Social Engineering and Healthcare
Security Through Education
JANUARY 4, 2023
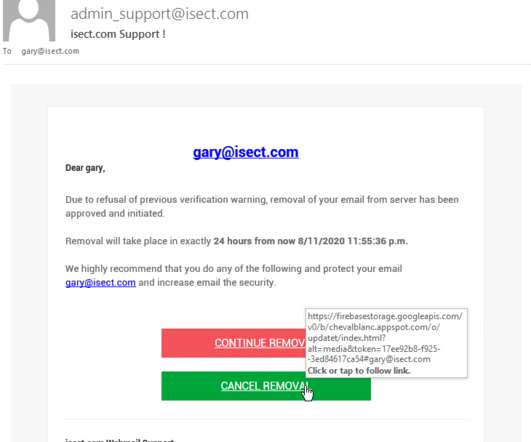
Social engineering has become a larger threat to the healthcare industry in recent years. Clearly, we need to take notice of how social engineering attacks are targeting our vital healthcare systems. So, what exactly is social engineering? What is Social Engineering? In one case, $3.1























Let's personalize your content