Apple to Add Manual Authentication to iMessage
Schneier on Security
NOVEMBER 22, 2023
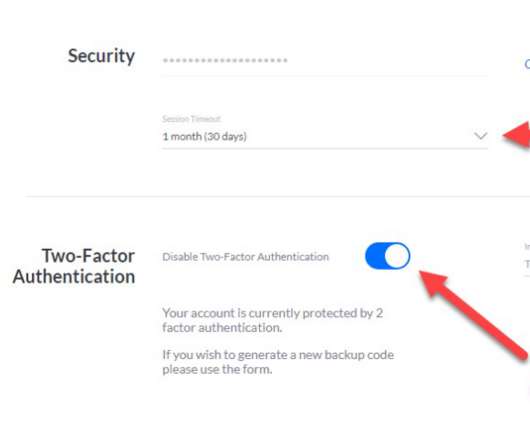
Signal has had the ability to manually authenticate another account for years. Instead of relying on Apple to verify the other person’s identity using information stored securely on Apple’s servers, you and the other party read a short verification code to each other, either in person or on a phone call.




































Let's personalize your content