How to defend your organization against social engineering attacks
Tech Republic Security
NOVEMBER 5, 2020
A security awareness program backed by multi-factor authentication can help protect your critical assets, says NordVPN Teams.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Tech Republic Security
NOVEMBER 5, 2020
A security awareness program backed by multi-factor authentication can help protect your critical assets, says NordVPN Teams.

CyberSecurity Insiders
MAY 1, 2023
Social engineering is a term used to describe the manipulation of people into revealing sensitive information or performing actions that they otherwise wouldn’t. Social engineering is an age-old tactic that is often used in phishing attacks. In conclusion, social engineering is a significant threat to cybersecurity.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
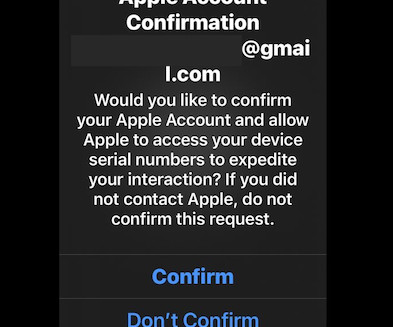
Krebs on Security
JANUARY 7, 2025
Lookout researchers discovered multiple voice phishing groups were using a new phishing kit that closely mimicked the single sign-on pages for Okta and other authentication providers. Each participant in the call has a specific role, including: -The Caller: The person speaking and trying to social engineer the target.

Security Affairs
SEPTEMBER 2, 2023
Identity services provider Okta warned customers of social engineering attacks carried out by threat actors to obtain elevated administrator permissions. Okta is warning customers of social engineering attacks carried out in recent weeks by threat actors to obtain elevated administrator permissions.

Schneier on Security
OCTOBER 21, 2021
Roger Grimes on why multifactor authentication isn’t a panacea : The first time I heard of this issue was from a Midwest CEO. His organization had been hit by ransomware to the tune of $10M. Operationally, they were still recovering nearly a year later. And, embarrassingly, it was his most trusted VP who let the attackers in.

Security Through Education
FEBRUARY 20, 2024
In the ever-evolving landscape of cybersecurity, social engineering has undergone significant transformations over the years, propelled by advancements in technology. This article delves into the historical shifts in social engineering tactics and explores how adversaries embrace new technologies to achieve their objectives.

SecureWorld News
NOVEMBER 8, 2023
Social engineering attacks have long been a threat to businesses worldwide, statistically comprising roughly 98% of cyberattacks worldwide. Given the much more psychologically focused and methodical ways that social engineering attacks can be conducted, it makes spotting them hard to do.

Krebs on Security
NOVEMBER 9, 2024
“This is social engineering at the highest level and there will be failed attempts at times. “In terms of overall social engineering attacks, the more you have a relationship with someone the more they’re going to trust you,” Donahue said. Don’t be discouraged.

SecureWorld News
APRIL 28, 2025
The phishing game has evolved into synthetic sabotage a hybrid form of social engineering powered by AI that can personalize, localize, and scale attacks with unnerving precision. At the heart of many of these kits are large language models (LLMs) trained or fine-tuned specifically for social engineering tasks.

SecureWorld News
FEBRUARY 15, 2024
A sophisticated form of mobile malware dubbed "GoldPickaxe" has been uncovered, which collects facial recognition data to produce deepfake videos, enabling hackers to bypass biometric authentication protections on banking apps. The hackers rely heavily on social engineering tactics to distribute the malware.

Duo's Security Blog
DECEMBER 14, 2023
But as it turns out, John was a victim of a phishing scam, a type of social engineering attack where the cybercriminal impersonated John’s IT department to gain his trust and trick him into revealing his login credentials. What is social engineering? If it is, access is granted.

Krebs on Security
AUGUST 21, 2020
” The perpetrators focus on social engineering new hires at the targeted company, and impersonate staff at the target company’s IT helpdesk. Consider using a formalized authentication process for employee-to-employee communications made over the public telephone network where a second factor is used to.

SecureWorld News
APRIL 22, 2025
This incident highlights the critical vulnerability in cryptocurrency communities, where high-net-worth individuals or executives may be more prone to social engineering attacks due to the high volume of media and investor engagement they handle. This adds an additional layer of protection in the event of credential theft.
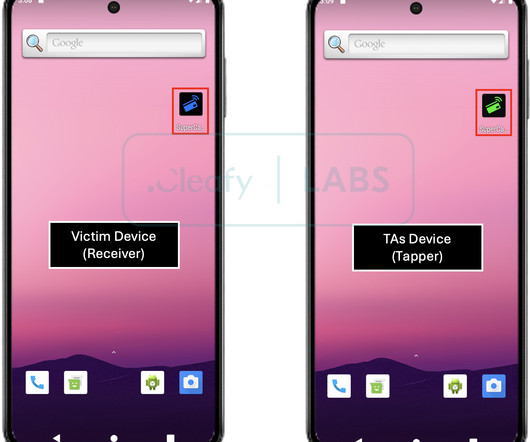
Security Affairs
APRIL 21, 2025
The malware is delivered via social engineering, attackers attempt to trick victims into tapping cards on infected phones. Calls enable social engineering in a Telephone-Oriented Attack Delivery (TOAD) scenario. Analysis of the SuperCard X campaign in Italy revealed custom malware builds tailored for regional use.

The Hacker News
FEBRUARY 12, 2024
When it comes to access security, one recommendation stands out above the rest: multi-factor authentication (MFA). With passwords alone being simple work for hackers, MFA provides an essential layer of protection against breaches. However, it's important to remember that MFA isn't foolproof. It can be bypassed, and it often is.

Krebs on Security
OCTOBER 20, 2023
Okta , a company that provides identity tools like multi-factor authentication and single sign-on to thousands of businesses, has suffered a security breach involving a compromise of its customer support unit, KrebsOnSecurity has learned. He said that on Oct 2.,
Schneier on Security
SEPTEMBER 17, 2020
When, say, an iPhone is getting ready to pair up with Bluetooth-powered device, CTKD’s role is to set up two separate authentication keys for that phone: one for a “Bluetooth Low Energy” device, and one for a device using what’s known as the “Basic Rate/Enhanced Data Rate” standard.
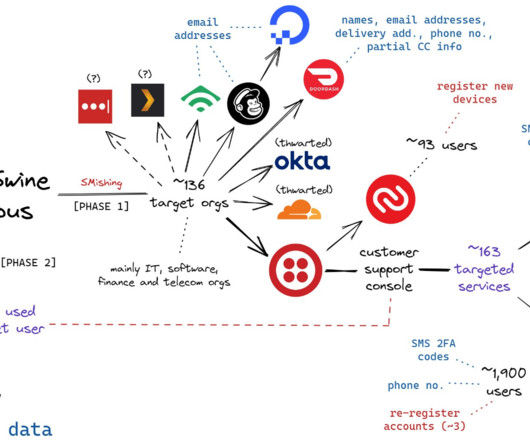
Krebs on Security
NOVEMBER 21, 2024
The targeted SMS scams asked employees to click a link and log in at a website that mimicked their employer’s Okta authentication page. Some SMS phishing messages told employees their VPN credentials were expiring and needed to be changed; other phishing messages advised employees about changes to their upcoming work schedule.

SecureWorld News
FEBRUARY 13, 2025
Evolution of social engineering Social engineering exploits human psychology to manipulate individuals into revealing sensitive information or taking harmful actions. Attacks on identity verification systems Bypassing biometric security: Many organizations use facial and voice recognition for authentication.
Krebs on Security
FEBRUARY 26, 2023
GoDaddy described the incident at the time in general terms as a social engineering attack, but one of its customers affected by that March 2020 breach actually spoke to one of the hackers involved. But we do know the March 2020 attack was precipitated by a spear-phishing attack against a GoDaddy employee.

The Last Watchdog
MARCH 28, 2025
Rather, this attack targets the victim’s digital identity, taking advantage of the widespread shift toward cloud-based enterprise storage and the fact that browser-based authentication is the primary gateway to accessing these resources.

The Last Watchdog
JULY 24, 2023
Today, bad actors are ruthlessly skilled at cracking passwords – whether through phishing attacks, social engineering, brute force, or buying them on the dark web. The next big thing is passwordless authentication. First and foremost, most solutions rely on connected devices like mobile phones to authenticate users.

The Last Watchdog
NOVEMBER 19, 2023
As the companies face nine federal lawsuits for failing to protect customer data, it’s abundantly clear hackers have checkmated multi-factor authentication (MFA). But the coup de gras was how easily they brushed aside the multi-factor authentication protections. How they steamrolled multi-factor authentication is a reason for pause.

The Last Watchdog
JANUARY 30, 2025
The extension then silently authenticates the victim into a Chrome profile managed by the attackers Google Workspace. Once this authentication occurs, the attacker has full control over the newly managed profile in the victims browser, allowing them to push automated policies such as disabling safe browsing and other security features.

IT Security Guru
FEBRUARY 25, 2025
A prime example is multi-factor authentication (MFA), a security process that requires users to verify their identity in two or more ways, such as a password, a code sent to their phone, or a fingerprint. Other Ways Threat Actors Exploit Human Behaviour In addition to fatigue attacks, malefactors weaponise social engineering.
SecureWorld News
FEBRUARY 25, 2025
One of the report's most pressing concerns is the role of Generative AI in social engineering attacks. From the report: "Generative AI is being used to create highly convincing phishing emails, fake voices, and even deepfake videosmaking social engineering attacks more difficult to detect.

Krebs on Security
AUGUST 19, 2020
Allen said a typical voice phishing or “vishing” attack by this group involves at least two perpetrators: One who is social engineering the target over the phone, and another co-conspirator who takes any credentials entered at the phishing page and quickly uses them to log in to the target company’s VPN platform in real-time.

SecureWorld News
JANUARY 22, 2025
Additionally, these conventional tools lack the contextual awareness needed to identify sophisticated social engineering tactics employed by AI-powered phishing campaigns. Multi-factor authentication (MFA) : Enforce robust MFA protocols to add an extra layer of security.

Krebs on Security
NOVEMBER 21, 2020
In response to questions from KrebsOnSecurity, GoDaddy acknowledged that “a small number” of customer domain names had been modified after a “limited” number of GoDaddy employees fell for a social engineering scam. authenticate the phone call before sensitive information can be discussed. and 11:00 p.m.

Security Affairs
NOVEMBER 15, 2024
The malware could harvest a huge trove of data from infected systems, including cookies, autofill, cryptocurrency wallets, 2FA authenticators, password managers, and email client information. Researchers from Gen Digital who discovered the threat, believe it is in its early development phase.

Schneier on Security
MAY 1, 2019
These mechanisms may also rely on security keys, but chances are that they don't (and somewhere down the line, there's probably a fallback mechanism that uses SMS, or Google Authenticator, or an email confirmation loop, or a password, or an administrator who can be sweet talked by a social engineer).

Krebs on Security
APRIL 6, 2022
“They would just keep jamming a few individuals to get [remote] access, read some onboarding documents, enroll a new 2FA [two-factor authentication method] and exfiltrate code or secrets, like a smash-and-grab,” the CXO said. ” Like LAPSUS$, these vishers just kept up their social engineering attacks until they succeeded.

Bleeping Computer
SEPTEMBER 15, 2023
Software company Retool says the accounts of 27 cloud customers were compromised following a targeted and multi-stage social engineering attack. [.]

Malwarebytes
JULY 30, 2024
If you were trying to download the popular Google Authenticator (a multi-factor authentication program) via a Google search in the past few days, you may have inadvertently installed malware on your computer. Fake site leads to signed payload hosted on Github The fraudulent site chromeweb-authenticators[.]com
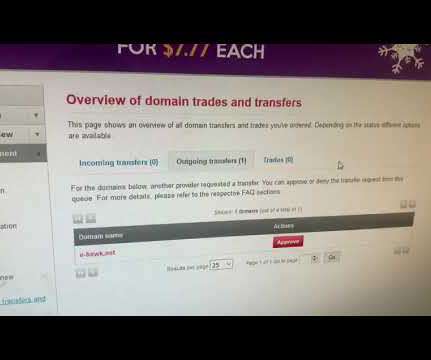
Krebs on Security
JANUARY 24, 2020
In the case of e-hawk.net, however, the scammers managed to trick an OpenProvider customer service rep into transferring the domain to another registrar with a fairly lame social engineering ruse — and without triggering any verification to the real owners of the domain. ” REGISTRY LOCK.

SecureWorld News
NOVEMBER 6, 2024
Google moved away from VPNs, instead using device-based authentication and continuous access verification, ensuring that each access request is authenticated. Deepfake social engineering: Deepfakes can mimic legitimate users to manipulate access. Take Google's BeyondCorp as an example.

eSecurity Planet
OCTOBER 22, 2024
Cybercriminals employ social engineering techniques to trick you into believing you must resolve fictitious technical issues. The hallmark of ClickFix campaigns is their clever use of social engineering. Enable multi-factor authentication (MFA): Implementing MFA adds layer of security to your accounts.
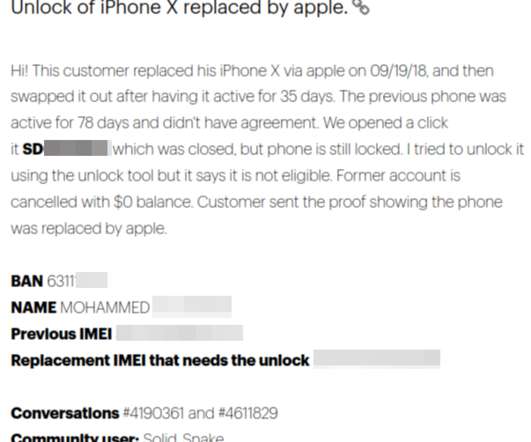
Krebs on Security
JANUARY 29, 2020
KrebsOnSecurity recently contacted Sprint to let the company know that an internal customer support forum called “Social Care” was being indexed by search engines, and that several months worth of postings about customer complaints and other issues were viewable without authentication to anyone with a Web browser.

The Last Watchdog
APRIL 22, 2025
As AI technology advances, attackers are shifting their focus from technical exploits to human emotions using deeply personal and well-orchestrated social engineering tactics. Typically, the attacker collects authentic media samples of their target, including still images, videos, and audio clips, to train the deep learning model.

Security Affairs
APRIL 7, 2025
Guidebooks are also available to instruct on how to exploit the information obtained, in order to more effectively target victims through social engineering and doxxing campaigns. The lack of a robust verification process, combined with the trust placed in authorities, increases the risk to users’ digital security and privacy.

eSecurity Planet
NOVEMBER 6, 2024
Rhysida went so far as to publish sample files to verify the authenticity of the data, revealing access to a trove of information, including city databases, employee credentials, cloud management files, and even the city’s traffic camera feeds.

Krebs on Security
JANUARY 30, 2024
2022 that an intrusion had exposed a “limited number” of Twilio customer accounts through a sophisticated social engineering attack designed to steal employee credentials. The missives asked users to click a link and log in at a phishing page that mimicked their employer’s Okta authentication page.

Krebs on Security
JUNE 15, 2024
.” In a SIM-swapping attack, crooks transfer the target’s phone number to a device they control and intercept any text messages or phone calls sent to the victim — including one-time passcodes for authentication, or password reset links sent via SMS.

SecureWorld News
FEBRUARY 6, 2025
However, even seemingly limited breaches can have downstream effects, enabling phishing attacks and social engineering schemes. Mandate multi-factor authentication (MFA) Require MFA for all vendor accounts accessing critical systems. How did this happen?
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content