Google introduces Context-Aware Cyber Threat detection to Chronicle
CyberSecurity Insiders
MARCH 16, 2022
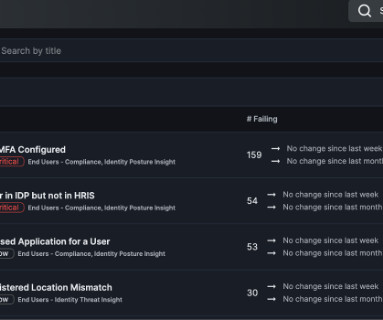
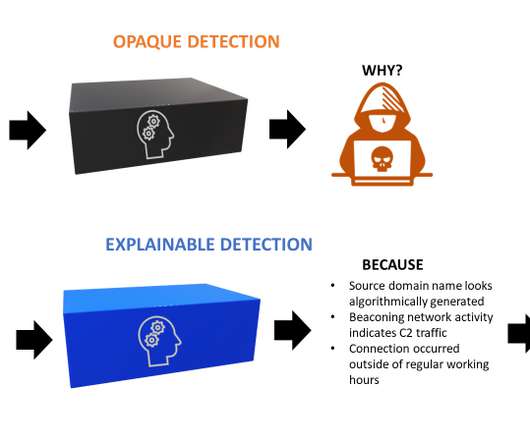
Google Cloud might think of delivering end-to-end security to its enterprise customers and so introduced Context-aware threat detection to its Chronicle platform. With the latest announcement Google is acknowledging all its IT Stack-related customer needs at one go”, says Chronicle in its latest blog post.














































Let's personalize your content