3 ways criminals use artificial intelligence in cybersecurity attacks
Tech Republic Security
OCTOBER 7, 2020
Bad actors use machine learning to break passwords more quickly and build malware that knows how to hide, experts warn.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Tech Republic Security
OCTOBER 7, 2020
Bad actors use machine learning to break passwords more quickly and build malware that knows how to hide, experts warn.
Security Affairs
FEBRUARY 19, 2020
Artificial intelligence is an immensely helpful tool for businesses and consumers alike, how to use artificial intelligence to secure sensitive Information. Artificial intelligence (AI) is an immensely helpful tool for businesses and consumers alike. Password Protection & Authentication.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Affairs
JANUARY 3, 2024
Crooks created a new tool that uses Artificial Intelligence (AI) for creating fraudulent invoices used for wire fraud and BEC. These posts introduced a new tool that incorporates Artificial Intelligence (AI) for creating fraudulent invoices used for wire fraud and Business E-Mail Compromise (BEC).

The Last Watchdog
JANUARY 31, 2022
We all rely on passwords. For better or worse, we will continue to use passwords to access our computing devices and digital services for years to come. Related : The coming of password-less access. Passwords were static to begin with. They have since been modified in two directions: biometrics and dynamic passwords.
eSecurity Planet
MARCH 31, 2025
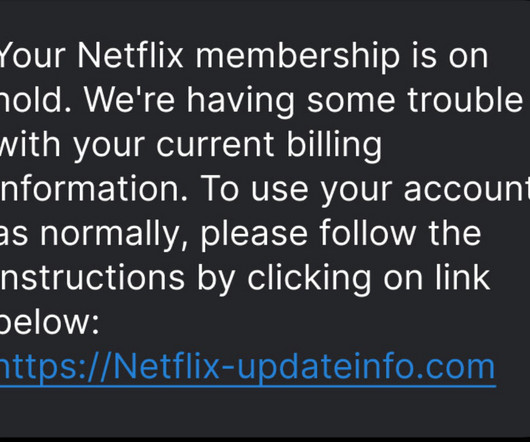
The rise in artificial intelligence and advanced phishing methods has made it even harder. If they log in, now their username and password belong to the hacker, Zilberstein explained. Use a strong, unique password for your Netflix account. They can now access the account, which contains financial information.

Krebs on Security
NOVEMBER 1, 2024
Booking.com said it now requires 2FA , which forces partners to provide a one-time passcode from a mobile authentication app (Pulse) in addition to a username and password. .” The phony booking.com website generated by visiting the link in the text message. million phishing attempts in 2023.”

SecureWorld News
APRIL 13, 2025
This is where Artificial Intelligence (AI) steps in. Hence, it is evident that artificial intelligence is revolutionizing the cybersecurity industry by providing quicker, more accurate, and more efficient ways to detect cyber attacks. Cyber threats evolve daily, often outpacing traditional security measures.

Malwarebytes
JANUARY 30, 2025
For those returning from a short holiday away from the news, DeepSeek is a new player on the Artificial Intelligence (AI) field. The sudden rise of DeepSeek has raised concerns and questions, especially about the origin and destination of the training data, as well as the security of the data.

Joseph Steinberg
DECEMBER 5, 2022
Change your password often. The post Cybersecurity for Seniors: Easy and Practical Advice – A Free Webinar With Joseph Steinberg, Author of Cybersecurity For Dummies appeared first on Joseph Steinberg: CyberSecurity Expert Witness, Privacy, Artificial Intelligence (AI) Advisor. Don’t open attachments.

Malwarebytes
JANUARY 6, 2022
Credential stuffing is the automated injection of stolen username and password pairs in to website login forms, in order to fraudulently gain access to user accounts. Besides listening to us telling you that you should not reuse passwords across multiple platforms, there are some other thing you can do. Start using a password manager.

Malwarebytes
FEBRUARY 13, 2025
In May, 2024, the FBI warned about the increasing threat of cybercriminals using Artificial Intelligence (AI) in their scams. And if cybercriminals manage to steal the session cookie, they can log in as you, change the password and grab control of your account.

Malwarebytes
APRIL 1, 2025
A researcher found millions of pictures from specialized dating apps for iOS stored online without any kind of password protection. To his surprise, he could access the unencrypted and otherwise unprotected photos without needing any password. The five platforms, all developed by M.A.D.
eSecurity Planet
FEBRUARY 10, 2025
With cybercriminals using advanced artificial intelligence algorithms to create more convincing fraudulent messages, the FBIs message is simple and uncompromising: Do not click on anything. AI-Enhanced Cyberthreats Recent intelligence indicates that the sophistication of Gmail phishing campaigns has reached new heights.

Malwarebytes
APRIL 1, 2025
Entering your password will send your credentials to a Russian receiver, who will decide what the most profitable way to use them is. Malwarebytes blocks fmhjhctk.ru Perhaps they’ll sell the details on the dark web, or use them for themselves to get access to your Microsoft accounts.

Malwarebytes
DECEMBER 12, 2023
As if password authentication’s coffin needed any more nails, researchers in the UK have discovered yet another way to hammer one in. For example, when typing a password, people will regularly hide their screen but will do little to obfuscate their keyboard’s sound.
Joseph Steinberg
MARCH 15, 2021
You can stop unauthorized devices from connecting to your network by not giving out your Wi-Fi password; it is simple to avoid giving your children your Wi-Fi password, for example, by manually configuring the Wi-Fi settings on ther devices. Keep in mind that: 1.

Malwarebytes
DECEMBER 12, 2023
As if password authentication’s coffin needed any more nails, researchers in the UK have discovered yet another way to hammer one in. For example, when typing a password, people will regularly hide their screen but will do little to obfuscate their keyboard’s sound.

Bleeping Computer
APRIL 5, 2024
Hackers are using Facebook advertisements and hijacked pages to promote fake Artificial Intelligence services, such as MidJourney, OpenAI's SORA and ChatGPT-5, and DALL-E, to infect unsuspecting users with password-stealing malware. [.]

Malwarebytes
APRIL 16, 2025
The rise in bots is down to generative artificial intelligence (AI), Imperva said. This is where a bot takes a password and email address that has been stolen and leaked online, and then tries those credentials across a myriad of services in the hope that its owner will have reused the password elsewhere. Protect your PC.

Webroot
MARCH 3, 2025
Common attacks to consumer protection Identity theft and fraud Some common types of identity theft and fraud include account takeover fraud , when criminals use stolen personal information such as account numbers, usernames, or passwords to hijack bank accounts, credit cards, and even email and social media accounts.
Malwarebytes
OCTOBER 22, 2024
Social media accounts are often lost when users forget their password, switch devices, or when they inadvertently or even willingly give their credentials to a scammer. Do I want to provide Meta with even more material that might end up getting used to train its Artificial Intelligence (AI) models?

Security Boulevard
MARCH 22, 2022
Motivation Sensitive information like passwords, API keys, access tokens, asymmetric private keys, client secrets and credentials are critical components of a secure internet. The post New Chariot Module Nosey Parker Released: An Artificial Intelligence Based Secrets Scanner That Out Sniffs the Competition appeared first on Praetorian.

The Last Watchdog
DECEMBER 6, 2022
Consider that some 80 percent of hacking-related breaches occur because of weak or reused passwords, and that over 90 percent of consumers continue to re-use their intrinsically weak passwords. Authentication systems that leverage machine learning and biometric technology are now ready to replace legacy password-centric technologies.

Joseph Steinberg
JANUARY 19, 2022
The post What Damage Can Happen If Data Leaks When Quantum Computing Breaks Today’s Encryption appeared first on Joseph Steinberg: CyberSecurity, Privacy, & Artificial Intelligence (AI) Advisor. But, with the arrival of powerful quantum computers, any data that is captured now can potentially be decrypted tomorrow.

Dark Reading
JULY 17, 2023
Artificial intelligence can be tricked into making password-based authentication even weaker.

SecureWorld News
OCTOBER 13, 2024
The emergence of artificial intelligence (AI) has also transcended these experiences. This evolving field of computer science focuses on creating intelligent machines powered by smart algorithms that make routine task performance easier, alleviating the need for human intelligence or manual involvement.

Tech Republic Security
JULY 28, 2017
Lastwall co-founder and CEO Karl Holmqvist explains how artificial intelligence could could soon eliminate the need for password-based security.

Security Boulevard
MARCH 24, 2025
A Cato Networks threat researcher with little coding experience was able to convince AI LLMs from DeepSeek, OpenAI, and Microsoft to bypass security guardrails and develop malware that could steal browser passwords from Google Chrome.

The Security Ledger
NOVEMBER 6, 2019
In this episode of the podcast (#166): Jay Budzik, the Chief Technology Officer at ZestAI, joins us to talk about that company's push to make artificial intelligence decisions explainable and how his company's technology is helping to root out synthetic identity fraud. Also: making Passwords work.

Hacker's King
DECEMBER 24, 2024
Here are the top 10 trends to watch out for in 2025: Rise of AI-Driven Cyberattacks Cybercriminals are increasingly leveraging artificial intelligence (AI) to develop sophisticated attack methods. Biometric Authentication on the Rise Traditional passwords are increasingly seen as inadequate for modern security needs.

Malwarebytes
SEPTEMBER 17, 2024
One of the most promising new features is the new Passwords app. Built on the foundation of Apple’s password management system Keychain, Passwords makes it easier for users to access stored passwords and get an overview of their credentials. And, admittedly, many of them come with a learning curve.

Thales Cloud Protection & Licensing
OCTOBER 30, 2024
Unlike traditional misinformation, which can be spread unintentionally, malinformation is designed with malicious intent, and artificial intelligence makes it even more insidious. Even if a cyber creature cracks your password, MFA can stop them in their tracks.
Malwarebytes
NOVEMBER 19, 2024
A large social media campaign was launched to promote a free Artificial Intelligence (AI) video editor. AMOS makes money for its operators by finding and stealing valuable information on the computers it infects, such as credit card details, authentication cookies, passwords and cryptocurrency.

The Last Watchdog
APRIL 10, 2019
The good news is that OneSpan and other security vendors are innovating to bring machine learning, data analytics and artificial intelligence to the front lines. In the not-so-distant past, banks dealt with online and account takeover fraud, where hackers stole passwords and used phishing scams to target specific individuals.

Joseph Steinberg
JULY 17, 2023
Classified data must remain offline The present leak did expose sensitive information, which, according to the Financial Times, included, in addition the aforementioned items, diplomatic documents, tax returns, travel details of top officers, and even passwords (why those were exposed in an email leak is a separate question mandating attention.)

CyberSecurity Insiders
NOVEMBER 16, 2022
Microsoft has announced that it is going to collaborate with GPU maker NVIDIA to build an Artificial Intelligence powered Supercomputer in the Azure cloud. Since reporting challenges make security and license management compulsive, redundant risks and costs are also being observed, says Microsoft 365 Security Benchmark Report.

Tech Republic Security
JULY 26, 2017
Lastwall co-founder and CEO Karl Holmqvist explains how artificial intelligence could could soon eliminate the need for password-based security.

Security Affairs
JANUARY 19, 2025
CISA adds Aviatrix Controllers vulnerability to its Known Exploited Vulnerabilities catalog ESET detailed a flaw that could allow a bypass of the Secure Boot in UEFI systems Russia-linked APT Star Blizzard targets WhatsApp accounts Prominent US law firm Wolf Haldenstein disclosed a data breach Clop Ransomware exploits Cleo File Transfer flaw: dozens (..)

Malwarebytes
JUNE 17, 2024
Copilot+ PCs are personal computers that come equipped with several artificial intelligence (AI) features. It will not hide information such as passwords or financial account numbers. Microsoft has announced it will postpone the broadly available preview of the heavily discussed Recall feature for Copilot+ PCs.

Malwarebytes
MAY 22, 2024
On Monday, the computing giant unveiled a new line of PCs that integrate Artificial Intelligence (AI) technology to promise faster speeds, enhanced productivity, and a powerful data collection and search tool that screenshots a device’s activity—including password entry—every few seconds.

SecureWorld News
FEBRUARY 10, 2025
To stay ahead, organizations must turn to artificial intelligence. Multi-factor authentication (MFA) is also a must to prevent unauthorized access from just a stolen password. The onus is on the security teams to make it nearly impossible for someone to decrypt the hashed passwords. How can they do that?

Security Affairs
JANUARY 7, 2024
Experts spotted a new macOS Backdoor named SpectralBlur linked to North Korea Merck settles with insurers regarding a $1.4

Thales Cloud Protection & Licensing
MARCH 24, 2024
However, while improvements in CIAM, such as passkeys and password deprecation, enhance user experience, they also introduce new challenges like deepfake attacks from generative AI, and simplifying this complexity is crucial to reducing opportunities for adversaries and improving usability and engagement.

Joseph Steinberg
OCTOBER 20, 2022
The system states explicitly that passwords are not treated as case sensitive , and that four special characters — < > — are not allowed to be used in passwords.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content