
Sometimes great old blog posts are hard to find (especially on Medium ) , so I decided to do a periodic list blog with my favorite posts of the past quarter or so. This covers both Anton on Security and my posts from Google Cloud blog , and our Cloud Security Podcast too ( subscribe ). “A Here is the next one. Do They Matter?”

Lohrman on Security
JANUARY 9, 2022
What were the top government security blog posts in 2021? These metrics tell us what cybersecurity and technology infrastructure topics were most popular in the past year.

Anton on Security
DECEMBER 10, 2021
SOC Technology Failures?—?Do img src: [link] Most failed Security Operations Centers (SOCs) that I’ve seen have not failed due to a technology failure. Hence this blog was born. Let’s stick to mostly technology focused failures. SOC should not spend time / resources managing such technologies. Do They Matter?

Security Boulevard
APRIL 4, 2024
5G technology impacts not just our daily lifestyle but the Internet of Things (IoT) as well. Unlike […] The post Impact of IoT Security for 5G Technology appeared first on Kratikal Blogs. Unlike […] The post Impact of IoT Security for 5G Technology appeared first on Kratikal Blogs.
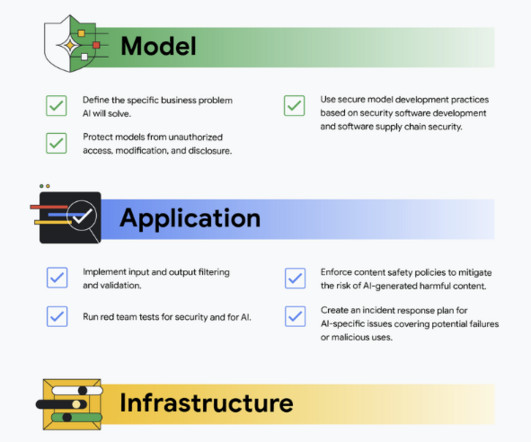
Anton on Security
APRIL 11, 2024
Recently our team has written several papers and blogs focused on securing AI. Here are 5 gen AI security terms busy business leaders should know” defines five key generative AI security terms that busy business leaders should understand to navigate the potential risks and benefits of this technology.

Troy Hunt
JULY 6, 2021
Not for money, not for glory, but for the love of technology and for the joy of seeing it make a difference to people. Speak at a user group? This week marks the beginning of my 11th year as an MVP with the warmly awaited notification hitting my inbox this weekend.

IT Security Guru
JUNE 13, 2024
These incidents underscore the need for organizations to adopt a holistic and layered approach to security, emphasizing continuous monitoring, employee training, and the adoption of cutting-edge security technologies. The post Guest Blog: Ox Security on learning from the Recent GitHub Extortion Campaigns first appeared on IT Security Guru.

Krebs on Security
APRIL 20, 2021
NYSE:IT ] — a $4 billion technology goliath whose analyst reports can move markets and shape the IT industry. As the largest organization dedicated to the analysis of software, Gartner’s network of analysts are well connected to the technology and software industries. Those enticements have mostly fallen on deaf ears.
Krebs on Security
APRIL 10, 2024
The domain mentioned at the beginning of this story — fedetwitter.com — redirects users to the blog of a Japanese technology enthusiast. A user with the handle “amplest0e” appears to have registered space-twitter.com , which Twitter/X users would see as the CEO’s “space-x.com.” com (webex.com).

Krebs on Security
MAY 11, 2020
Diebold Nixdorf , a major provider of automatic teller machines (ATMs) and payment technology to banks and retailers, recently suffered a ransomware attack that disrupted some operations. So far, the crooks behind ProLock haven’t launched their own blog.
Krebs on Security
APRIL 20, 2023
3CX hired incident response firm Mandiant , which released a report on Wednesday that said the compromise began in 2022 when a 3CX employee installed a malware-laced software package distributed via an earlier software supply chain compromise that began with a tampered installer for X_TRADER , a software package provided by Trading Technologies.

Schneier on Security
AUGUST 15, 2023
On Monday, the company said in a blog post that there’s no need to worry about that. It’s a stupid way to run a technological revolution. This is why we need regulation: Zoom updated its Terms of Service in March, spelling out that the company reserves the right to train AI on user data with no mention of a way to opt out.
Krebs on Security
AUGUST 27, 2024
.” Those third-party reports came in late June 2024 from Michael Horka , senior lead information security engineer at Black Lotus Labs , the security research arm of Lumen Technologies , which operates one of the global Internet’s largest backbones. victims and one non-U.S.

Schneier on Security
APRIL 9, 2024
The Board also concludes that Microsoft’s security culture was inadequate and requires an overhaul, particularly in light of the company’s centrality in the technology ecosystem and the level of trust customers place in the company to protect their data and operations.
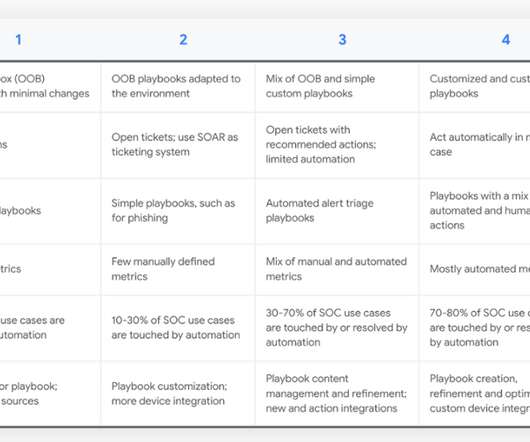
Anton on Security
JUNE 17, 2022
Originally written for a new Chronicle blog. Admittedly many organizations don’t have a SOAR or comparable technology, so they fall outside of this visual. As security orchestration, automation and response (SOAR) adoption continues at a rapid pace , security operations teams have a greater need for a structured planning approach.

Krebs on Security
APRIL 2, 2020
By far the largest group of companies exposing their Zoom meetings are in the technology sector, and include a number of security and cloud technology vendors. We need to look at the risk specific applications pose and help voice a message of how people can leverage technology and be safe. Image: SecKC. This is extreme.
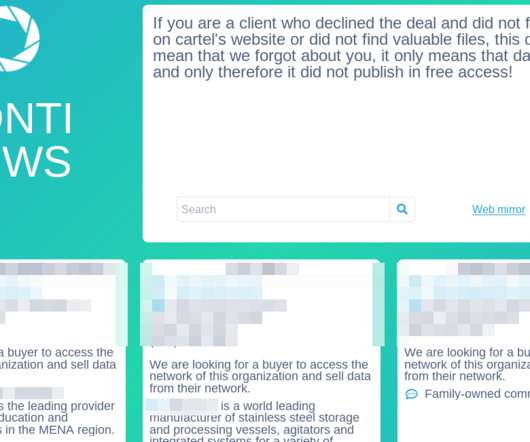
Krebs on Security
OCTOBER 25, 2021
Organizations infected with Conti’s malware who refuse to negotiate a ransom payment are added to Conti’s victim shaming blog, where confidential files stolen from victims may be published or sold. A redacted screenshot of the Conti News victim shaming blog.
Anton on Security
MAY 19, 2022
This is written jointly with Tim Peacock and will eventually appear on the GCP blog. you, the esteemed reader of this blog , do not need this explanation, perhaps, but a typical cloud user might] How is the cloud different compared to the traditional environment? Second, the entire environment around you changes. So, what to do next?

Krebs on Security
MARCH 8, 2021
“We never got a ‘real’ confirmation of the zero-day before the patch was released,” said Dubex’s Chief Technology Officer Jacob Herbst. 29: Trend Micro publishes a blog post about “ Chopper ” web shells being dropped via Exchange flaws.
Krebs on Security
NOVEMBER 4, 2022
“We may warn you about messages that ask you to take the conversation to another platform because that can be a sign of a scam,” the company said in a blog post. “These warnings will also give you the choice to report the content without letting the sender know.” A follow-up story on Oct.
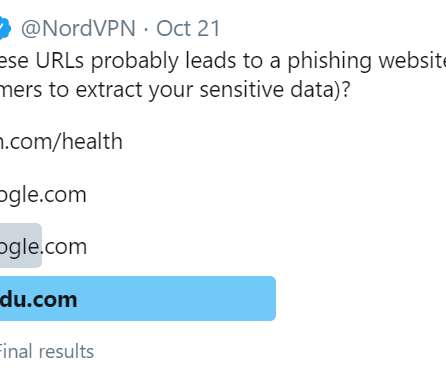
Troy Hunt
OCTOBER 28, 2020
Everything becomes clear(er) if I manually change the font in the browser dev tools to a serif version: The victim I was referring to in the opening of this blog post? Obviously, the image is resized to the width of paragraphs on this blog, give it a click if you want to check it out at 1:1 size.

Krebs on Security
MARCH 8, 2022
Lumen Technologies , an American company that operates one of the largest Internet backbones and carries a significant percentage of the world’s Internet traffic, said today it will stop routing traffic for organizations based in Russia. ru) from the Internet.

Troy Hunt
NOVEMBER 2, 2020
I've had this blog post in draft for quite some time now, adding little bits to it as the opportunity presented itself. Ricky Gervais does an amazing job of explaining what I'm about to delve into so do yourself a favour and spend a minute watching this first: And therein lies the inspiration for the title of this blog.
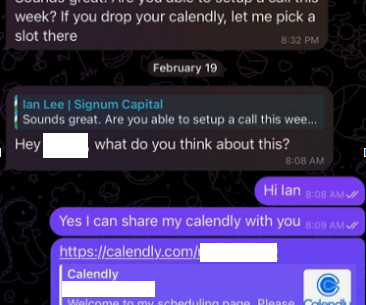
Krebs on Security
FEBRUARY 28, 2024
Doug then messaged the Mr. Lee account on Telegram, who said there was some kind of technology issue with the video platform, and that their IT people suggested using a different meeting link. MacOS computers include X-Protect , Apple’s built-in antivirus technology. “We are actively working on fixing these problems.
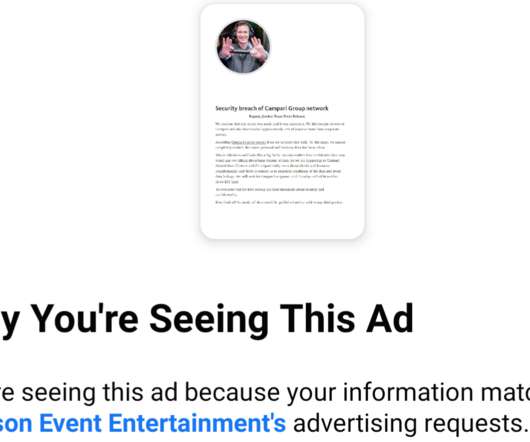
Krebs on Security
NOVEMBER 10, 2020
It’s bad enough that many ransomware gangs now have blogs where they publish data stolen from companies that refuse to make an extortion payment. Fabian Wosar , chief technology officer at computer security firm Emsisoft , said some ransomware groups have become especially aggressive of late in pressuring their victims to pay up.

Krebs on Security
DECEMBER 10, 2020
Conti is one of several cybercriminal groups that maintains a blog which publishes data stolen from victims in a bid to force the negotiation of ransom payments. The gang claims the data published so far represents just 15 percent of the information it offloaded from TSYS before detonating its ransomware inside the company. .
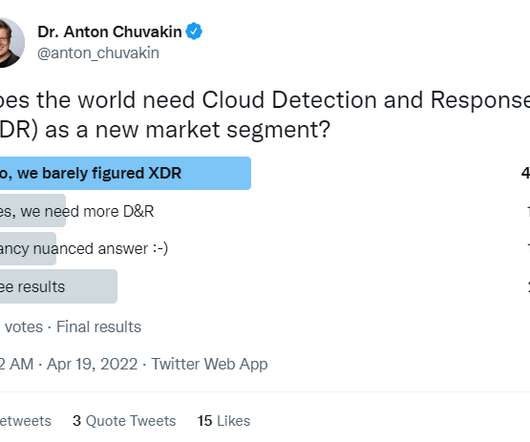
Anton on Security
JUNE 23, 2022
Three roads I see: CDR should exist as a technology and/or market : Cloud is a new realm for threat detection and so old tools/approaches are not ideal; so we need new tools that work well in this new realm. As you can see, I stole some ideas from my original EDR definition so that some useful similarities come out. I did NOT invent the term.

Anton on Security
DECEMBER 22, 2020
Deloitte Security Operations Center (SOC) paper titled “Future of the SOC: Forces shaping modern security operations” ( launch blog , paper PDF ) and promised a series of three more papers covering SOC people, process and technology. and one on technology inside and around the modern SOC. Skills, Not Tiers” (PDF).

The Last Watchdog
MAY 20, 2022
Managed security services (MSS) refer to a service model that enable the monitoring and managing of security technologies, systems, or even software-as-a-service (SaaS) products. Enterprises that embrace IoT technologies to enhance end-user and employee experiences are likely to turn to MSS providers for quick and effective security […].

Anton on Security
SEPTEMBER 3, 2021
I did tend to treat every technology that analyzes log files and perhaps other similar telemetry as a SIEM. Imagine this technology was never born (as SIM and SEM) back in the murky?—?but Anybody would be free to invent a technology to analyze security telemetry (logs, endpoint traces, traffic) and call it whatever they want.

The Last Watchdog
NOVEMBER 8, 2021
M&A invariably creates technology gaps that bad actor’s prey upon. It encompasses identity access and management, privileged access management, password-less management controls, detection and response technology, encryption from the endpoint, through the network and into cloud and on-premises hosting environments.

Security Boulevard
JULY 22, 2024
Emerging at the forefront of technological innovation, Generative AI is reshaping the landscape of cybersecurity defense with groundbreaking advancements. This blog delves into 5 Ways Generative AI is Revolutionizing Cybersecurity Defense and how we protect digital assets.

Anton on Security
JANUARY 10, 2022
Strong thought out processes are sometimes (unfairly) seen as the most boring of the people, processes, and technology triad. We are writing the final paper 4 as we speak :-) Related blog posts: “New Paper: “Future of the SOC: Forces shaping modern security operations”” “New Paper: “Future of the SOC: SOC People?—?Skills,

The Last Watchdog
MAY 19, 2022
Wikipedia uses a CMS for textual entries, blog posts, images, photographs, videos, charts, graphics, and “ talk pages ” that help its many contributors collaborate. If you are using a CMS hosted in your data center, then you need to be sure to promptly apply fixes and patches provided by your technology vendor. (If

Graham Cluley
FEBRUARY 23, 2024
Prescription orders across the United States are reportedly being delayed after a cyber attack impacted a healthcare technology firm that supplies services to pharmacies, including CVS Health. Read more in my article on the Hot for Security blog.

Krebs on Security
JULY 30, 2020
based merchants suggest thieves are exploiting weaknesses in how certain financial institutions have implemented the technology to sidestep key chip card security features and effectively create usable, counterfeit cards. Newer, chip-based cards employ a technology known as EMV that encrypts the account data stored in the chip.

Krebs on Security
OCTOBER 20, 2023
BeyondTrust Chief Technology Officer Marc Maiffret said that alert came more than two weeks after his company alerted Okta to a potential problem. ET: Okta has published a blog post about this incident that includes some “indicators of compromise” that customers can use to see if they were affected. Update, 2:57 p.m.

Krebs on Security
NOVEMBER 17, 2022
Peter is an IT manager for a technology manufacturer that got hit with a Russian ransomware strain called “ Zeppelin ” in May 2020. “These senseless acts of targeting those who are unable to respond are the motivation for this research, analysis, tools, and blog post. .
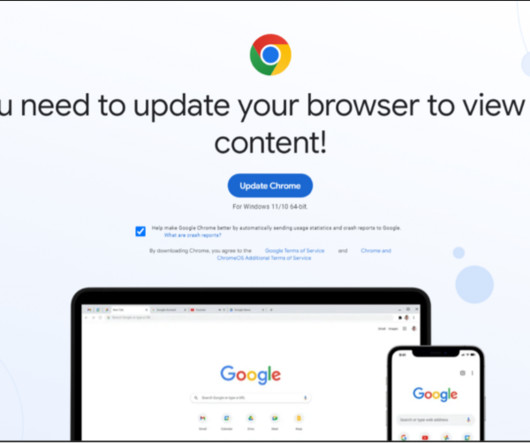
Krebs on Security
OCTOBER 18, 2023
In August 2023, security researcher Randy McEoin blogged about a scam he dubbed ClearFake , which uses hacked WordPress sites to serve visitors with a page that claims you need to update your browser before you can view the content. Previously, the group had stored its malicious update files on Cloudflare, Guard.io

Jane Frankland
APRIL 17, 2024
As technology weaves deeper into our lives, the swift exchange of information has become our reality. I invite you to join me on a journey to understand the intricacies of secure transactions in our digitised world, where trust and technological innovation converge for a safer, more resilient digital future.

Krebs on Security
DECEMBER 14, 2020
A blog post by Microsoft says the attackers were able to add malicious code to software updates provided by SolarWinds for Orion users. “The victims have included government, consulting, technology, telecom and extractive entities in North America, Europe, Asia and the Middle East,” the company’s analysts wrote.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content