7 Types of Penetration Testing: Guide to Pentest Methods & Types
eSecurity Planet
JUNE 28, 2023
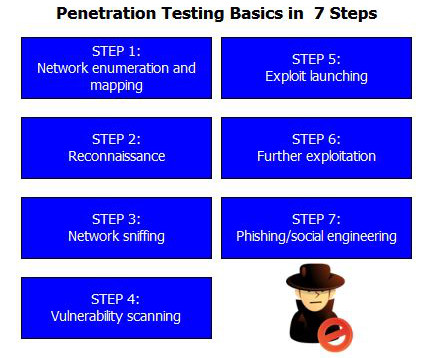
Social engineering tests Social engineering is a technique used by cyber criminals to trick users into giving away credentials or sensitive information. Attackers usually contact workers, targeting those with administrative or high-level access via email, calls, social media, and other approaches.

















Let's personalize your content