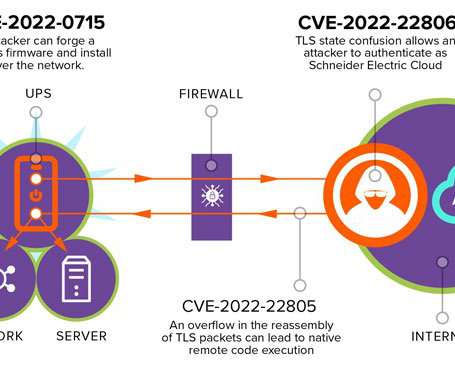
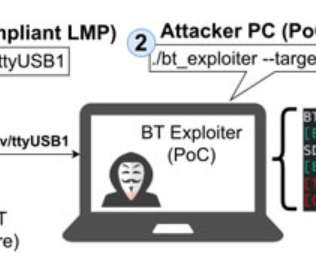
IoT Unravelled Part 3: Security
Troy Hunt
NOVEMBER 25, 2020
In part 1 of this series, I posited that the IoT landscape is an absolute mess but Home Assistant (HA) does an admirable job of tying it all together. I also looked at custom firmware and soldering and why, to my mind, that was a path I didn't need to go down at this time. Now for the big challenge - security. Let's dive into it.










































Let's personalize your content