Drovorub Malware
Schneier on Security
AUGUST 14, 2020
The NSA and FBI have jointly disclosed Drovorub, a Russian malware suite that targets Linux. News articles. Detailed advisory. Fact sheet. Reddit thread.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Schneier on Security
AUGUST 14, 2020
The NSA and FBI have jointly disclosed Drovorub, a Russian malware suite that targets Linux. News articles. Detailed advisory. Fact sheet. Reddit thread.

Schneier on Security
MARCH 2, 2021
This is weird : Once an hour, infected Macs check a control server to see if there are any new commands the malware should run or binaries to execute. So far, however, researchers have yet to observe delivery of any payload on any of the infected 30,000 machines, leaving the malware’s ultimate goal unknown. Another article.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Schneier on Security
JULY 27, 2021
Interesting research: “EvilModel: Hiding Malware Inside of Neural Network Models” Abstract: Delivering malware covertly and detection-evadingly is critical to advanced malware campaigns. In this paper, we present a method that delivers malware covertly and detection-evadingly through neural network models.

Schneier on Security
JANUARY 24, 2022
Crowdstrike is reporting that malware targeting Linux has increased considerably in 2021: Malware targeting Linux systems increased by 35% in 2021 compared to 2020. XorDDoS, Mirai and Mozi malware families accounted for over 22% of Linux-targeted threats observed by CrowdStrike in 2021. Lots of details in the report.

Security Affairs
OCTOBER 13, 2024
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape. Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape. Over 300,000!

Security Affairs
OCTOBER 20, 2024
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape. Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape.

Schneier on Security
SEPTEMBER 17, 2024
Interesting social engineering attack: luring potential job applicants with fake recruiting pitches, trying to convince them to download malware. The capacity for exploitation at that point is pretty much unlimited, due to the flexibility of Python and how it interacts with the underlying OS.
Krebs on Security
MAY 18, 2020
Almost daily now there is news about flaws in commercial software that lead to computers getting hacked and seeded with malware. Here’s a look at one long-lived malware vulnerability testing service that is used and run by some of the Dark Web’s top cybercriminals. RedBear’s profile on the Russian-language xss[.]is

Schneier on Security
SEPTEMBER 12, 2022
It’s pretty nasty : The malware was dubbed “ Shikitega ” for its extensive use of the popular Shikata Ga Nai polymorphic encoder, which allows the malware to “mutate” its code to avoid detection. Another article. Slashdot thread.

Schneier on Security
MARCH 30, 2021
From a news article : The broad range of data that this sneaky little bastard is capable of stealing is pretty horrifying. This is a sophisticated piece of malware. Researchers have discovered a new Android app called “System Update” that is a sophisticated Remote-Access Trojan (RAT).

Schneier on Security
MAY 9, 2023
Another nation-state malware , Russian in origin: In the early stages of the war in Ukraine in 2022, PIPEDREAM, a known malware was quietly on the brink of wiping out a handful of critical U.S. Wired article. electric and liquid natural gas sites. CISA advisory.

Schneier on Security
APRIL 14, 2022
The Department of Energy, CISA, the FBI, and the NSA jointly issued an advisory describing a sophisticated piece of malware called Pipedream that’s designed to attack a wide range of industrial control systems. There’s also no indication of how the malware was discovered. News article. More information.

Security Affairs
APRIL 6, 2025
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape CISA Releases Malware Analysis Report on RESURGE Malware Associated with Ivanti Connect Secure Unboxing Anubis: Exploring the Stealthy Tactics of FIN7’s Latest Backdoor Advancements in delivery: Scripting with (..)

Security Affairs
APRIL 20, 2025
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape Malicious NPM Packages Targeting PayPal Users New Malware Variant Identified: ResolverRAT Enters the Maze Nice chatting with you: what connects cheap Android smartphones, WhatsApp and cryptocurrency theft?

Schneier on Security
JUNE 30, 2022
Wired is reporting on a new remote-access Trojan that is able to infect at least eighty different targets: So far, researchers from Lumen Technologies’ Black Lotus Labs say they’ve identified at least 80 targets infected by the stealthy malware, including routers made by Cisco, Netgear, Asus, and DrayTek.

Security Affairs
APRIL 13, 2025
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape Lazarus Expands Malicious npm Campaign: 11 New Packages Add Malware Loaders and Bitbucket Payloads BadBazaar: iOS and Android Surveillanceware by Chinas APT15 Used to Target Tibetans and Uyghurs GOFFEE continues to attack (..)

Security Affairs
DECEMBER 1, 2024
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape.
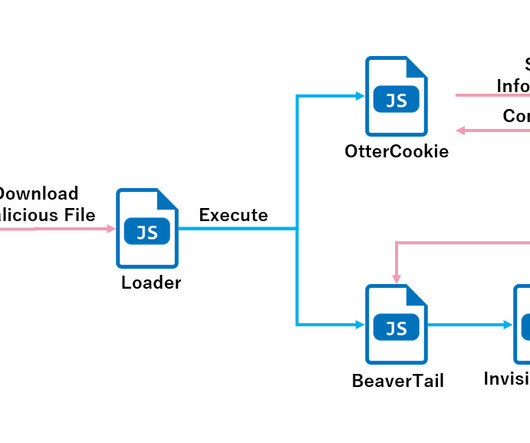
Security Affairs
DECEMBER 27, 2024
North Korea-linked threat actors were spotted using new malware called OtterCookie as part of the Contagious Interview campaign that targets software developer community with fake job offers. Since November 2024, threat actors employed the malware OtterCookie, alongside BeaverTail and InvisibleFerret, in the campaign.

Security Affairs
FEBRUARY 2, 2025
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape.

Security Affairs
FEBRUARY 9, 2025
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape.

Security Affairs
MARCH 30, 2025
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape Microsoft Trusted Signing service abused to code-sign malware Shedding light on the ABYSSWORKER driver VSCode Marketplace Removes Two Extensions Deploying Early-Stage Ransomware New Android Malware Campaigns Evading (..)

Schneier on Security
APRIL 12, 2023
The FBI is warning people against using public phone-charging stations, worrying that the combination power-data port can be used to inject malware onto the devices: Avoid using free charging stations in airports, hotels, or shopping centers. News article. Carry your own charger and USB cord and use an electrical outlet instead.

Schneier on Security
JUNE 22, 2022
Interesting : What makes Symbiote different from other Linux malware that we usually come across, is that it needs to infect other running processes to inflict damage on infected machines. So far, there’s no evidence of infections in the wild, only malware samples found online. No public attribution yet.

Security Affairs
FEBRUARY 16, 2025
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape.

Schneier on Security
NOVEMBER 20, 2020
The group is using living-off-the-land tools as well as custom malware in this attack campaign, including a custom malware — Backdoor.Hartip — that Symantec has not seen being used by the group before. News article. Interesting details about the group’s tactics.

Security Affairs
MARCH 9, 2025
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape.

Security Affairs
JANUARY 12, 2025
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape.

Security Affairs
JANUARY 19, 2025
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape.

Security Affairs
MARCH 23, 2025
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape Decrypting Encrypted files from Akira Ransomware (Linux/ESXI variant 2024) using a bunch of GPUs Jaguar Land Rover Breached by HELLCAT Ransomware Group Using Its Infostealer PlaybookThen a Second Hacker Strikes ClearFakes (..)

Security Affairs
JANUARY 5, 2025
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape.

Security Affairs
JANUARY 26, 2025
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape.

Security Affairs
DECEMBER 29, 2024
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape. Now You See Me, Now You Dont: Using LLMs to Obfuscate Malicious JavaScript Analyzing Malicious Intent in Python Code: A Case Study DigiEver Fix That IoT Thing!

Security Affairs
FEBRUARY 23, 2025
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape. You’ve Got Malware: FINALDRAFT Hides in Your Drafts Telegram Abused as C2 Channel for New Golang Backdoor Infostealing Malware Infections in the U.S.

Security Affairs
MARCH 2, 2025
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape.
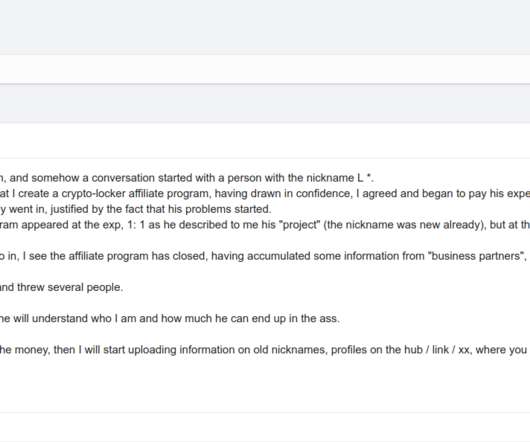
Security Affairs
OCTOBER 27, 2024
They were convicted of illegal payment handling, with Puzyrevsky and Khansvyarov also found guilty of malware use and distribution. They were found guilty of illegal payment handling, while Puzyrevsky and Khansvyarov were also convicted of using and distributing malware. “On Friday, October 25, the St.

Schneier on Security
JULY 2, 2021
The first is from Microsoft, which wrote : As part of our investigation into this ongoing activity, we also detected information-stealing malware on a machine belonging to one of our customer support agents with access to basic account information for a small number of our customers. News article. Two reports this week.

SecureList
MARCH 10, 2025
Last year, we published an article about SideWinder , a highly prolific APT group whose primary targets have been military and government entities in Pakistan, Sri Lanka, China, and Nepal. Once their tools are identified, they respond by generating a new and modified version of the malware, often in under five hours.

Graham Cluley
OCTOBER 24, 2024
Historically, Mac users haven't had to worry about malware as much as their Windows-using cousins. And the recent discovery of a new malware strain emphasises that the threat - even if much smaller than on Windows - remains real. Read more in my article on the Tripwire State of Security blog.

Security Affairs
NOVEMBER 24, 2024
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape. Android Malware Detection Based on Behavioral-Level Features with Graph Convolutional Networks.
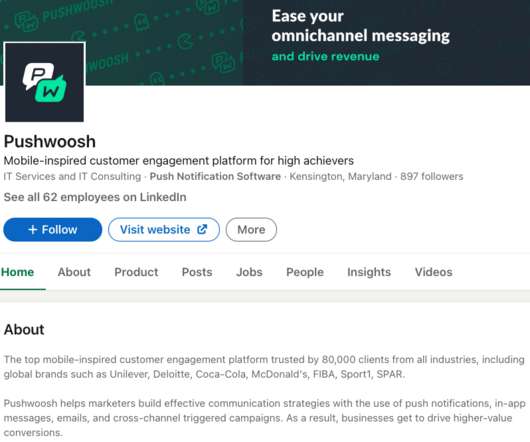
Krebs on Security
NOVEMBER 28, 2022
But that story omitted an important historical detail about Pushwoosh: In 2013, one of its developers admitted to authoring the Pincer Trojan , malware designed to surreptitiously intercept and forward text messages from Android mobile devices. ” wherein Shmakov acknowledged writing the malware as a freelance project.

Security Affairs
MARCH 28, 2025
“Preliminary findings indicate that the suspects developed malware called Mamont, which they distributed via Telegram channels under the guise of safe mobile applications and video files. Mamont spreads via Telegram, Mamont malware is delivered through Telegram channels.

Security Affairs
SEPTEMBER 29, 2024
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape. Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape.

Security Affairs
JULY 28, 2024
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape. Follow me on Twitter: @securityaffairs and Facebook and Mastodon Pierluigi Paganini ( SecurityAffairs – hacking, newsletter)
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content