Securing Multicloud Environments with Cisco Secure Firewall Threat Defense on Alkira Cloud
Cisco Security
DECEMBER 14, 2021
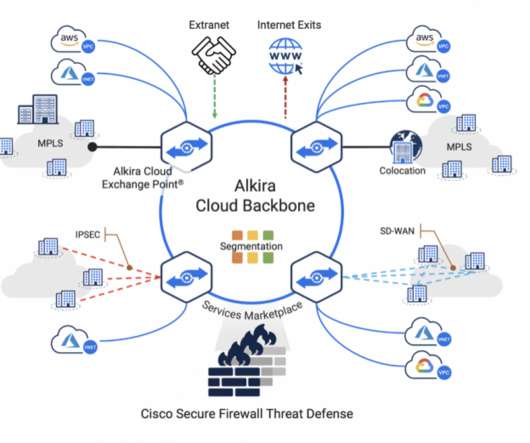
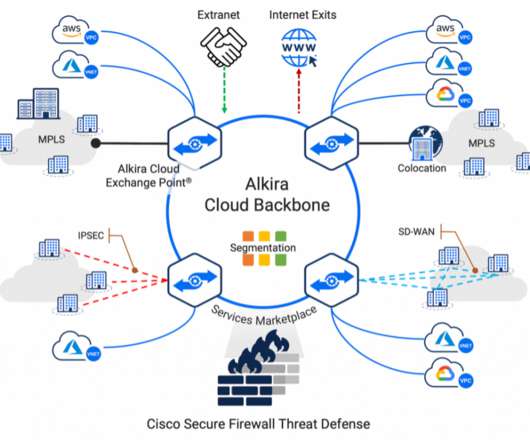
Cisco Secure Firewall Threat Defense provides unmatched security controls such as stateful firewalling, Snort3 IPS, URL filtering, malware defense, application visibility and control, and more. Cisco Secure Firewall Threat Defense 7.1 will be available on Alkira’s service marketplace early 2022.










































Let's personalize your content