3 tips to reducing big data compliance risks
Tech Republic Security
NOVEMBER 16, 2016
Don't let big data compliance risks take you by surprise. Here are three steps to take today to ease your big data compliance concerns.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Tech Republic Security
NOVEMBER 16, 2016
Don't let big data compliance risks take you by surprise. Here are three steps to take today to ease your big data compliance concerns.

Tech Republic Security
OCTOBER 25, 2016
The security risks associated with IoT devices cannot be ignored. If your big data plans include IoT devices, follow these four steps to reduce your chances of a security breach.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

SecureBlitz
SEPTEMBER 20, 2023
In this post, I will show you the big risks in Big Data for Fintech companies. These innovative companies have moved the once legacy world of banking into new […] The post The Big Risks In Big Data For Fintech Companies appeared first on SecureBlitz Cybersecurity.

Thales Cloud Protection & Licensing
FEBRUARY 8, 2018
The 2018 Thales Data Threat Report (DTR) has great information on Big Data use and security. We surveyed more than 1,200 senior security executives from around the world, and virtually all (99%) report they plan to use Big Data this year. Top Big Data Security Concerns. Big Data is unstructured.

Tech Republic Security
JUNE 6, 2024
Both the promise and the risk of "human-level" AI has always been part of OpenAI’s makeup. What should business leaders take away from this letter?

The Last Watchdog
OCTOBER 16, 2019
Related: Cyber risks spinning out of IoT Credential stuffing and account takeovers – which take full advantage of Big Data, high-velocity software, and automation – inundated the internet in massive surges in 2018 and the first half of 2019, according to multiple reports.

Tech Republic Security
JANUARY 11, 2017
Developers just want to 'get stuff done,' but may be putting their enterprise data at risk in the process. Here's why.

SC Magazine
APRIL 19, 2021
Among the incidents data stolen by Chinese hackers involved a Twitter database. Researchers on Monday reported that cybercriminals are taking advantage of China’s push to become a leader in big data by extracting legitimate big data sources and selling the stolen data on the Chinese-language dark web.

Tech Republic Security
MAY 15, 2023
The post Survey: Most CISOs feel their business is at risk for cyberattack appeared first on TechRepublic. A new report from Proofpoint provides global insight into CISOs' challenges, expectations and priorities for 2023.

Thales Cloud Protection & Licensing
NOVEMBER 19, 2018
The age of Big Data is upon us. And, as more data is available for analytical purposes, more sensitive and private information is at risk. Protecting the confidentiality and integrity and of warehoused data and ensuring that access is controlled is vital to keeping that data secure. respondents.”.

Tech Republic Security
SEPTEMBER 23, 2022
Now you can see your institution's fraud and security risks in a new way, with LogicGate Risk Cloud. The post LogicGate Risk Cloud: Product review appeared first on TechRepublic. Read our review here.

Tech Republic Security
MAY 24, 2024
A leading cyber lawyer in Australia has warned CISOs and other IT leaders their organisations and careers could be at stake if they do not understand data risk and data governance practices.

IT Security Guru
NOVEMBER 16, 2023
Through AI-enabled systems, different industries have been able to minimize human error and automate repetitive processes and tasks while smoothly handling big data. Despite AI’s countless benefits, it also comes with some risks that each user should be aware of.

TrustArc
MARCH 29, 2022
For example, the global big data analytics market is predicted […]. It seems every department, function, and team in an organization uses their preferred list of external apps and vendors to satisfy their business needs.

SecureBlitz
JULY 23, 2023
Big data analytics and the increasing usage of VDRs have changed investment banking. Access to enormous volumes of data that can be evaluated is made possible by VDRs. The way investment banks and other financial organizations conduct business is changing due to these innovations.
Security Affairs
FEBRUARY 11, 2025
Artificial intelligence enhances data security by identifying risks and protecting sensitive cloud data, helping organizations stay ahead of evolving threats. Artificial intelligence (AI) is transforming industries and redefining how organizations protect their data in todays fast-paced digital world.
eSecurity Planet
MAY 18, 2022
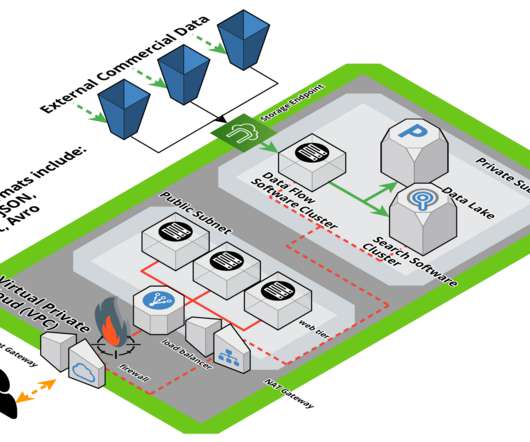
Actually, pretty much all software uses this library written in Java, so it’s a very widespread risk and concern. Zectonal researchers have revealed a new and critically important attack vector that can use the infamous bug: Data pipelines and data lakes. Understanding the Big Data Attack.
Penetration Testing
MAY 9, 2024
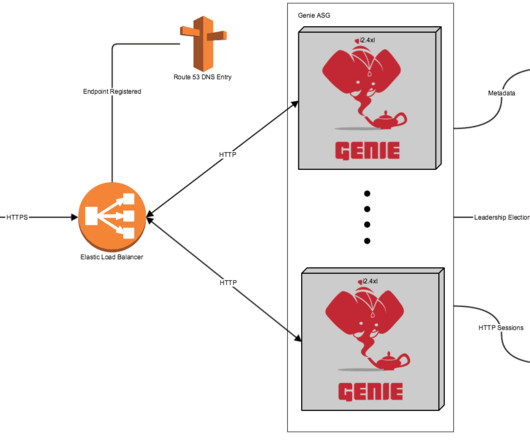
A severe remote code execution (RCE) vulnerability has been discovered in Genie, Netflix’s popular open-source job orchestration engine for big data processing. ... The post CVE-2024-4701 (CVSS 9.9): Major RCE Risk in Netflix’s Genie Platform appeared first on Penetration Testing.

The Last Watchdog
AUGUST 23, 2021
International workforces can be an excellent way to find top talent, but they can introduce unique security risks. Inconsistent data regulations. Countries have different data security laws, and these can get in the way of one another. Surveillance gives cybercriminals another potential point of entry to see or steal your data.

Security Affairs
APRIL 4, 2025
This impacts big-data frameworks (e.g., Disrupt services: They could shut down services or corrupt data, causing denial of service and business downtime. “All confidentiality, integrity, and availability of the affected system are at risk (in CVSS terms, High impact on all three). Versions 1.15.0

SecureWorld News
OCTOBER 20, 2021
Cyberrisk is business risk. But how should we communicate this risk to the business, to clients, or to investors? Accenture annual report: risks we face from cyberattacks. Accenture featured this earning's news on page 2 in a big, bold font. L egal, reputational and financial risks? billion, a 14% increase in U.S.

Security Boulevard
APRIL 18, 2022
This big data discipline of artificial intelligence gives systems the freedom to automatically gain information. The post What is Machine Learning? appeared first on Gurucul. The post What is Machine Learning? appeared first on Security Boulevard.

Krebs on Security
SEPTEMBER 17, 2020
“CHENGDU 404 developed a ‘big data’ product named ‘ SonarX ,’ which was described…as an ‘Information Risk Assessment System,'” the government’s indictment reads. Security analysts and U.S. Chengdu404’s offices in China. Image: DOJ.

The Last Watchdog
NOVEMBER 30, 2021
Yet, API security risks haven’t gotten the attention they deserve. Cybersecurity vendors competing in this nascent space, Salt Security among them, are ramping up their efforts to leverage Big Data and advanced analytics to meet a highly dynamic and complex security threat.
Tech Republic Security
SEPTEMBER 21, 2023
Australian retailers are rolling out mass surveillance solutions to combat shoplifting, but a poor regulatory environment could mean high risks associated with data security and privacy.

Privacy and Cybersecurity Law
MARCH 21, 2013
What is Big Data? Big Data is about using mathematical models to spot patterns or “footprints” in large datasets. The […].

Tech Republic Security
FEBRUARY 26, 2025
Ransomware groups now steal, encrypt, and threaten to leak company data on the dark web, forcing victims to pay or risk exposing sensitive information.

Security Boulevard
APRIL 21, 2021
Cybercriminals are using big data technology to make money from data obtained on the Chinese-language underground. Quelle surprise.

Tech Republic Security
JUNE 5, 2024
Find out how the cyberespionage threat actor LilacSquid operates, and then learn how to protect your business from this security risk.

The Last Watchdog
OCTOBER 17, 2023
Combining a security Information tool with a security event tool made it easier to correlate alerts generated by security products, like firewalls and IDS, normalize it, and then analyze it to identify potential risks. We use machine learning models on open choice big data lakes to detect unknown threats early in the attack chain.

Tech Republic Security
SEPTEMBER 1, 2023
The National Cyber Security Centre provides details on prompt injection and data poisoning attacks so organizations using machine-learning models can mitigate the risks.
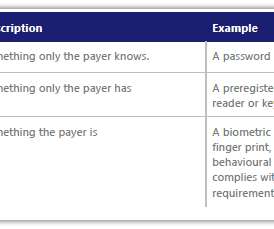
Thales Cloud Protection & Licensing
JANUARY 26, 2021
Coupled with the fact that only about half of all vulnerabilities in the retail industry are getting patched within the first quarter after discovery, it is easy to understand the risks of being defraud by criminals. Big Data and EMV 3DS. Fraud detection is where big data and machine learning come in handy.

Spinone
JUNE 8, 2018
While the potential of Big Data is vast, it might lag behind as a standalone tool to deal with hackers due to the enormous volume of data to analyze. There is a huge difference between raw data collected and meaningful insights that can benefit enterprises in their attempt to prevent cyber attacks.

Tech Republic Security
JUNE 6, 2023
Read the technical details about this zero-day MoveIT vulnerability, find out who is at risk, and learn how to detect and protect against this SQL injection attack. The post Zero-day MOVEit Transfer vulnerability exploited in the wild, heavily targeting North America appeared first on TechRepublic.

SC Magazine
MARCH 29, 2021
ARCSIGHT Company: Micro Focus Noteworthy: Correlation engine delivers real-time detection of both known and unknown, elusive threats, through machine learning-based behavioral analysis and big data threat hunting. FINALIST | BEST SIEM SOLUTION. FINALIST | BEST SIEM SOLUTION.

Thales Cloud Protection & Licensing
DECEMBER 5, 2018
With digital transformation technologies like cloud, big data, IoT, containers, mobile payments and blockchain all in play, there are many new attack surfaces and risks to financial data. Each and every environment and instance requires a data security plan and implementation tuned to the environment.

Security Affairs
DECEMBER 1, 2020
In January, the EU’s executive Commission presented a set of rules and technical measures aimed at reducing cybersecurity risks from the adoption of 5G. The Commission’s recommendations included blocking high-risk equipment suppliers from “critical and sensitive” components of 5G infrastructures, such as the core. allegations.

The Last Watchdog
MAY 20, 2022
Keeping up with new risks, resolving them as soon as they occur, and recovering from incidents identified too late may, as you can certainly imagine, take up valuable resources and cause businesses to lose time, money, and the trust of their clients/partners. The greater the reliance, the more likely such a breach will take place.

The Last Watchdog
SEPTEMBER 27, 2021
Assessing the risks involved in using the latest technology is something our culture had to adopt in the early days of the computer. New technologies come with risks — there’s no denying that. Businesses and consumers have to assess cybersecurity risks to protect their assets and private information.

Thales Cloud Protection & Licensing
SEPTEMBER 5, 2019
The vast majority (84%) of enterprises are now using, or planning to use, digitally transformative technologies – such as big data, containers, blockchain and the Internet of Things (IoT). The picture looks rather different, when we look at evolving threats in the context of big data. Blockchain.

Security Affairs
JANUARY 17, 2022
Oracle also urges its customers to apply Critical Patch Update patches as soon as possible due to the risk of exploitation of the addressed vulnerabilities. Some of the vulnerabilities addressed in this Critical Patch Update impacts multiple products. The highest CVSS v3.1 Base Score (10.0) The highest CVSS v3.1 Base Score (10.0)

Thales Cloud Protection & Licensing
JULY 25, 2019
healthcare organizations are nearly universal in the adoption of digital transformation technologies (cloud, SaaS applications, big data, IoT, digital payments, containers, and blockchain). ET about “The State of Data Security in Healthcare.” Thales will also host a webinar on Thursday, Sept. 12 at 2:00 p.m.

Thales Cloud Protection & Licensing
OCTOBER 4, 2021
The digital transformation initiatives have shifted the technology landscape and introduced new threats and risks. To address the escalating cyber risks, the Hong Kong Association of Banks (HKAB) developed and published guidelines for Secure Tertiary Data Backup (STDB).

Tech Republic Security
JULY 24, 2023
Assurances include watermarking, reporting about capabilities and risks, investing in safeguards to prevent bias and more.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content