Verizon's 2025 DBIR: Threats Are Faster, Smarter, and More Personal
SecureWorld News
APRIL 23, 2025
Ransoms are usually paid via cryptocurrency, and those values have been back on the rise since Q4 2023rising aggressively in the past couple of quarters. The only method of recovery will be backups, however data shows that backups do not typically survive these breaches.





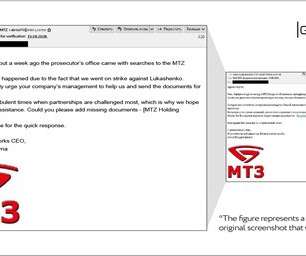










Let's personalize your content