Ransomware Prevention, Detection, and Simulation
NetSpi Executives
APRIL 27, 2024
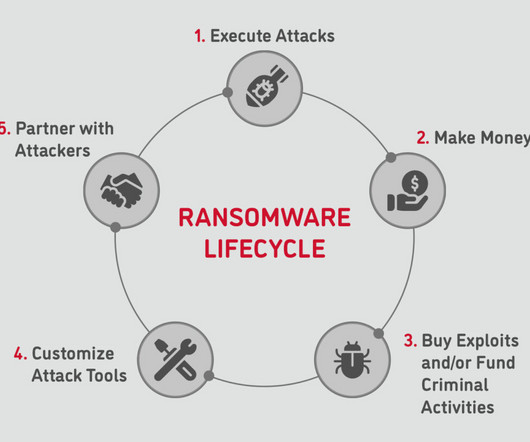
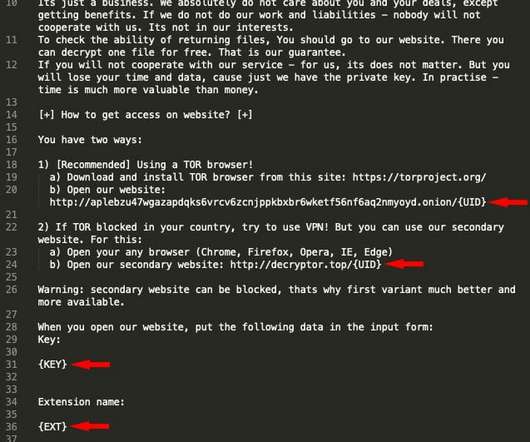
An attacker can easily scan the internet for websites that haven’t patched a vulnerability for which the attacker has an exploit. In addition to encrypting data and holding it hostage, ransomware attackers also upload valuable data to other systems on the internet. Some can’t afford not to pay, and some are covered by cyber insurance.








Let's personalize your content