On Chinese-Owned Technology Platforms
Schneier on Security
FEBRUARY 25, 2021
I am a co-author on a report published by the Hoover Institution: “ Chinese Technology Platforms Operating in the United States.”
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Schneier on Security
FEBRUARY 25, 2021
I am a co-author on a report published by the Hoover Institution: “ Chinese Technology Platforms Operating in the United States.”

Troy Hunt
DECEMBER 30, 2018
This is part of the opening monologue of the Ozark series and when I first heard it, I immediately stopped the show and dropped it into this blog post. So here it is - 10 Personal Financial Lessons for Technology Professionals. Money is, at its essence, that measure of a man’s choices. Intro: This Industry Rocks! Banking is below that.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Last Watchdog
NOVEMBER 15, 2021
Such a transformation however, comes with its own set of risks. Misleading information has emerged as one of the leading cyber risks in our society, affecting political leaders, nations, and people’s lives, with the COVID-19 pandemic having only made it worse. So, how do organizations prepare against such threats?

The Last Watchdog
AUGUST 29, 2023
Here’s what you should know about the risks, what aviation is doing to address those risks, and how to overcome them. It is difficult to deny that cyberthreats are a risk to planes. Risks delineated Still, there have been many other incidents since. There was another warning from the U.S.
Anton on Security
APRIL 11, 2024
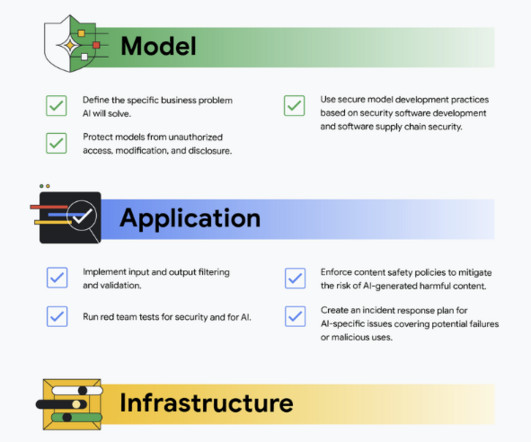
Recently our team has written several papers and blogs focused on securing AI. Here are 5 gen AI security terms busy business leaders should know” defines five key generative AI security terms that busy business leaders should understand to navigate the potential risks and benefits of this technology.

The Last Watchdog
JANUARY 2, 2024
In today’s digital landscape, organizations face numerous challenges when it comes to mitigating cyber risks. Related: How AI is transforming DevOps The constant evolution of technology, increased connectivity, and sophisticated cyber threats pose significant challenges to organizations of all sizes and industries.

The Last Watchdog
MAY 5, 2022
Let’s walk through some practical steps organizations can take today, implementing zero trust and remote access strategies to help reduce ransomware risks: •Obvious, but difficult – get end users to stop clicking unknown links and visiting random websites that they know little about, an educational challenge. Best practices.

The Last Watchdog
OCTOBER 10, 2022
As digital technologies become more immersive and tightly integrated with our daily lives, so too do the corresponding intrusive attacks on user privacy. Instead, it is a first step towards solving a dangerous technological disparity: despite posing an unprecedented degree of privacy risk, VR currently lacks even the most basic privacy tools.

The Last Watchdog
JANUARY 8, 2023
Smarter security to me broadly refers to relentlessly focusing on fundamentals while maturing the program, making sure your risk posture aligns with your business strategy. Business initiatives demand faster, more efficient outcomes and technology responds. Complexity challenge. Managed solutions can help.

CSO Magazine
JUNE 9, 2023
Google, owner of the generative AI chatbot Bard and parent company of AI research lab DeepMind, said a framework across the public and private sectors is essential for making sure that responsible actors safeguard the technology that supports AI advancements so that when AI models are implemented, they’re secure-by-default.

Krebs on Security
JULY 30, 2020
based merchants suggest thieves are exploiting weaknesses in how certain financial institutions have implemented the technology to sidestep key chip card security features and effectively create usable, counterfeit cards. Newer, chip-based cards employ a technology known as EMV that encrypts the account data stored in the chip.

IT Security Guru
JUNE 13, 2024
These incidents underscore the need for organizations to adopt a holistic and layered approach to security, emphasizing continuous monitoring, employee training, and the adoption of cutting-edge security technologies. The post Guest Blog: Ox Security on learning from the Recent GitHub Extortion Campaigns first appeared on IT Security Guru.

Krebs on Security
MARCH 8, 2022
Lumen Technologies , an American company that operates one of the largest Internet backbones and carries a significant percentage of the world’s Internet traffic, said today it will stop routing traffic for organizations based in Russia. However, we are taking steps to immediately stop business in the region.”

Responsible Cyber
NOVEMBER 25, 2024
However, this dependence also introduces significant risks. Managing these risks—whether they stem from cybersecurity vulnerabilities, regulatory compliance, or operational disruptions—has become a top priority for organizations worldwide. Top Tools Provenance: A blockchain-based platform designed for supply chain transparency.

Schneier on Security
DECEMBER 19, 2023
” Willison expands this in a blog post , which I strongly recommend reading in its entirety. We risk letting companies get away with real misconduct because we incorrectly believed in conspiracy theories. On a personal level we risk losing out on useful tools. Privacy is important, and very easily misunderstood.

Jane Frankland
APRIL 17, 2024
As technology weaves deeper into our lives, the swift exchange of information has become our reality. Without upholding digital trust, with every click, we not only risk security breaches, fraud and the misuse of our data but one’s own company’s reputation and the very foundation of our business operations.

SecureWorld News
OCTOBER 16, 2024
With the increasing adoption of smart home technologies, ensuring robust security measures for such devices is crucial to prevent hackers from gaining control or accessing private information. Smart home users should stay vigilant, update device software regularly, and implement network security best practices to mitigate risks.

The Last Watchdog
MAY 20, 2022
Managed security services (MSS) refer to a service model that enable the monitoring and managing of security technologies, systems, or even software-as-a-service (SaaS) products. It’s worth noting that there are a few: •Cybersecurity breaches may originate from the vendor, putting the host company’s information at risk. Kjaersgaard.

The Last Watchdog
NOVEMBER 8, 2021
M&A invariably creates technology gaps that bad actor’s prey upon. It encompasses identity access and management, privileged access management, password-less management controls, detection and response technology, encryption from the endpoint, through the network and into cloud and on-premises hosting environments.
Krebs on Security
NOVEMBER 4, 2022
LinkedIn also said it is adding a warning to some LinkedIn messages that include high-risk content, or that try to entice the user into taking the conversation to another platform (like WeChat). “These warnings will also give you the choice to report the content without letting the sender know.” A follow-up story on Oct.

Centraleyes
MARCH 25, 2024
Let’s discuss an acronym reshaping the business world: Vendor Risk Management , or VRM. With supply chains extending across multiple regions and involving numerous third-party vendors, organizations face unprecedented challenges in managing vendor risks effectively. What risks are you facing?

The Last Watchdog
MAY 16, 2022
The same technologies that make supply chains faster and more effective also threaten their cybersecurity,” writes David Lukic , a privacy, security, and compliance consultant. The inherent complexity of the supply chain for modern technology is a reason why so many cybercrime attempts have been successful.

The Last Watchdog
JANUARY 9, 2024
Augmented reality (AR) and virtual reality (VR) technologies provide intriguing opportunities for immersive and interactive experiences in cybersecurity training. Related: GenAI’ impact on DevSecOps Here’s how these technologies can bridge learning gaps in cybersecurity awareness and enhance the overall training experience.

The Last Watchdog
APRIL 3, 2023
Related: Taking a risk-assessment approach to VM Unlike a typical cyber attack that exploits a software vulnerability, recent cyber attacks exploit other security risks, such as misconfigurations, security deviations, and posture anomalies. But VM vendors tend to focus more on software vulnerabilities and leave out everything else.

Krebs on Security
APRIL 2, 2020
By far the largest group of companies exposing their Zoom meetings are in the technology sector, and include a number of security and cloud technology vendors. We need to look at the risk specific applications pose and help voice a message of how people can leverage technology and be safe. Image: SecKC. This is extreme.

Responsible Cyber
NOVEMBER 25, 2024
Effective from January 2025, DORA mandates that financial institutions implement robust measures to manage Information and Communication Technology (ICT) risks, with a significant emphasis on Third-Party Risk Management (TPRM).

The Last Watchdog
SEPTEMBER 25, 2023
Nonprofits are equally at risk, and often lack cybersecurity measures. Given the risk involved, small businesses and nonprofits must consider prioritizing cybersecurity policies and practices to stay protected, retain customers, and remain successful. Security places a crucial role in your technology.
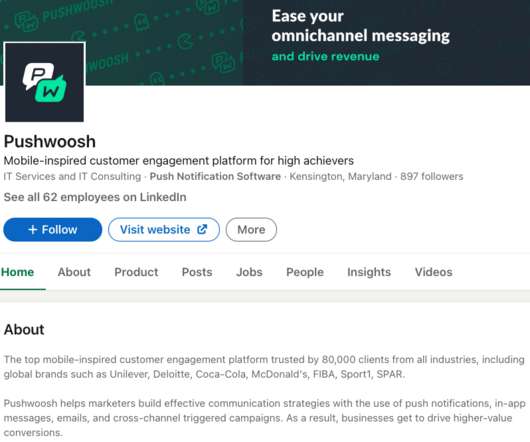
Krebs on Security
NOVEMBER 28, 2022
Edwards said Pushwoosh began as Arello-Mobile , and for several years the two co-branded — appearing side by side at various technology expos. In a blog post responding to the Reuters story, Pushwoosh said it is a privately held company incorporated under the state laws of Delaware, USA, and that Pushwoosh Inc. ” GOV 311.

The Last Watchdog
JANUARY 27, 2022
And with technology playing a huge part in simplifying and enabling integration activities between two distinct organizations, it is these very systems that attackers are looking to exploit. They can be divided into two categories: Pre-Close Risks. Post-Close Risks. Lack of documented evidence. Hybrid Integration.

The Last Watchdog
MARCH 7, 2022
An efficient VM solution will reduce the time and manpower resources required to maintain an effective cybersecurity infrastructure, thereby reducing the risk for enterprises. Despite this, many organizations manage incomplete or out-of-date VM technologies to protect critical data assets.

The Last Watchdog
MAY 19, 2022
Wikipedia uses a CMS for textual entries, blog posts, images, photographs, videos, charts, graphics, and “ talk pages ” that help its many contributors collaborate. If you are using a CMS hosted in your data center, then you need to be sure to promptly apply fixes and patches provided by your technology vendor. (If

The Last Watchdog
AUGUST 8, 2022
Our technological world is advancing at dizzying speeds. Add in an increasing focus on data becoming a crucial enterprise asset—as well as the introduction of countless database and analytical tools, digital twins, artificial intelligence, and machine learning—and we are dealing with unprecedented technical complexities and risk.

The Last Watchdog
DECEMBER 5, 2019
I’ve been paying close attention to privacy and cybersecurity since 2004, first as a technology reporter at USA TODAY, then as Editor-In-Chief of ThirdCertainty.com, a corporate-underwritten news analysis blog. I’ve never done stories to win awards. That usually happens every time I publish a story under my byline.

Cisco Security
APRIL 1, 2024
Blockchain technology has experienced remarkable adoption in recent years, driven by its use across a broad spectrum of institutions, governments, retail investors, and users. However, this surge in… Read more on Cisco Blogs Blockchain adoption and crypto investments are peaking, along with scams.

The Last Watchdog
MARCH 25, 2024
The National Institute of Standards and Technology (NIST) has updated their widely used Cybersecurity Framework (CSF) — a free respected landmark guidance document for reducing cybersecurity risk. It seeks to establish and monitor your company’s cybersecurity risk management strategy, expectations, and policy. The CSF 2.0

Daniel Miessler
SEPTEMBER 27, 2020
The Difference Between Threats and Risks. The problem we have as humans is that opportunity is usually coupled with risk, so the question is one of which opportunities should you take and which should you pass on. And If you want to take a certain risk, which controls should you put in place to keep the risk at an acceptable level?
Troy Hunt
MARCH 10, 2021
link] - @troyhunt think this one is an interesting read, maybe worthy of a blog post. The Mirai botnet taught us how far vulnerable IoT devices can be pushed and let's face it, those of us running Home Assistant are putting a lot of IoT stuff in the network that creates some level of risk, we just don't know how much risk.

The Last Watchdog
DECEMBER 16, 2021
After all, a malicious actor only needs a few minutes of time with a privileged account to take over the entire directory, and there are volumes of exploitable identity risks at every organization. Prior to his career in information technology, Lance was a professional mountain guide. The ascendency of CISOs.

The Last Watchdog
SEPTEMBER 11, 2023
Related: Neutralizing insider threats This pervasive problem extends beyond traditional notions of fraud, encompassing both insider threats and external risks arising from partnerships, competitors, and poor IP management. Organizations have access to ample data; the key lies in adopting suitable technology to extract its value.

Security Boulevard
JANUARY 27, 2023
However, as with any technology, there are also risks associated with the use of AI in cybersecurity. Artificial intelligence (AI) is rapidly becoming a powerful tool in the cybersecurity landscape, with the potential to revolutionize the way we detect and respond to cyber threats.

The Last Watchdog
DECEMBER 2, 2021
In fact, Gartner forecasts that global spending on information security and risk management services will reach $150.4 Today’s technology and security strategies are falling short at keeping a company’s most critical asset – data itself – safe. In the end, the issue is clear — our data is at risk. billion this year.

Responsible Cyber
NOVEMBER 25, 2024
Universities today rely heavily on third-party entities to support their operations, ranging from academic services to administrative support and technological infrastructure. However, their involvement introduces a spectrum of risks, such as data breaches, compliance violations, and operational failures. Canvas, Blackboard).
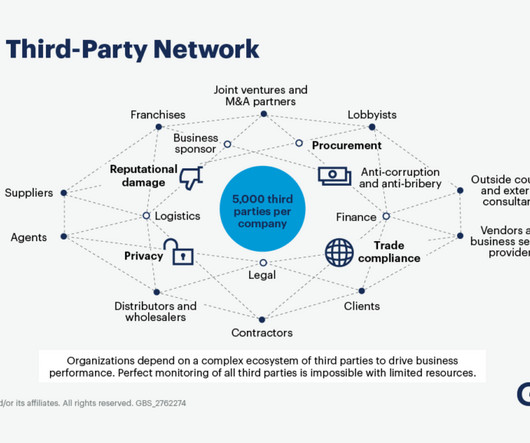
Responsible Cyber
NOVEMBER 23, 2024
However, with every partnership comes potential risk. As networks expand to include third, fourth, and even fifth parties, the complexities of managing these risks multiply. For CCEOs and senior leaders, effective third-party risk management (TPRM) is not just a necessity—it’s a strategic imperative.

The Last Watchdog
APRIL 13, 2022
While you might think that these actors are interested in government and defense information, their operations prove they are interested in much more – including software development and information technology, data analytics, and logistics. Educate your employees on threats and risks such as phishing and malware.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content