Recent Cyber Attacks: Trends, Tactics, and Countermeasures
Hacker's King
DECEMBER 16, 2024
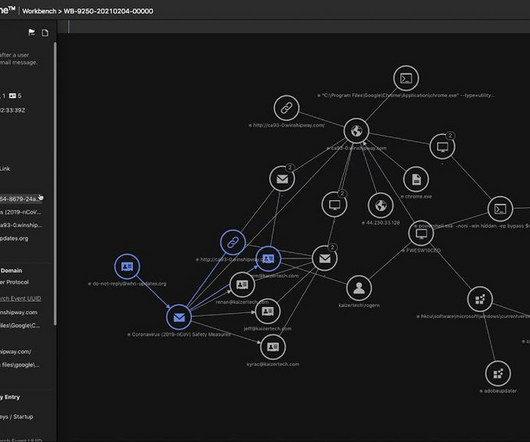
The use of artificial intelligence and machine learning has enabled hackers to automate their attacks, making them more efficient and harder to detect. Cybercriminals are also increasingly using social media to gather intelligence, exploit personal information, and initiate attacks.























Let's personalize your content