How to Measure Threat Detection Quality for an Organization?
Anton on Security
MARCH 24, 2022
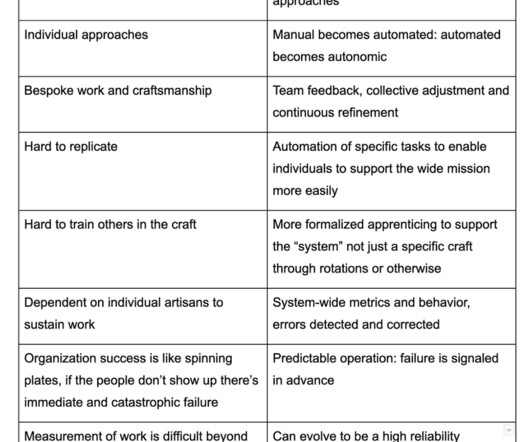
Sometimes I write blog posts with answers. In other cases, I write blog posts with questions. This particular blog post covers a topic where I feel I am in the “discovering questions” phase. Here I’m talking about the quality of the entire detection capability of an organization. In other words, don’t expect answers?—?but




























Let's personalize your content