On Chinese-Owned Technology Platforms
Schneier on Security
FEBRUARY 25, 2021
I am a co-author on a report published by the Hoover Institution: “ Chinese Technology Platforms Operating in the United States.”
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Schneier on Security
FEBRUARY 25, 2021
I am a co-author on a report published by the Hoover Institution: “ Chinese Technology Platforms Operating in the United States.”

Schneier on Security
OCTOBER 9, 2023
Reading the headlines, one would hope that the rapid gains in AI technology have also brought forth a unifying realization of the risks—and the steps we need to take to mitigate them. Some are concerned about far-future risks that sound like science fiction. AI could destroy humanity or pose a risk on par with nukes.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Responsible Cyber
NOVEMBER 25, 2024
Effective from January 2025, DORA mandates that financial institutions implement robust measures to manage Information and Communication Technology (ICT) risks, with a significant emphasis on Third-Party Risk Management (TPRM).

Jane Frankland
APRIL 25, 2025
But if we switch our focus to the world of technology, we seei a starkly different picturea landscape increasingly shaped by control, compliance, and automation. The rapid advancement of technology, particularly in AI and automation, is transforming the way we interact with the digital world.
Responsible Cyber
NOVEMBER 23, 2024
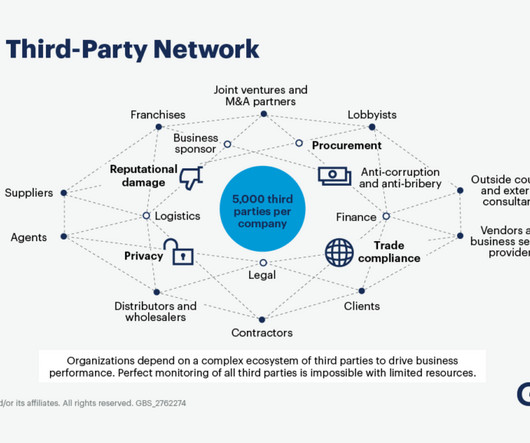
However, with every partnership comes potential risk. As networks expand to include third, fourth, and even fifth parties, the complexities of managing these risks multiply. For CCEOs and senior leaders, effective third-party risk management (TPRM) is not just a necessity—it’s a strategic imperative.

Troy Hunt
DECEMBER 30, 2018
This is part of the opening monologue of the Ozark series and when I first heard it, I immediately stopped the show and dropped it into this blog post. So here it is - 10 Personal Financial Lessons for Technology Professionals. Money is, at its essence, that measure of a man’s choices. Intro: This Industry Rocks! Banking is below that.

The Last Watchdog
NOVEMBER 15, 2021
Such a transformation however, comes with its own set of risks. Misleading information has emerged as one of the leading cyber risks in our society, affecting political leaders, nations, and people’s lives, with the COVID-19 pandemic having only made it worse. So, how do organizations prepare against such threats?

The Last Watchdog
AUGUST 29, 2023
Here’s what you should know about the risks, what aviation is doing to address those risks, and how to overcome them. It is difficult to deny that cyberthreats are a risk to planes. Risks delineated Still, there have been many other incidents since. There was another warning from the U.S.

Centraleyes
DECEMBER 16, 2024
As we approach 2025, the cybersecurity landscape is evolving rapidly, shaped by technological advancements, regulatory shifts, and emerging threats. Tools like ChatGPT and Bard, powered by large language models, showcase how generative AI transforms business processesbut they also pose new risks. The challenge?

BH Consulting
APRIL 16, 2025
She clearly emphasised that although retail, finance and operational technologies are rapidly adopting AI, human expertise remains irreplaceable. Dr. Ng emphasised the balancing act between innovation and risk. Cloud calls for cooperation in a changed risk landscape Has computing really changed with the cloud?
Anton on Security
APRIL 11, 2024
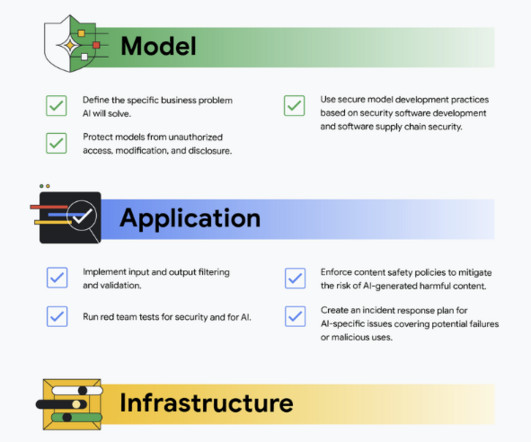
Recently our team has written several papers and blogs focused on securing AI. Here are 5 gen AI security terms busy business leaders should know” defines five key generative AI security terms that busy business leaders should understand to navigate the potential risks and benefits of this technology.

Security Boulevard
MARCH 21, 2025
Check out key findings and insights from the Tenable Cloud AI Risk Report 2025. 1 - Tenable: Orgs using AI in the cloud face thorny cyber risks Using AI tools in cloud environments? 1 - Tenable: Orgs using AI in the cloud face thorny cyber risks Using AI tools in cloud environments?

The Last Watchdog
MAY 5, 2022
Let’s walk through some practical steps organizations can take today, implementing zero trust and remote access strategies to help reduce ransomware risks: •Obvious, but difficult – get end users to stop clicking unknown links and visiting random websites that they know little about, an educational challenge. Best practices.

The Last Watchdog
JANUARY 2, 2024
In today’s digital landscape, organizations face numerous challenges when it comes to mitigating cyber risks. Related: How AI is transforming DevOps The constant evolution of technology, increased connectivity, and sophisticated cyber threats pose significant challenges to organizations of all sizes and industries.

The Last Watchdog
OCTOBER 10, 2022
As digital technologies become more immersive and tightly integrated with our daily lives, so too do the corresponding intrusive attacks on user privacy. Instead, it is a first step towards solving a dangerous technological disparity: despite posing an unprecedented degree of privacy risk, VR currently lacks even the most basic privacy tools.

The Last Watchdog
JANUARY 8, 2023
Smarter security to me broadly refers to relentlessly focusing on fundamentals while maturing the program, making sure your risk posture aligns with your business strategy. Business initiatives demand faster, more efficient outcomes and technology responds. Complexity challenge. Managed solutions can help.

The Last Watchdog
APRIL 22, 2025
security professionals, highlighting a few worrisome findings: Deepfake risks increasingly target vulnerable board members and executives. As AI technology advances, attackers are shifting their focus from technical exploits to human emotions using deeply personal and well-orchestrated social engineering tactics.

IT Security Guru
FEBRUARY 25, 2025
In this blog, well look at the concept of MFA fatigue, how bad actors exploit it, and what entities can do to strengthen defences against this cunning tactic. MFA fatigue is simply a natural evolution in their tacticstargeting the human element instead of trying to bypass the technology itself.

Responsible Cyber
NOVEMBER 25, 2024
However, this dependence also introduces significant risks. Managing these risks—whether they stem from cybersecurity vulnerabilities, regulatory compliance, or operational disruptions—has become a top priority for organizations worldwide. Top Tools Provenance: A blockchain-based platform designed for supply chain transparency.

Jane Frankland
OCTOBER 25, 2024
As ITDMs, CISOs and cyber risk owners this is our dream scenario, and he got me thinking. It’s a subtle shift in focus, and requires a fundamental change in how we, as ITDMs, CISOs and cyber risk owners view and action resilience—not as a one-time project, but as an ongoing programme that provides strategic advantage.
Security Boulevard
APRIL 18, 2025
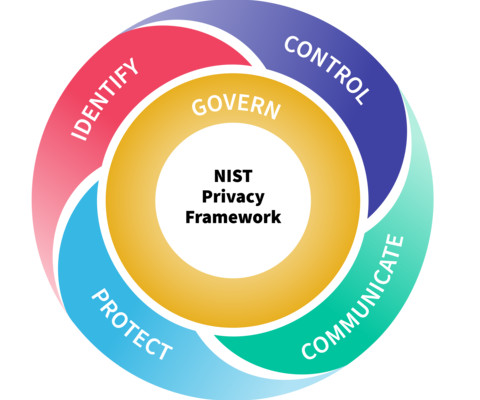
Plus, learn why code-writing GenAI tools can put developers at risk of package-confusion attacks. National Institute of Standards and Technology (NIST) released a draft update of its Privacy Framework (PFW) that more closely interconnects it with the popular Cybersecurity Framework (CSF) , which was updated in 2024. This week, the U.S.

Webroot
JANUARY 13, 2025
Anything less, and you risk leaving customers vulnerable to costly breaches. This ongoing evolution demands continuous investment in both training for an MSPs security team and the latest technologies to effectively detect and mitigate new types of threats. Loss of sensitive data, with potential regulatory fines to follow.

IT Security Guru
JUNE 13, 2024
These incidents underscore the need for organizations to adopt a holistic and layered approach to security, emphasizing continuous monitoring, employee training, and the adoption of cutting-edge security technologies. The post Guest Blog: Ox Security on learning from the Recent GitHub Extortion Campaigns first appeared on IT Security Guru.

Schneier on Security
DECEMBER 19, 2023
” Willison expands this in a blog post , which I strongly recommend reading in its entirety. We risk letting companies get away with real misconduct because we incorrectly believed in conspiracy theories. On a personal level we risk losing out on useful tools. Privacy is important, and very easily misunderstood.

Krebs on Security
JULY 30, 2020
based merchants suggest thieves are exploiting weaknesses in how certain financial institutions have implemented the technology to sidestep key chip card security features and effectively create usable, counterfeit cards. Newer, chip-based cards employ a technology known as EMV that encrypts the account data stored in the chip.

Digital Shadows
NOVEMBER 12, 2024
DRP Insights: Credential Exposure Makes Up 75% of Alerts Construction companies are increasingly vulnerable to opportunistic attacks, with credential exposure incidents now accounting for 75% of all GreyMatter Digital Risk Protection (DRP) alerts for the sector.

Malwarebytes
FEBRUARY 26, 2025
It wasnt until a few weeks later, when a Google security blog titled 5 new protections on Google Messages to help keep you safe revealed that one of the new protections was designed to introduce Sensitive Content Warnings for Google Messages. It included a new service called Android System SafetyCore.

Jane Frankland
FEBRUARY 7, 2025
But as a CISO or cyber risk owner, it’s not just about locking down sensitive informationits about doing it without slowing down your people. This is where the real opportunity lies, and what Im exploring in this blog. For CISOs and cyber risk owners, this isnt just a riskits a gamble no one can afford to take.
Krebs on Security
NOVEMBER 4, 2022
LinkedIn also said it is adding a warning to some LinkedIn messages that include high-risk content, or that try to entice the user into taking the conversation to another platform (like WeChat). “These warnings will also give you the choice to report the content without letting the sender know.” A follow-up story on Oct.

SecureWorld News
OCTOBER 16, 2024
With the increasing adoption of smart home technologies, ensuring robust security measures for such devices is crucial to prevent hackers from gaining control or accessing private information. Smart home users should stay vigilant, update device software regularly, and implement network security best practices to mitigate risks.

Krebs on Security
MARCH 8, 2022
Lumen Technologies , an American company that operates one of the largest Internet backbones and carries a significant percentage of the world’s Internet traffic, said today it will stop routing traffic for organizations based in Russia. However, we are taking steps to immediately stop business in the region.”
Malwarebytes
NOVEMBER 4, 2024
In this blog post, we take a look at how criminals are abusing Bing and stay under the radar at the same time while also bypassing advanced security features such as two-factor authentication. The idea is about creating content that looks real, like a blog, but with malicious intent (monetization or other). com info-blog-news[.]com

The Last Watchdog
MAY 20, 2022
Managed security services (MSS) refer to a service model that enable the monitoring and managing of security technologies, systems, or even software-as-a-service (SaaS) products. It’s worth noting that there are a few: •Cybersecurity breaches may originate from the vendor, putting the host company’s information at risk. Kjaersgaard.

Adam Shostack
JANUARY 2, 2025
The board has clearly given Microsoft the benefit of the doubt, pushed them to correct visible failings like the blog post, and (reading between the lines) pushed them to reach a conclusion about the breakin. Running 46 parallel teams is an interesting approach, with some risks of silos. Page iv) [Happy to help all y'all!]

The Last Watchdog
NOVEMBER 8, 2021
M&A invariably creates technology gaps that bad actor’s prey upon. It encompasses identity access and management, privileged access management, password-less management controls, detection and response technology, encryption from the endpoint, through the network and into cloud and on-premises hosting environments.
Krebs on Security
MAY 18, 2022
In a letter to FTC Chair Lina Khan , the Senators charge that ID.me’s CEO Blake Hall has offered conflicting statements about how his company uses the facial scan data it collects on behalf of the federal government and many states that use the ID proofing technology to screen applicants for unemployment insurance.

Centraleyes
MARCH 17, 2025
Every organization faces risks that threaten its objectives, assets, and operations. A risk assessment is the foundation for identifying, analyzing, and prioritizing these risks. Understanding the basics of risk assessment is the first step in building a resilient and proactive strategy to mitigate risks and vulnerabilities.

Security Boulevard
APRIL 15, 2025
Risk to CVE program With the report that the funding for the CVE program is potentially set to expire on April 16, the biggest concern stems from the fact that CVE Numbering Authorities, or CNAs, will no longer be able to reserve and assign CVEs for newly discovered vulnerabilities.

Jane Frankland
APRIL 17, 2024
As technology weaves deeper into our lives, the swift exchange of information has become our reality. Without upholding digital trust, with every click, we not only risk security breaches, fraud and the misuse of our data but one’s own company’s reputation and the very foundation of our business operations.

The Last Watchdog
MAY 16, 2022
The same technologies that make supply chains faster and more effective also threaten their cybersecurity,” writes David Lukic , a privacy, security, and compliance consultant. The inherent complexity of the supply chain for modern technology is a reason why so many cybercrime attempts have been successful.

Webroot
DECEMBER 9, 2024
By offering OpenText MDR to your MSP clients, you gain access to skilled security experts and advanced technology infrastructurewithout the complexity and cost of building it all in-house. You get the best of both worldscutting-edge technology and dedicated human oversight that augments your MSP team.

Security Boulevard
MARCH 31, 2025
In this blog, we share three challenges cybersecurity leaders say exposure management helps them solve. The core cybersecurity discipline is evolving into exposure management , which is built on a broader, more strategic approach to identifying, prioritizing and mitigating risk.

The Last Watchdog
APRIL 3, 2023
Related: Taking a risk-assessment approach to VM Unlike a typical cyber attack that exploits a software vulnerability, recent cyber attacks exploit other security risks, such as misconfigurations, security deviations, and posture anomalies. But VM vendors tend to focus more on software vulnerabilities and leave out everything else.

Krebs on Security
APRIL 2, 2020
By far the largest group of companies exposing their Zoom meetings are in the technology sector, and include a number of security and cloud technology vendors. We need to look at the risk specific applications pose and help voice a message of how people can leverage technology and be safe. Image: SecKC. This is extreme.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content