Chinese national charged for hacking thousands of Sophos firewalls
Security Affairs
DECEMBER 11, 2024
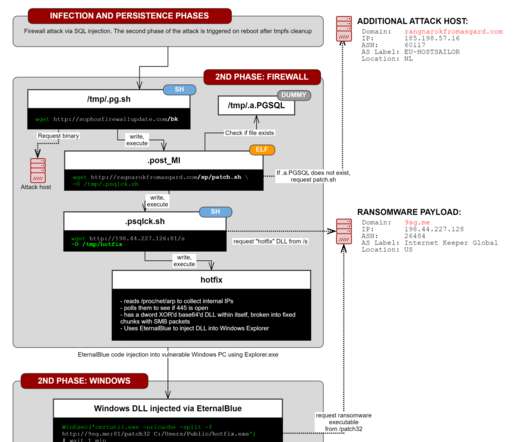
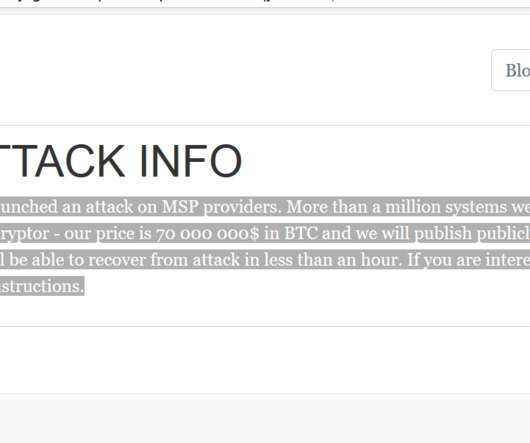
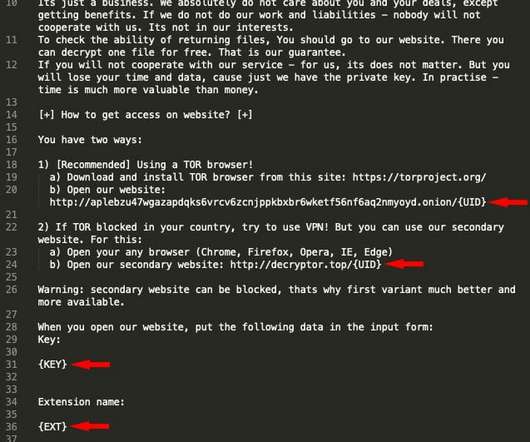
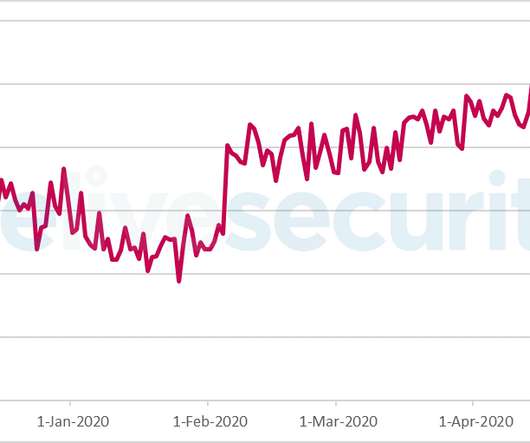
has charged a Chinese national for hacking thousands of Sophos firewall devices worldwide in 2020. has charged the Chinese national Guan Tianfeng (aka gbigmao and gxiaomao) for hacking thousands of Sophos firewall devices worldwide in 2020. It was designed to download payloads intended to exfiltrate XG Firewall-resident data.














































Let's personalize your content