Security Affairs newsletter Round 493 by Pierluigi Paganini – INTERNATIONAL EDITION
Security Affairs
OCTOBER 13, 2024
Enjoy a new round of the weekly SecurityAffairs newsletter, including the international press.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Security Affairs
OCTOBER 13, 2024
Enjoy a new round of the weekly SecurityAffairs newsletter, including the international press.

SecureWorld News
OCTOBER 31, 2024
The crucifix : Regular backups, robust firewalls, and anti-malware software can drive away these bloodsuckers, keeping your system safe from sudden data "drain." Spooky fact : Sophos says the average ransom in 2024 is $2.73 Spooky fact : The average cost of a ransomware attack in 2023 is estimated to be $4.5
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Affairs
FEBRUARY 15, 2025
CISA adds Apple iOS and iPadOS and Mitel SIP Phones flaws to its Known Exploited Vulnerabilities catalog Attackers exploit recently disclosed Palo Alto Networks PAN-OS firewalls bug U.S. custody in exchange for Marc Fogel North Korea-linked APT Emerald Sleet is using a new tactic U.S.

Security Affairs
FEBRUARY 11, 2025
The Talos researchers discovered a number of features implemented by Phobos allowing operators to establish persistence in a targeted system, perform speedy encryption, and remove backups. Disable system recovery, backup and shadow copies and the Windows firewall. Embedded configuration with more than 70 options available.

CyberSecurity Insiders
MARCH 21, 2021
Therefore, make sure to set up the latest network routers and firewall protocols across all IT equipment to strengthen your security and create a defense against hackers and security breaches. Firewalls . Install hardware firewalls for the maximum level of network security. . Backup data on Cloud . Monitoring system.
Security Affairs
MARCH 13, 2025
The threat actors use PsExec to execute scripts, enable RDP access, and modify firewall rules. Encryption is executed using gaze.exe , which disables security tools, deletes backups, and encrypts files with AES-256 before dropping a ransom note. Attackers use Mimikatz to steal credentials.

Security Affairs
FEBRUARY 13, 2024
Stopping it will remove the evidence stored in the volatile memory (RAM) Collect and keep all relevant log information, from the affected equipment, but also from network equipment, firewall Examine the system logs to identify the mechanism by which IT infrastructure has been compromised Immediately inform all employees and notify affected customers (..)

Security Affairs
JUNE 17, 2023
Margaret’s Health is the first hospital to cite a cyberattack as a reason for its closure A database containing data of +8.9 Margaret’s Health is the first hospital to cite a cyberattack as a reason for its closure A database containing data of +8.9

Security Affairs
JUNE 7, 2022
The attackers, prior to the deployment of the ransomware, established RDP sessions to Hyper-V servers to modify configurations for the Veeam backup jobs and deleted the backups of the virtual machines used by the victims.

eSecurity Planet
APRIL 24, 2023
Cybercrime has skyrocketed in the last few years, and the websites of small and medium-sized companies have been the most frequent target of web attacks. See the Top Web Application Firewalls (WAFs) What is SPanel? Offsite backups SPanel accounts also get free daily backups to a remote server.
Security Affairs
JULY 5, 2021
Implement allowlisting to limit communication with remote monitoring and management (RMM) capabilities to known IP address pairs, and/or Place administrative interfaces of RMM behind a virtual private network (VPN) or a firewall on a dedicated administrative network.
Security Affairs
NOVEMBER 19, 2023
The Talos researchers discovered a number of features implemented by Phobos allowing operators to establish persistence in a targeted system, perform speedy encryption, and remove backups. Disable system recovery, backup and shadow copies and the Windows firewall. Embedded configuration with more than 70 options available.

CyberSecurity Insiders
NOVEMBER 25, 2021
Today, any company can fall victim to cybercrime, which has become a major problem around the world. Install firewalls and anti-virus software on each computer within your company to combat cyber attacks and make sure you regularly update it. If your system is hacked, you can use backups to restore your data.

Security Affairs
SEPTEMBER 8, 2024
Head Mare hacktivist group targets Russia and Belarus Zyxel fixed critical OS command injection flaw in multiple routers VMware fixed a code execution flaw in Fusion hypervisor U.S.

SiteLock
AUGUST 27, 2021
Because cybercrime is big business (and the fastest-growing type of crime), new attack methods are always arising. Block cybercriminals and bad bots with a web application firewall. Prepare for disaster recovery with Website Backup. Additionally, cybercriminals aren’t the only reason you need regular site backups.

SiteLock
AUGUST 27, 2021
In fact, the World Economic Forum (WEF) projects that by 2021: Global cybercrime costs could total approximately $6 trillion in the US. If cybercrime were a country, it would have the third largest economy in the world. Clearly, cybercrime is big business, and it operates like one. How big is the impact of cybercrime?

The Last Watchdog
APRIL 28, 2020
That, of course, presents the perfect environment for cybercrime that pivots off social engineering. What people will eventually come to realize, the sooner the better, is that we will need to flatten the X factor represented by cybercrime. Backup your data frequently on hard drives that aren’t connected 24/7 to the internet.

CyberSecurity Insiders
JUNE 13, 2023
Be Skeptical of Phishing Attempts: Phishing is a prevalent cybercrime technique that involves tricking individuals into divulging their sensitive information. Maintain Regular Backups: Regularly back up your important data to an external hard drive or a cloud-based service.
Security Affairs
JANUARY 28, 2023
The recent Hive infrastructure takedown as well as other major gangs dissolution such as Conti in 2022, is making room in the cybercrime business The Lockbit locker leaked a few months ago in the underground, is increasing its popularity and adoption among micro-criminal actors.

SiteLock
AUGUST 27, 2021
This is especially true today considering the fact that cybercrime continues to be a serious threat for businesses and users. When cybercrime happens to your company website, you can lose money, credibility, and customers. Set Your Site Up for Success with a Web Application Firewall (WAF). Backup Your Site Regularly.

CyberSecurity Insiders
MAY 18, 2022
These developments have made the perimeter so porous that the old approach of simply hiding behind a firewall and keeping the rest of the world at bay is no longer feasible. In fact, the NSA and CISA have released a joint statement on the value of protective DNS solutions in fighting modern cybercrime. So where do we go from here?

Security Affairs
OCTOBER 22, 2022
US government agencies warned that the Daixin Team cybercrime group is actively targeting the U.S. CISA, the FBI, and the Department of Health and Human Services (HHS) warned that the Daixin Team cybercrime group is actively targeting U.S. Healthcare and Public Health sector with ransomware.

SiteLock
AUGUST 27, 2021
As cybercrime increases, your security measures should, too. As cybercrime advances and backdoor attacks become even more prevalent, it’s vital that small businesses pay close attention to their cybersecurity efforts. Keep an off-site backup of the site that’s confirmed to be free of back doors. million versus $4.25

eSecurity Planet
OCTOBER 15, 2024
Even the smallest business can become a target for cybercrime, with cyber threats increasingly affecting organizations of all sizes. Data breaches, ransomware attacks, and other forms of cybercrime bring direct costs in the form of data recovery, legal fees, and potential fines for failing to comply with regulatory standards.

SecureWorld News
SEPTEMBER 14, 2021
This is also true for victims of cybercrimes, too. I figured they [the school district] had firewalls and things of that nature. They followed the FBI’s advice to not pay the hackers and restored their system from backups they had kept for such an emergency. Unfortunately, there is no perfect profile for a cybercriminal.

Digital Shadows
OCTOBER 23, 2024
This concealed their attack until the environment was encrypted and backups were sabotaged. In this report, we explore Scattered Spider’s evolution from low-level cybercrimes to partnering with ransomware groups to target major organizations. Our investigation uncovered an NTDS.dit file on the attacker’s VM.

Responsible Cyber
APRIL 8, 2020
As cybercrime has become well-funded and increasingly sophisticated, phishing remains one of the most effective methods used by criminals to introduce malware into businesses. Businesses must also ensure they have secure backups of their critical data. Phishing and Spear Phishing. Lack of Cybersecurity Knowledge. SQL Injection.

eSecurity Planet
SEPTEMBER 22, 2021
Then you want to add extra protection around your most critical data, in the form of zero trust access tools and high-integrity data backups. And enterprise firewall vendors Fortinet and Palo Alto Networks unveiled secure routers last week aimed at home and small office workers. Sociopolitical Motivations.

eSecurity Planet
FEBRUARY 16, 2021
With vulnerabilities rooted in unsuspecting users, the task of preventing these attacks means both staff training and a robust email and network security system that includes a strong backup program so you have a recent copy of your data that you can roll back to. Offline Backups. Screenshot example. Version restores.

SC Magazine
MARCH 19, 2021
losses from cybercrime topped $4.1 Backup and recovery should also be important components of an organization’s data protection planning. Does the company have a set of internal firewalls protecting its databases? FBI Director Christopher Wray speaks to a group in Washington, D.C. The FBI recently reported that total U.S.
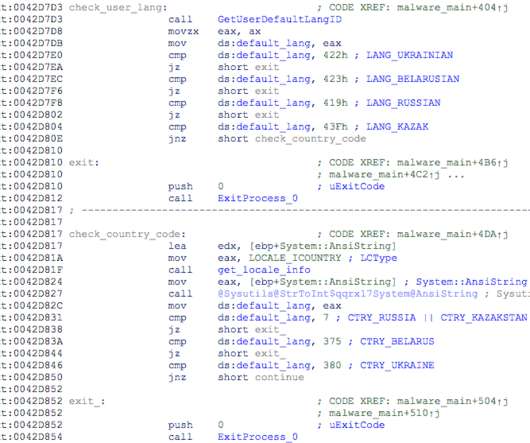
Security Affairs
AUGUST 13, 2022
The group uses multiple attack vectors to gain access to victim networks, including RDP exploitation, SonicWall firewall vulnerabilities exploitation, and phishing attacks. Zeppelin actors request ransom payments in Bitcoin, they range from several thousand dollars to over a million dollars.

SecureWorld News
JULY 7, 2022
While large and active Ransomware-as-a-Service (RaaS) gangs like Conti, LockBit, and BlackCat always make headlines with their operations, it's important to learn about smaller ransomware families, as they can provide insight and help us understand more about cybercrime gangs as a whole. What is North Korea up to?

CyberSecurity Insiders
FEBRUARY 2, 2022
Cybercrime costs approximately $600 billion per year, accounting for over 1% of global GDP, as per The Center for Strategic and International Studies (CSIS), and 300,562,519 people were affected by publicly disclosed security breaches the previous year, as per the Identity Theft Resource Center. Operational users. Software, Hardware, Network.
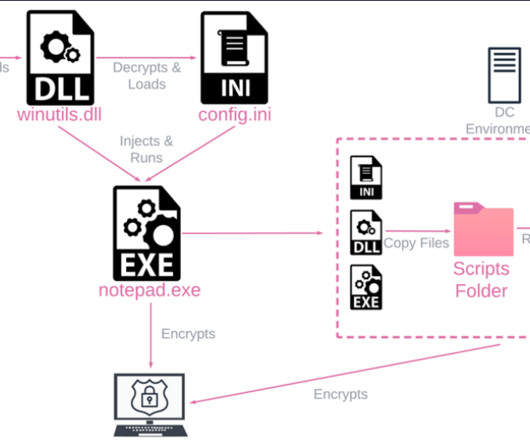
Security Affairs
APRIL 4, 2023
The ransomware uses this technique to stop a predefined list of services, delete shadow volumes and backups, clear the following Windows event logs, and disable the Windows firewall.
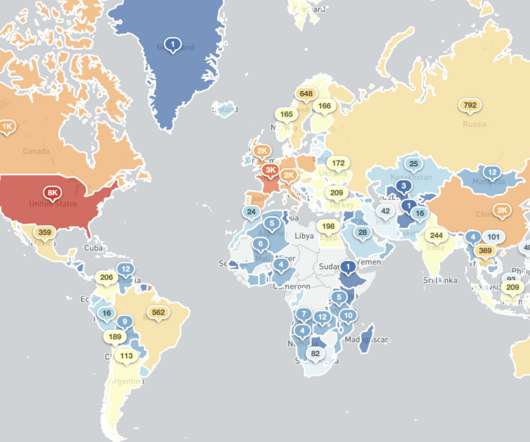
Security Affairs
JUNE 23, 2020
Fxmsp took his first steps in the cybercrime scene in September 2016 when he registered on an underground forum, fuckav[.]ru. After gaining access to the target device, Fxmsp usually disables the existing antivirus software and firewall, then creates additional accounts. Finally, he infects the backups by installing backdoors.

IT Security Guru
JULY 28, 2023
On the other hand, small-sized companies are also vulnerable to increasing cybercrime and the rapidly evolving threat landscape since they need more resources to hire security professionals and need more expertise.

SecureWorld News
OCTOBER 8, 2023
Use the 3-2-1 backup rule. Fully utilize firewall capabilities. Enhancing your security habits The culture of safe device use should be improved. This involves several steps, including: Regularly back up your data, saving it to external drives or cloud services to protect against data loss.

Spinone
OCTOBER 13, 2020
As is often the case, the cost of restoring files from backups can amount to more than paying the ransom. It has been noted that paying a ransom demand only encourages this type of cybercrime and funds it. Backups aren’t working. Ransomware today can actually look for backup files along with user data.

Vipre
JANUARY 25, 2021
Backup and Recovery Tools. In this day and age of digital communication where the most common method of recording and storing information is digital, backup and recovery tools are indispensable if you want to protect your digital data. Data loss due to system crashes or hardware failures is as frustrating as it is common. Ad Blockers.

eSecurity Planet
SEPTEMBER 13, 2024
Cyber security measures ensure this data is safeguarded against breaches, fraud, hacking, and other forms of cybercrime. Encryption, firewalls, and secure access controls are just a few of the measures that banks implement to ensure customer data remains protected.
Digital Shadows
NOVEMBER 26, 2024
The proliferation of cybercrime guides on forums and a 7% rise in insider threat content, driven by significant financial incentives, highlight the growing complexity of cybersecurity challenges. The proliferation of these guides enables more individuals to enter the cybercrime arena.

Security Affairs
JUNE 14, 2023
Certain web application firewalls (WAF) will purportedly provide adequate protections against exploitation but an upgrade from Elementor is suggested immediately if version 3.11.6 wc-ajax=1”. After updating values such as “siteurl,” SQL queries can be generated to determine the destination specified and whether autoload is enabled.

Spinone
JANUARY 9, 2019
Phishing scams are cybercrimes that target unsuspecting end users by electronic communication that fraudulently presents itself as a known, reputable company and persuades individuals to divulge sensitive information including credit card numbers, social security numbers, and other sensitive personal information. What are Phishing Scams?

Digital Shadows
OCTOBER 23, 2024
This concealed their attack until the environment was encrypted and backups were sabotaged. In this report, we explore Scattered Spider’s evolution from low-level cybercrimes to partnering with ransomware groups to target major organizations. Our investigation uncovered an NTDS.dit file on the attacker’s VM.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content