Most Popular Cybersecurity Blogs from 2023
Lohrman on Security
JANUARY 14, 2024
What were the top government technology and security blogs in 2023? The metrics tell us what cybersecurity and technology infrastructure topics were most popular.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Lohrman on Security
JANUARY 14, 2024
What were the top government technology and security blogs in 2023? The metrics tell us what cybersecurity and technology infrastructure topics were most popular.

Lohrman on Security
JANUARY 15, 2023
What were the top government technology and security blogs in 2022? The metrics don’t lie, and they tell us what cybersecurity and technology infrastructure topics were most popular.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Lohrman on Security
JANUARY 9, 2022
What were the top government security blog posts in 2021? These metrics tell us what cybersecurity and technology infrastructure topics were most popular in the past year.

Schneier on Security
NOVEMBER 14, 2019
Technology is now deeply intertwined with policy. It's all changing fast; technology is literally creating the world we all live in, and policymakers can't keep up. The answer requires a deep understanding of both the policy tools available to modern society and the technologies of AI. Today, it's a crisis.

Security Boulevard
JANUARY 14, 2024
What were the top government technology and security blogs in 2023? The metrics tell us what cybersecurity and technology infrastructure topics were most popular. The post Most Popular Cybersecurity Blogs from 2023 appeared first on Security Boulevard.

The Last Watchdog
NOVEMBER 27, 2023
In cybersecurity, keeping digital threats at bay is a top priority. This technology promises to simplify tasks, boost accuracy and quicken responses. Automation matters in cybersecurity. Implementation steps Amos Incorporating RPA into cybersecurity is crucial, especially with data breaches impacting 281.5

NSTIC
OCTOBER 24, 2023
During this week’s blog series, we sat down with two of our NIST experts from the Visualization and Usability Group at NIST — Shanée Dawkins and Jody Jacobs — who discussed the importance of recognizing and reporting phishing. This week’s Cybersecurity Awareness Month theme is ‘recognize and report phishing.’

NSTIC
OCTOBER 10, 2023
Today’s blog is the second one in our 2023 Cybersecurity Awareness Month series and examines different factors associated with using strong passwords and a password manager. This week’s Cybersecurity Awareness Month theme is ‘ using strong passwords and a password manager.’ One research area is human

Security Boulevard
JANUARY 17, 2023
Many discussions about the human element in cybersecurity center around human fallibility and error. From misconfigurations to selecting weak passwords and getting duped by phishing emails, the mistakes people make play a visible role in cybersecurity incidents. Still, recent technological developments, Read More.

The Last Watchdog
SEPTEMBER 25, 2023
If you’re a small business looking for the secret sauce to cybersecurity, the secret is out: start with a cybersecurity policy and make the commitment to security a business-wide priority. The average cost of a cybersecurity breach was $4.45 The average cost of a cybersecurity breach was $4.45

Heimadal Security
FEBRUARY 1, 2024
We have partnered with Jupiter Technology Corporation, who will distribute our cybersecurity products across Japan as part of a long-term sales and distribution agreement. It […] The post Heimdal Partners with Jupiter Technology to Distribute Cybersecurity Solutions in Japan appeared first on Heimdal Security Blog.

The Last Watchdog
JUNE 13, 2022
At the start of this year, analysts identified a number of trends driving the growth of cybersecurity. billion in venture capital poured into cybersecurity companies globally. For a long time, enterprise customers have been dissatisfied with cybersecurity solutions for identity management. Last year saw an unprecedented $21.8

Security Boulevard
JULY 22, 2024
Emerging at the forefront of technological innovation, Generative AI is reshaping the landscape of cybersecurity defense with groundbreaking advancements. This blog delves into 5 Ways Generative AI is Revolutionizing Cybersecurity Defense and how we protect digital assets.

The Last Watchdog
MARCH 25, 2024
The National Institute of Standards and Technology (NIST) has updated their widely used Cybersecurity Framework (CSF) — a free respected landmark guidance document for reducing cybersecurity risk. It seeks to establish and monitor your company’s cybersecurity risk management strategy, expectations, and policy.

Security Boulevard
JANUARY 9, 2024
Entering a new year, the cybersecurity landscape is poised for significant shifts, driven by the dynamic interplay between technological advancements and persistent threats. The post 2024 Cybersecurity Predictions appeared first on Security Boulevard.
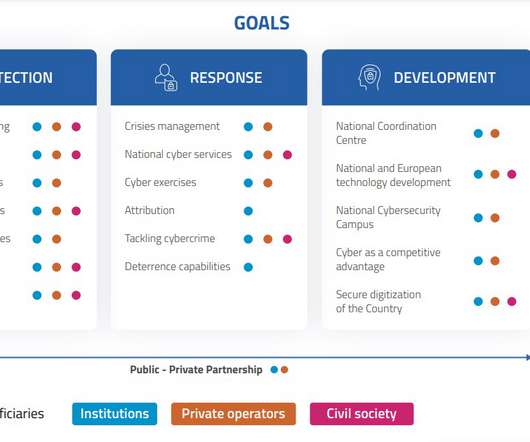
Security Affairs
MAY 26, 2022
Italy announced its National Cybersecurity Strategy for 2022/26, a crucial document to address cyber threats and increase the resilience of the country. The document remarks that cybersecurity is an essential investment and an enabling factor for the development of the national economy and industry. ” reads the strategy.

Security Boulevard
FEBRUARY 22, 2024
Cybersecurity is crucial for national security in the digital world, where major powers clash over their interests. However, technology also enables more sophisticated and harmful network attacks. The post NSFOCUS Innovative DDoS Protection Technology Secures Your Network Perimeter appeared first on Security Boulevard.

Security Boulevard
JANUARY 27, 2023
Artificial intelligence (AI) is rapidly becoming a powerful tool in the cybersecurity landscape, with the potential to revolutionize the way we detect and respond to cyber threats. However, as with any technology, there are also risks associated with the use of AI in cybersecurity.

The Last Watchdog
SEPTEMBER 21, 2022
This explains the rise and popularity of Zero Trust as a framework for securing networks in these new realities as an effective tool to drive cybersecurity initiatives within the entire enterprise. Looking to the future, the adoption of cybersecurity initiatives will remain high and continue to grow.

The Last Watchdog
NOVEMBER 29, 2021
The vulnerabilities and challenges associated with declining worker mental health is causing cybersecurity risks to increase, especially from insider threats. Declining workplace mental health is affecting cybersecurity in various ways. Mental health cyber risks. Steeper leadership challenges.

Security Boulevard
APRIL 29, 2024
The rise of digital technology has provided great convenience to the banking sector, but it has also opened up the doors to cyber attacks. A recent incident at a well-known Indian bank acts as a wake-up call, emphasizing the need for a strong cybersecurity framework.

Security Boulevard
JANUARY 18, 2024
By: Gary Perkins, Chief Information Security Officer As we keep a close eye on trends impacting businesses this year, it is impossible to ignore the impacts of Artificial Intelligence and its evolving relationship with technology. One of the key areas experiencing this transformational change is cybersecurity.

Krebs on Security
APRIL 20, 2021
NYSE:IT ] — a $4 billion technology goliath whose analyst reports can move markets and shape the IT industry. As the largest organization dedicated to the analysis of software, Gartner’s network of analysts are well connected to the technology and software industries. Those enticements have mostly fallen on deaf ears.
Krebs on Security
AUGUST 27, 2024
.” Those third-party reports came in late June 2024 from Michael Horka , senior lead information security engineer at Black Lotus Labs , the security research arm of Lumen Technologies , which operates one of the global Internet’s largest backbones. victims and one non-U.S.

eSecurity Planet
MAY 30, 2023
The software giant built the technology on cutting-edge generative AI – such as large language models (LLMs) – that power applications like ChatGPT. In a blog post , Microsoft boasted that the Security Copilot was the “first security product to enable defenders to move at the speed and scale of AI.” Or consider Palo Alto Networks.

Security Boulevard
JANUARY 2, 2024
One of the big questions that I often get is: How does someone become successful in a cybersecurity career? In this blog I want to share with you the three key lessons I’ve learned during my 18-year journey in the cybersecurity industry.

The Last Watchdog
JANUARY 8, 2023
Business initiatives demand faster, more efficient outcomes and technology responds. The need for reset and oversight is so great that a new class of technology is emerging to give organizations a better grip on the digital sprawl that’s come to define modern-day enterprise architecture.

The Last Watchdog
APRIL 13, 2022
While you might think that these actors are interested in government and defense information, their operations prove they are interested in much more – including software development and information technology, data analytics, and logistics. which supplies ultra-sensitive, portable marijuana breathalyzer technology.

The Last Watchdog
MARCH 27, 2023
Organizations with strong cybersecurity cultures experience fewer cyberattacks and recover faster than others. For most organizations, building a cybersecurity culture is a necessary evil rather than a cherished goal. For most organizations, building a cybersecurity culture is a necessary evil rather than a cherished goal.

Jane Frankland
MAY 8, 2024
On one hand, AI has been hailed as a game-changing technology with the potential to transform industries and improve our daily lives. So where does AI stand in the realm of cybersecurity, and how can we leverage it for protection rather than harm? This is where AI comes in as a potential game-changer.

Quick Heal Antivirus
JULY 30, 2024
Tap and pay technology has completely changed the way we do transactions. Discover the Hidden Dangers of Tap and Pay Technology appeared first on Quick Heal Blog. Imagine making a payment just by. The post Is Your Money Safe?

The Last Watchdog
OCTOBER 16, 2023
In response, industry professionals must automate their cybersecurity tools to stay ahead. The 2020 SolarWinds cybersecurity incident — which industry experts call the supply chain attack of the decade — was an incredibly high-profile breach affecting massive corporations. Simply put, cyberattacks are on the rise. Ongoing monitoring.

The Last Watchdog
MAY 20, 2022
The unification revolution of cybersecurity solutions has started – and managed security service providers are leading the way. Managed security services (MSS) refer to a service model that enable the monitoring and managing of security technologies, systems, or even software-as-a-service (SaaS) products. Fully-managed vs. co-managed.

Krebs on Security
APRIL 18, 2022
Cybersecurity & Infrastructure Security Agency (CISA), Zloader had a special relationship with Ryuk/Conti, acting as a preferred distribution platform for deploying Ryuk/Conti ransomware. Conti shames victims who refuse to pay a ransom by posting their internal data on their darkweb blog.

The Last Watchdog
JUNE 26, 2023
As the threat of cybercrime grows with each passing year, cybersecurity must begin utilizing artificial intelligence tools to better combat digital threats. However, the truth is that automated AI tools work best in the hands of cybersecurity professionals instead of replacing them.

Cisco Security
NOVEMBER 14, 2022
In the second part of this blog series on Unscrambling Cybersecurity Acronyms , we covered Endpoint Detection and Response (EDR) and Managed Endpoint Detection and Response (MEDR) solutions, which included an overview of the evolution of endpoint security solutions. What are Managed Detection and Response (MDR) solutions? .

The Last Watchdog
JANUARY 9, 2024
Augmented reality (AR) and virtual reality (VR) technologies provide intriguing opportunities for immersive and interactive experiences in cybersecurity training. AR and VR technologies can create distinct immersive experiences by merging digital reality with the physical world.

The Last Watchdog
OCTOBER 24, 2022
In addition, educating employees about cybersecurity issues can help to reinforce the security-minded culture of the organization and change employee behaviour. Training employees is a crucial part of fighting back against this kind of attack and can complement other technological security solutions. Change passwords regularly.

Thales Cloud Protection & Licensing
OCTOBER 2, 2023
Cybersecurity Awareness Month 2023 – What it is and why we should be aware madhav Tue, 10/03/2023 - 05:33 The inception of Cybersecurity Awareness Month in 2004 came at a critical juncture in our technological history. This dynamic environment has necessitated a consistent evolution in our cybersecurity strategies.

Security Boulevard
SEPTEMBER 23, 2024
Cunningham, Chief Technology Officer Michael Wilson, and Product Manager Marcy Elder—gathered for a webinar to share their insights on what’s next for cybersecurity management. Reimagining Cybersecurity Management Five years ago, when Lewie joined.

The Last Watchdog
MARCH 29, 2021
One of the hottest fields right now on the WFH radar is the information technology (IT) sector. Many universities offer massive open online courses (MOOC) in cybersecurity. While you’ll need a bachelor’s degree (not necessarily in cybersecurity specifically) for most of these jobs, the median pay is a very solid $47.95/hr.

The Last Watchdog
NOVEMBER 8, 2021
However, M&A is a complex undertaking, and integrating and consolidating IT, cybersecurity and data privacy infrastructure only adds to the challenge. M&A invariably creates technology gaps that bad actor’s prey upon. Patient data exposures. Healthcare data security and privacy is a problem that continues to grow.

Krebs on Security
NOVEMBER 17, 2022
Peter is an IT manager for a technology manufacturer that got hit with a Russian ransomware strain called “ Zeppelin ” in May 2020. “These senseless acts of targeting those who are unable to respond are the motivation for this research, analysis, tools, and blog post. .

Krebs on Security
DECEMBER 14, 2020
” In response to the intrusions at Treasury and Commerce, the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA) took the unusual step of issuing an emergency directive ordering all federal agencies to immediately disconnect the affected Orion products from their networks. ”
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content