9 Best Penetration Testing Tools for 2022
eSecurity Planet
FEBRUARY 24, 2022
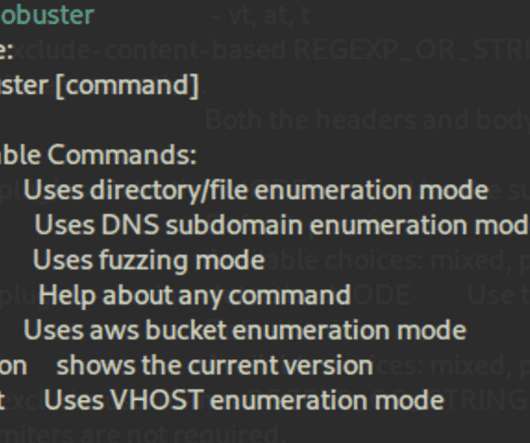
Installing Kali can remove the hassle of downloading and installing these tools separately. Can spot backup and configuration files. Download Gobuster. Download and install Amass. System administrators and security teams (and hackers) can use them to spot weak passwords. Can hide status and process (e.g.,












Let's personalize your content