Largest Recorded DDoS Attack is 3.8 Tbps
Schneier on Security
OCTOBER 7, 2024
CLoudflare just blocked the current record DDoS attack: 3.8 Lots of good information on the attack, and DDoS in general, at the link.) News article. terabits per second.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Schneier on Security
OCTOBER 7, 2024
CLoudflare just blocked the current record DDoS attack: 3.8 Lots of good information on the attack, and DDoS in general, at the link.) News article. terabits per second.

Schneier on Security
MAY 5, 2022
Cloudflare is reporting a large DDoS attack against an unnamed company “operating a crypto launchpad.” HTTPS DDoS attacks are more expensive in terms of required computational resources because of the higher cost of establishing a secure TLS encrypted connection. News article. The attack only lasted 15 seconds.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Hacker News
SEPTEMBER 15, 2023
The Internet of Things (IoT) is transforming efficiency in various sectors like healthcare and logistics but has also introduced new security risks, particularly IoT-driven DDoS attacks. This article explores how these attacks work, why they’re uniquely problematic, and how to mitigate them. What Is IoT?

CyberSecurity Insiders
APRIL 1, 2022
As CIOs and CTOs are getting extremely worried about distributed denial of service attacks (DDoS), here’s a brief article that can help to enlighten their mind on protecting their corporate networks, without the need of any professional help. Running a DDoS Testing- It is essential, although it is a 3 hour effort to conduct.

Security Affairs
OCTOBER 13, 2024
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape. Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape. Over 300,000!

CSO Magazine
AUGUST 18, 2022
Google Cloud has claimed to have blocked the largest Layer 7 (HTTPS) DDoS attack to date after a Cloud Armor customer was targeted by a series of attacks that peaked at 46 million requests per second (rps). To read this article in full, please click here

SecureList
NOVEMBER 8, 2021
Q3 2021 brought two new DDoS attack vectors, potentially posing a serious threat, including for major web resources. ris , a new botnet capable of carrying out powerful DDoS attacks. For instance, a DDoS attack on a Cloudflare customer (attributed to M?ris) We won't let our #DDoS stop us doing what we love!

SecureList
FEBRUARY 10, 2022
Q4 2021 saw the appearance of several new DDoS botnets. In October, the botnet was upgraded with DDoS functionality. This is further evidence that the same botnets are often used for mining and DDoS. Once on the device, Moobot waits for a command from the C2 server before launching a DDoS attack.

The Hacker News
MARCH 26, 2024
Minecraft, with over 500 million registered users and 166 million monthly players, faces significant risks from distributed denial-of-service (DDoS) attacks, threatening server functionality, player experience, and the game’s reputation. This article explains
SecureList
MAY 10, 2021
Botnet operators use infected devices to carry out DDoS attacks or mine cryptocurrency. In Q1 2021, cybercriminals also found a host of new tools for amplifying DDoS attacks. RDP servers listening on UDP port 3389 were used to amplify DDoS attacks. The vendor released a patch when they learned about the problem.
Security Affairs
APRIL 28, 2020
Timetv.live is the latest Azeri news site targeted by Denial of Service (DDoS) attacks launched by Sandman threat actor, the attack took place on March 21, 2020. Just like many other DDoS attacks we have seen in the past against Azeri media, the attacker monitors the success of the floods using the HostTracker service. Conclusion.

CSO Magazine
FEBRUARY 12, 2021
What is a DDoS attack? A distributed denial of service (DDoS) attack is when an attacker, or attackers, attempt to make it impossible for a service to be delivered. In a DoS attack, it’s one system that is sending the malicious data or requests; a DDoS attack comes from multiple systems.

Security Affairs
FEBRUARY 8, 2024
Several media reported that three million electric toothbrushes were compromised and recruited into a DDoS botnet. The Swiss newspaper Aargauer Zeitung first published the news of a DDoS attack, carried out on January 30, that involved three million compromised electric toothbrushes. Is it true? What the f is wrong with you people????

CSO Magazine
JUNE 28, 2021
The 2H2020 Threat Intelligence Report correctly predicted that 2020’s record-breaking distributed denial of service (DDoS) attack activity would follow the COVID-19 pandemic into 2021. million DDoS attacks in the first quarter of 2021, a 31% increase from the same time in 2020.

Malwarebytes
AUGUST 20, 2021
On the Cloudflare blog , the American web infrastructure behemoth that provides content delivery network (CDN) and DDoS mitigation services reports that it detected and mitigated a 17.2 million request-per-second (rps) DDoS attack. The target of this enormous DDoS attack was a customer of Cloudflare in the financial sector.

Graham Cluley
JULY 23, 2024
It has been revealed that earlier this month a website which offered a DDoS-for-hire service was taken offline by law enforcement, but only after they collected data about its criminal customers. Read more in my article on the Hot for Security blog.

CSO Magazine
JULY 27, 2021
Cybersecurity is built to protect computer systems and networks from theft, damage, and service disruption from attacks such as distributed denial-of-service (DDoS). DDoS attacks work by taking a target website or online service offline by overwhelming the target or its surrounding infrastructure with a flood of internet traffic.

IT Security Guru
JANUARY 3, 2024
Swarming or DDoS attacks pose a threat to streamers. A reliable VPN provider always maintains a DDoS-protected server. In this article, we will continue to explore how a VPN can fortify your Twitch stream. In this article, we will continue to explore how a VPN can fortify your Twitch stream. link] What’s a DDoS attack?

CSO Magazine
AUGUST 16, 2021
In particular, distributed denial-of-service (DDoS) attack s have risen dramatically. The latest NETSCOUT Threat Intelligence Report revealed record-breaking DDoS activity in 2020, as attackers launched more than 10 million DDoS worldwide. To read this article in full, please click here

CSO Magazine
MARCH 9, 2022
Security researchers, network operators and security vendors have detected a new reflection/amplification distributed denial-of-service (DDoS) vulnerability actively being exploited to launch multiple high-impact DDoS attacks. To read this article in full, please click here

CSO Magazine
MAY 18, 2021
At the same time, distributed denial-of-service (DDoS) attacks, which have also traditionally been used to extort businesses, returned in force. To read this article in full, please click here (Insider Story) Ransomware groups are even using them to put additional pressure on their victims.

Schneier on Security
SEPTEMBER 7, 2022
This article makes LockBit sound like a legitimate organization: The DDoS attack last weekend that put a temporary stop to leaking Entrust data was seen as an opportunity to explore the triple extortion tactic to apply more pressure on victims to pay a ransom.

Graham Cluley
DECEMBER 15, 2022
Law enforcement agencies in the United States, UK, Netherlands, Poland, and Germany have brought down the most popular DDoS-for-hire services on the internet, responsible for tens of millions of attacks against websites. Read more in my article on the Tripwire State of Security blog.

CSO Magazine
NOVEMBER 22, 2022
Microsoft is extending the Azure DDoS Protection family with a new product focusing on small and medium-size businesses (SMBs). The product, DDoS IP Protection for SMBs, was announced at Microsoft's Ignite conference and is now in public preview. To read this article in full, please click here

CSO Magazine
APRIL 25, 2022
Larry Pesce remembers the day when the distributed denial of service (DDoS) threat landscape changed dramatically. To read this article in full, please click here It was late fall in 2016 when a fellow researcher joined him at the InGuardians lab, where he is director of research.

CSO Magazine
JUNE 11, 2021
Security researchers are tracking new DDoS extortion activity by threat actor group Fancy Lazarus. To read this article in full, please click here The attacks have been primarily targeting US and global organizations from a range of sectors including energy, financial, insurance, manufacturing, public utilities and retail.

CSO Magazine
NOVEMBER 5, 2021
Firewalls are critical, but they are not enough to protect you from Distributed Denial of Service (DDoS) attacks. You need a stateless DDoS solution like NETSCOUT Arbor Edge Defense. To read this article in full, please click here In fact, they are the main target of state exhaustion attacks. Learn more here.

CSO Magazine
FEBRUARY 24, 2023
Content delivery network ( CDN ) service provider Edgio has added a new Distributed Denial of Service ( DDoS ) scrubbing ability along with improved Web Application and API Interface (WAAP) to its network security offering. To read this article in full, please click here

CyberSecurity Insiders
APRIL 9, 2023
A DDoS (Distributed Denial of Service) attack is a common form of cyber attack that aims to disrupt the normal functioning of a network by overwhelming it with traffic. In this article, we will discuss how to detect and respond to a D DoS network cyber attack. Some common signs of a DDoS attack include: 1.)

CSO Magazine
JULY 7, 2022
million distributed denial-of-service (DDoS) attacks occurred in the second half of 2021, to know with certainty that such attacks are always happening. It’s not a matter of if a company will be impacted by a DDoS attack, it’s a matter of when. To read this article in full, please click here

CSO Magazine
JULY 21, 2022
At Netscout we continuously work with customers to discover the impact our offerings to prevent distributed denial-of-service (DDoS) are having on their ongoing security concerns and challenges. To read this article in full, please click here
Krebs on Security
JANUARY 17, 2023
Most people who operate DDoS-for-hire businesses attempt to hide their true identities and location. Prosecutors say his service attracted more than two million registered users, and was responsible for launching a staggering 30 million distinct DDoS attacks. men for allegedly operating stresser services.

CSO Magazine
SEPTEMBER 29, 2022
Cryptojacking is the most common form of attack against container- based systems running in the cloud, while geopolitical motivations—mainly related to Russia's war against Ukraine—factored into a fourfold increase in DDoS (distributed denial-of-service) attacks this year, according to a new report from cybersecurity company Sysdig.
Krebs on Security
MARCH 27, 2025
In May 2024, KrebsOnSecurity published a deep dive on Stark , which has repeatedly been used to host infrastructure for distributed denial-of-service (DDoS) attacks, phishing, malware and disinformation campaigns from Russian intelligence agencies and pro-Kremlin hacker groups.

Trend Micro
JANUARY 16, 2025
Since the end of 2024, we have been continuously monitoring large-scale DDoS attacks orchestrated by an IoT botnet exploiting vulnerable IoT devices such as wireless routers and IP cameras.

CSO Magazine
DECEMBER 13, 2022
There are several trends evident in the latest DDoS Threat Intelligence Report from NETSCOUT. These include adaptive distributed denial-of-service (DDoS), direct-path TCP-based DDoS, proliferation of botnets, sociopolitical fallout, and collateral damage. To read this article in full, please click here
Krebs on Security
MAY 23, 2024
Two weeks before Russia invaded Ukraine in February 2022, a large, mysterious new Internet hosting firm called Stark Industries Solutions materialized and quickly became the epicenter of massive distributed denial-of-service (DDoS) attacks on government and commercial targets in Ukraine and Europe. Image: SentinelOne.com.

CSO Magazine
JUNE 28, 2022
Cyberattacks on the Lithuanian government and private institutions conducted by the Russian cybercollective Killnet, and the group's possible collaboration with the Conti hacking gang, were shared on the Telegram messaging service ahead of a major DDoS attack Monday, according to cybersecurity company Flashpoint.

CSO Magazine
MAY 17, 2022
Cyber attackers launched three worldwide distributed denial-of-service (DDoS) extortion attack campaigns in 2021 – a startling new achievement carried out by a REvil copycat, Lazarus Bear Armada (LBA), and Fancy Lazarus. To read this article in full, please click here But threat actors did more than simply increase such global attacks.
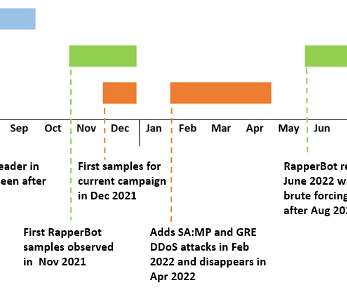
Security Affairs
NOVEMBER 16, 2022
Fortinet researchers discovered new samples of RapperBot used to build a botnet to launch Distributed DDoS attacks against game servers. Fortinet FortiGuard Labs researchers have discovered new samples of the RapperBot malware that are being used to build a DDoS botnet to target game servers. Pierluigi Paganini.

Heimadal Security
OCTOBER 12, 2021
As my colleague Cezarina explained in a previous article, a botnet is a network of infected computers or other internet-connected devices, that communicate with each other in order to perform the same malicious actions. The post DDoS Operator Arrested by the Ukrainian Police appeared first on Heimdal Security Blog.

Krebs on Security
MARCH 7, 2022
” Stern apparently believed in his crypto dreams so much that he sponsored a $100,000 article writing contest on the Russian language cybercrime forum Exploit, asking interested applicants to put forth various ideas for crypto platforms. “Cryptocurrency article contest! . “Cryptocurrency article contest!

CSO Magazine
AUGUST 31, 2021
Yes, the first half of 2021 saw yet another record broken when it comes to global distributed denial-of-service (DDoS) attacks—but that’s not the full picture. After an astonishingly active first quarter of DDoS attack activity, things calmed down a bit for the second quarter of 2021. Unfortunately, “calmed down” is a relative term.

Heimadal Security
JUNE 21, 2022
Mounting Denial-of-Service (DDOS) attacks is undoubtedly an arcane tactic considering the evolutionary timeline of cyber-defenses, but ‘going old-school’ does pay off when one’s engaged in a fast-paced, counter-for-threat trade-off. In this article, we’re […].
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content