Matthew Green on Telegram’s Encryption
Schneier on Security
AUGUST 28, 2024
Matthew Green wrote a really good blog post on what Telegram’s encryption is and is not.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Schneier on Security
AUGUST 28, 2024
Matthew Green wrote a really good blog post on what Telegram’s encryption is and is not.

Schneier on Security
JUNE 11, 2021
For three years, the Federal Bureau of Investigation and the Australian Federal Police owned and operated a commercial encrypted phone app, called AN0M, that was used by organized crime around the world. We’ve seen law enforcement take over encrypted apps before: for example, EncroChat.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Schneier on Security
FEBRUARY 26, 2024
Apple announced PQ3 , its post-quantum encryption standard based on the Kyber secure key-encapsulation protocol, one of the post-quantum algorithms selected by NIST in 2022. There’s a lot of detail in the Apple blog post , and more in Douglas Stabila’s security analysis. I am of two minds about this.
Troy Hunt
SEPTEMBER 3, 2020
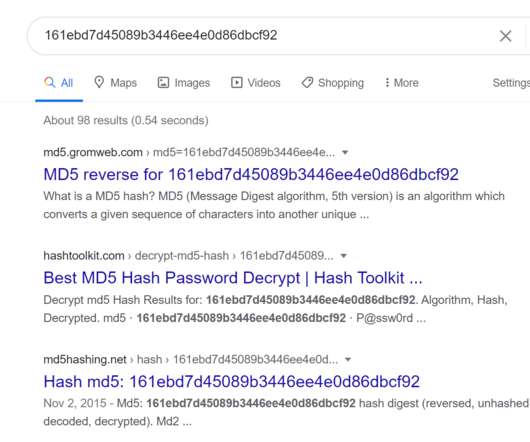
The organisation involved may have contacted you and advised your password was exposed but fortunately, they encrypted it. Isn't the whole point of encryption that it protects data when exposed to unintended parties? This entire blog post hashed with Md5 is still 32 characters long. But you should change it anyway. With bcrypt.

Anton on Security
DECEMBER 20, 2021
Sometimes great old blog posts are hard to find (especially on Medium ) , so I decided to do a periodic list blog with my favorite posts of the past quarter or so. This covers both Anton on Security and my posts from Google Cloud blog , and our Cloud Security Podcast too ( subscribe ). Here is the next one.

Anton on Security
SEPTEMBER 16, 2021
Sometimes great old blog posts are hard to find (especially on Medium ), so I decided to do a periodic list blog with my favorite posts over the past quarter. This covers both Anton on Security and my posts from Google Cloud blog , and now our Cloud Security Podcast too! Here is the next one.

Anton on Security
MARCH 3, 2022
Great old blog posts are sometimes hard to find (especially on Medium) , so I decided to do a periodic list blog with my favorite posts of the past quarter or so. This covers both Anton on Security and my posts from Google Cloud blog , and our Cloud Security Podcast too ( subscribe ). “A Here is the next one.

Graham Cluley
OCTOBER 17, 2024
Read more in my article on the Tripwire State of Security blog. And boy do we need some good news - amid reports that 389 US-based healthcare institutions were hit by ransomware last year - more than one every single day.

Heimadal Security
APRIL 2, 2025
In some cases, that might mean […] The post Top 8 Sophos Intercept X Alternatives for Ransomware Encryption Protection appeared first on Heimdal Security Blog. So, using it often requires a full commitment to the Sophos ecosystem.

Anton on Security
MAY 15, 2023
Great blog posts are sometimes hard to find (especially on Medium ), so I decided to do a periodic list blog with my favorite posts of the past quarter or so. This covers both Anton on Security and my posts from Google Cloud blog , and our Cloud Security Podcast too ( subscribe ). Here is the next one. Is Your Fate In the Cloud?”

Schneier on Security
MAY 23, 2022
This file is encrypted using AES-256-CBC encryption combined with Base64 encoding. A 4-digit application PIN (which gets set during the initial onboarding when a user first instals the application) is the encryption password used to protect or encrypt the licence data. There’s a lot more in the blog post.

Daniel Miessler
DECEMBER 24, 2022
It started back in August of 2022 as a fairly common breach notification on a blog, but it, unfortunately, turned into more of a blog series. After initiating an immediate investigation, we have seen no evidence that this incident involved any access to customer data or encrypted password vaults. Actually, some data was lost.
Centraleyes
APRIL 10, 2025
The most commonly used methods for securing cardholder data are tokenization and encryption. This blog will explore the differences between PCI DSS tokenization vs. encryption, how each method fits into PCI compliance, and the associated PCI DSS encryption requirements and tokenization practices. What Is Encryption?

Adam Shostack
JANUARY 2, 2025
[no description provided] Adrian Colyer has an interesting summary of a recent paper, " Why your encrypted database is not secure " in his excellent "morning paper" blog. Many recent encrypted databases make strong claims of provable security against snapshot attacks. an attacker that does a one-off exfiltration).

Schneier on Security
AUGUST 9, 2021
They were not only able to get into the BitLocker-encrypted computer, but then use the computer to get into the corporate network. Original blog post. It’s the “evil maid attack.” ” It requires physical access to your computer, but you leave it in your hotel room all the time when you go out to dinner.
Anton on Security
AUGUST 9, 2023
Great blog posts are sometimes hard to find (especially on Medium ), so I decided to do a periodic list blog with my favorite posts of the past quarter or so. This covers both Anton on Security and my posts from Google Cloud blog , and our Cloud Security Podcast too ( subscribe ). Here is the next one. Use Cloud Securely? “How

Thales Cloud Protection & Licensing
JANUARY 21, 2025
Three Keys to Modernizing Data Security: DSPM, AI, and Encryption andrew.gertz@t Tue, 01/21/2025 - 14:56 Discover how DSPM, AI, and encryption are transforming data security strategies, reducing vulnerabilities, and improving compliance. A DSPM moves the needle with integrated capabilities and comprehensive encryption.

GlobalSign
FEBRUARY 14, 2024
In this blog, we review why automation and encryption are important in improving time efficiency and mitigating risks in digital certificate management workflows.

Schneier on Security
OCTOBER 27, 2023
found no expired certificates on the server, as explained in a blog post by ValdikSS, a pseudonymous anti-censorship researcher based in Russia who collaborated on the investigation. However, jabber.ru Before it had expired, it would have allowed someone to decrypt the traffic being exchanged over the service.

Krebs on Security
JULY 1, 2020
But absent any additional information from the victim company or their partners who may be affected by the attack, these kinds of stories and blog posts look a great deal like ambulance chasing and sensationalism. Currently, more than a dozen ransomware crime gangs have erected their own blogs to publish sensitive data from victims.

Krebs on Security
NOVEMBER 17, 2022
He’d been on the job less than six months, and because of the way his predecessor architected things, the company’s data backups also were encrypted by Zeppelin. “We’ve found someone who can crack the encryption.” Then came the unlikely call from an FBI agent. “Don’t pay,” the agent said.

Heimadal Security
APRIL 5, 2024
This malicious group successfully encrypted the company’s VMware ESXi servers, which host virtual private servers for their clients, as well as the backups, putting a significant portion of hosted websites […] The post Powerhost’s ESXi Servers Encrypted with New SEXi Ransomware appeared first on Heimdal Security Blog.

Webroot
SEPTEMBER 7, 2023
When it comes to keeping sensitive data safe, email encryption is a necessity. Too many employees and IT experts have experienced the pain of trying to use a needlessly complicated email encryption solution. If this is the experience you’ve come to expect, Webroot Email Encryption powered by Zix is here to surprise you.

Graham Cluley
DECEMBER 7, 2023
Meta's Head of Messenger announced that the company has begun to roll out end-to-end encryption (E2EE) for personal chats and calls. Read more in my article on the Hot for Security blog.
Troy Hunt
MARCH 18, 2024
I linked to the story from the beginning of this blog post and got a handful of willing respondents for whom I sent their data and asked two simple questions: Does this data look accurate? The above example simply didn't have plain text entries for the encrypted data.

Schneier on Security
OCTOBER 15, 2021
The idea is that they wouldn’t touch the cryptography, but instead eavesdrop on communications and systems before encryption or after decryption. Ross Anderson wrote a great blog post on the paper. (It’s Even before Apple made its announcement , law enforcement shifted their battle for backdoors to client-side scanning.

Troy Hunt
NOVEMBER 13, 2024
One last comment: there was a story published earlier this year titled Our Investigation of the Pure Incubation Ventures Leak and in there they refer to "encrypted passwords" being present in the data. Some people take the view of "I have nothing to hide", whilst others become irate if even just their email address is exposed.

Schneier on Security
DECEMBER 21, 2020
Note that the company has heavily edited its blog post, but the original — with lots of technical details — was saved by the Wayback Machine.). So either Cellebrite believes it is so good that it can break whatever Signal does, or the original blog post was a mistake. Cellebrite announced that it can break Signal.

Malwarebytes
FEBRUARY 26, 2025
It wasnt until a few weeks later, when a Google security blog titled 5 new protections on Google Messages to help keep you safe revealed that one of the new protections was designed to introduce Sensitive Content Warnings for Google Messages. I use end-to-end-encrypted (E2EE) messaging for a reason.

Adam Levin
MAY 24, 2019
In a blog post released this week, the company admitted the passwords of “some” of its G Suite customers had been stored on internal servers without cryptographic protection, also known as a hash. We will continue with our security audits to ensure this is an isolated incident,” announced the blog.
Krebs on Security
SEPTEMBER 22, 2023
This is significant because in November 2022, LastPass disclosed a breach in which hackers stole password vaults containing both encrypted and plaintext data for more than 25 million users. The more iterations, the longer it takes an offline attacker to crack your master password. “LastPass in my book is one step above snake-oil. .'”
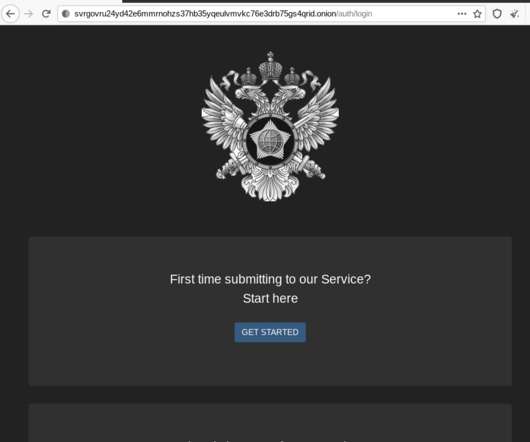
Krebs on Security
JUNE 7, 2021
In the process of doing so, I encountered a small snag: The FSB’s website said in order to communicate with them securely, I needed to download and install an encryption and virtual private networking (VPN) appliance that is flagged by at least 20 antivirus products as malware. Federal Bureau of Investigation (FBI). Image: Wikipedia.
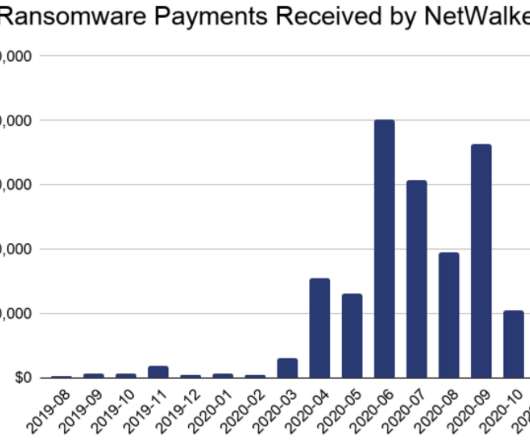
Krebs on Security
JANUARY 27, 2021
“Chainalysis has traced more than $46 million worth of funds in NetWalker ransoms since it first came on the scene in August 2019,” the company said in a blog post detailing its assistance with the investigation. million last summer in exchange for a digital key needed to unlock files encrypted by the ransomware.
Security Affairs
NOVEMBER 26, 2024
A list of these extension IDs is provided at the end of the blog post.” The ZIP file is then XOR encrypted, base64 encoded, and sent via a POST request to a specified URL using the built-in cURL command. Elastic researchers noticed that regarding Safari, only the cookies are collected by the AppleScript script for the current version.
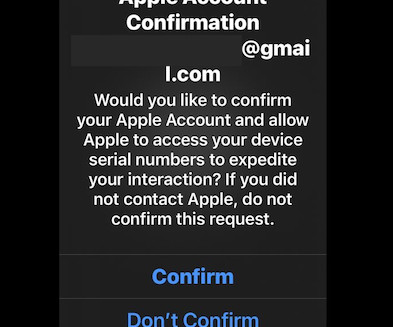
Krebs on Security
JANUARY 7, 2025
The image that Lookout used in its blog post for Crypto Chameleon can be seen in the lower right hooded figure. That latter domain was created and deployed shortly after Lookout published its blog post on Crypto Chameleon. com and two other related control domains — thebackendserver[.]com com and lookoutsucks[.]com. ”

Schneier on Security
MAY 29, 2020
But crucially, Facebook says that the detection will occur only based on metadata -- not analysis of the content of messages -- so that it doesn't undermine the end-to-end encryption that Messenger offers in its Secret Conversations feature. That default Messenger encryption will take years to implement.
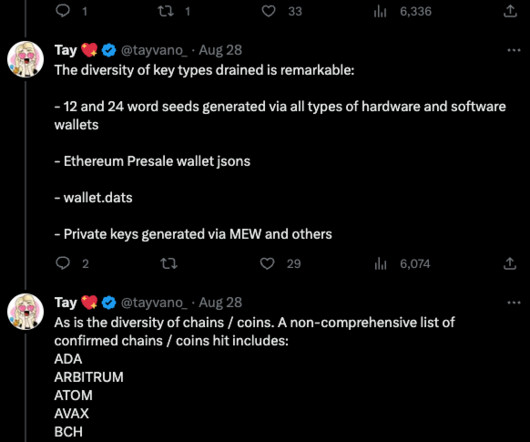
Krebs on Security
SEPTEMBER 5, 2023
In November 2022, the password manager service LastPass disclosed a breach in which hackers stole password vaults containing both encrypted and plaintext data for more than 25 million users. LastPass disclosed that criminal hackers had compromised encrypted copies of some password vaults, as well as other personal information.

Webroot
NOVEMBER 21, 2024
The five core components of a VPN are: Encryption : The conversion of information into a coded format that can only be read by someone who has the decryption key. Split tunneling: Allows you to choose which internet traffic goes through the VPN (with encryption) and which goes directly to the internet. How do VPNs work?

Thales Cloud Protection & Licensing
FEBRUARY 12, 2025
The Rise of Non-Ransomware Attacks on AWS S3 Data madhav Thu, 02/13/2025 - 04:39 A sophisticated ransomware gang, Codefinger, has a cunning new technique for encrypting data stored in AWS S3 buckets without traditional ransomware tools. Many regulations and standards mandate strict control over encryption keys.

Schneier on Security
SEPTEMBER 5, 2019
A decade ago, the Doghouse was a regular feature in both my email newsletter Crypto-Gram and my blog. The discovery challenges today's current encryption framework by enabling the accurate prediction of prime numbers." In it, I would call out particularly egregious -- and amusing -- examples of cryptographic " snake oil.".

Security Boulevard
JANUARY 31, 2025
The cyberthreat landscape of 2024 was rife with increasingly sophisticated threats, and encryption played a pivotal rolea staggering 87.2% billion attempted encrypted attacks, a clear demonstration of the growing risk posed by cybercriminals leveraging encryption to evade detection. of threats were hidden in TLS/SSL traffic.

Fox IT
DECEMBER 10, 2024
One of the most popular requests has been the capability to use Dissect in combination with common disk encryption methods like Microsoft’s BitLocker or its Linux equivalent LUKS. Of course, a blog post is not complete without a demo. Internally at Fox-IT we were able to already use these capabilities.

Krebs on Security
JUNE 16, 2021
First debuting in early 2019, CLOP is one of several ransomware groups that hack into organizations, launch ransomware that encrypts files and servers, and then demand an extortion payment in return for a digital key needed to unlock access. ? /. CLOP’s victim shaming blog on the deep web.
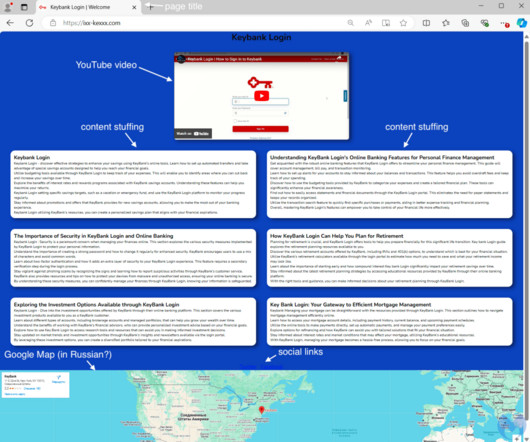
Malwarebytes
NOVEMBER 4, 2024
In this blog post, we take a look at how criminals are abusing Bing and stay under the radar at the same time while also bypassing advanced security features such as two-factor authentication. The idea is about creating content that looks real, like a blog, but with malicious intent (monetization or other). com info-blog-news[.]com
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content